[BlackHat USA tool] chocoProxy: aid in reverse engineering Windows applications’ network traffic
chocoProxy
chocoProxy is a Windows tool intended to aid in reverse engineering Windows applications’ network traffic. The proxy works by hooking the sending and receiving Windows APIs after being injected into a target process. The traffic can be modified to arbitrary values to observe the behavior of an application when provided with unexpected input. The tool is meant to expedite the discovery and development of memory corruption exploits that occur in the implementation of complex and custom network protocols. chocoProxy takes away the necessity for exploit developers to reverse engineer a network protocol by utilizing the existing client/server functionality in the target.
 Use
Use
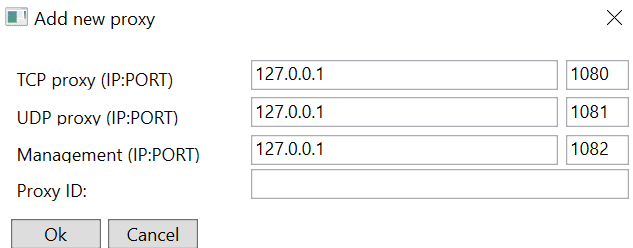
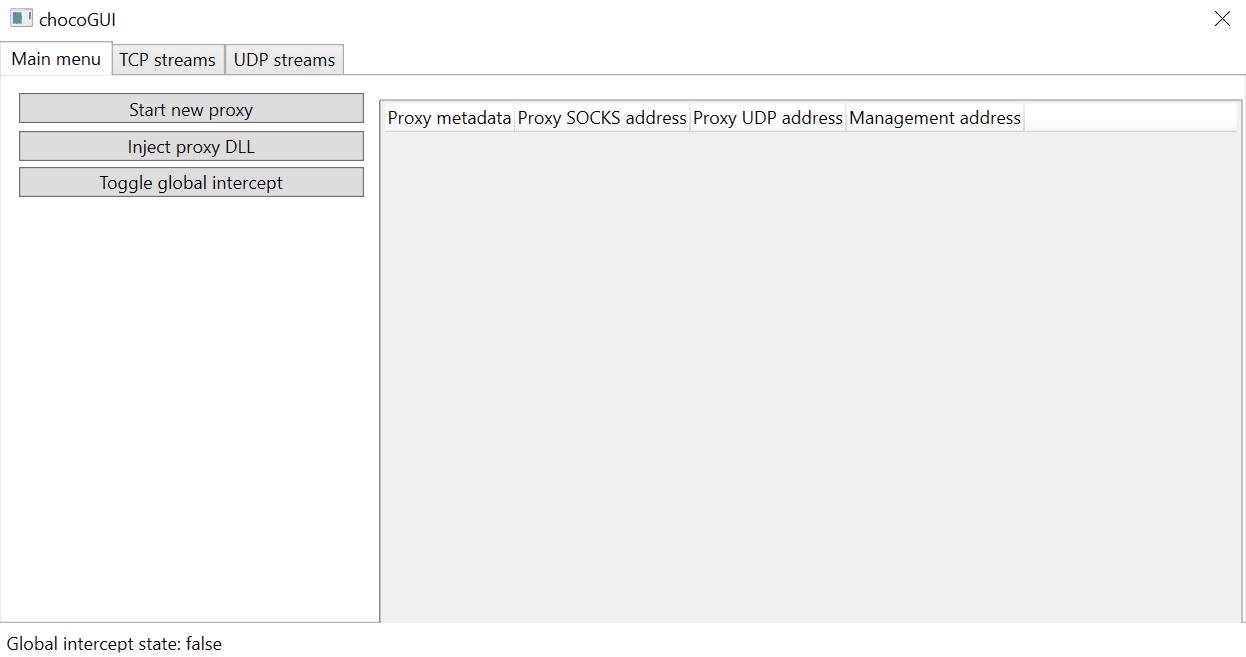
The tool can be used for both TCP and UDP protocols. By default, it runs a TCP listener on port 1080, a UDP listener on port 1081 and a second TCP listener on port 1082 used for internal communication between the proxy component and the GUI. A new proxy can be started in the main menu via the ‘Start new proxy’ button.
If the specified TCP/UDP ports are available, the proxy is established and listening for connections.
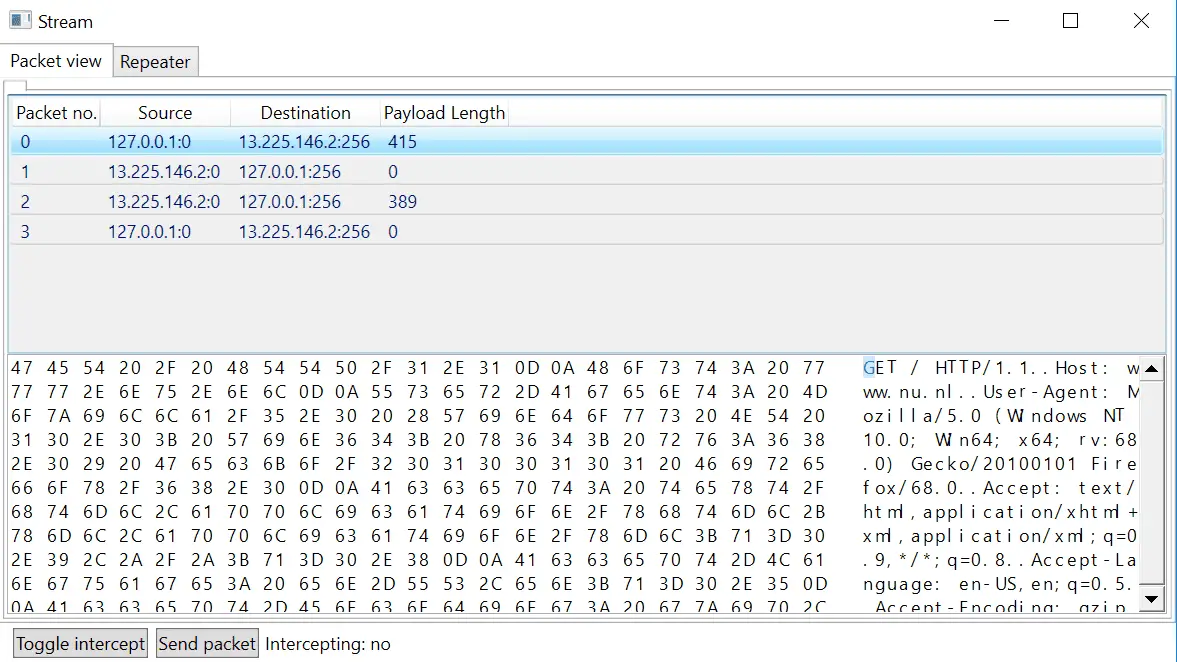
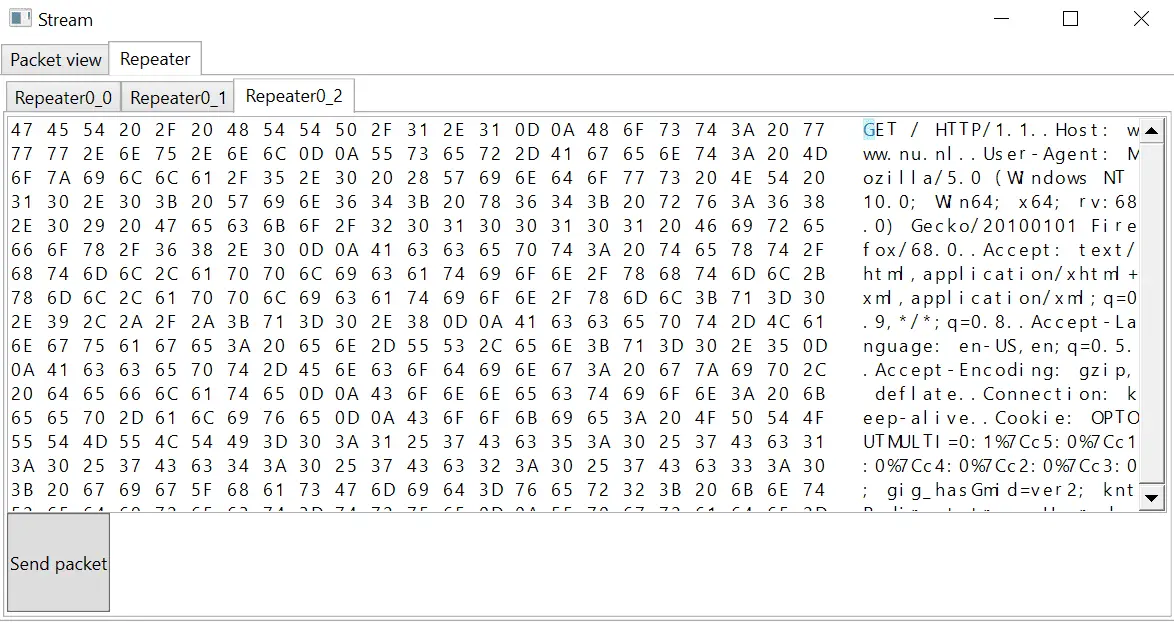
As soon as there are packets traversing the proxy, the streams are displayed in either the TCP streams or the UDP streams tab with the information identifying the streams. Right-clicking the streams enables the user to open the stream to view its contents. Opening the stream displays the packets in order as well as their contents in hex and ASCII:
The client packets can be sent to the Repeater tab by right-clicking and selecting the “Send to repeater” option. The contents of the packet can be modified by the user and sent to the server. This functionality does not yet work for UDP packets.
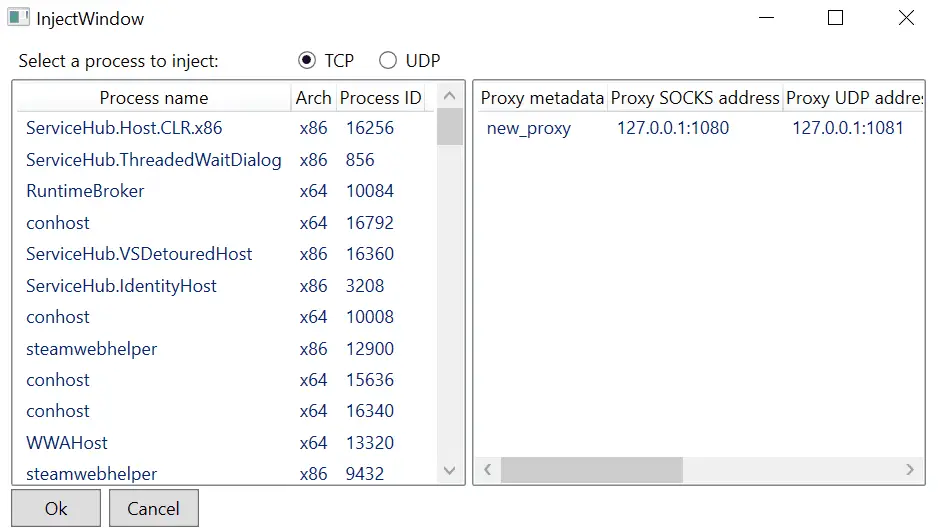
To use the proxy for proxy-unaware clients, it is necessary to inject a DLL into the target process to hook the sending/receiving functions. This can be done via the ‘Inject proxy DLL’ button via the Main menu and selecting a process to inject, the proxy listener, and whether it’s TCP or UDP traffic. Both TCP and UDP support is currently in beta!
Once the DLL is injected, the corresponding protocol data is sent to the proxy for modification.
In terms of intercept capabilities, the proxy supports two modes: – Local stream intercept. – Global intercept.
The local interception can be applied on an already established stream by opening the stream and clicking the ‘Toggle intercept’ button in the lower-left corner. When the intercept is on, every new packet in the selected stream will first be sent to the user for modification. The packet can then be sent to the server via the ‘Send packet’ button.
The global intercept can be enabled via the “Toggle global intercept” button from the Main menu. The global intercept allows the interception of streams before they’re established and is enabled for all present and upcoming connections. Intercepted packets are displayed in the correspondent UDP or TCP tab under a new entry:
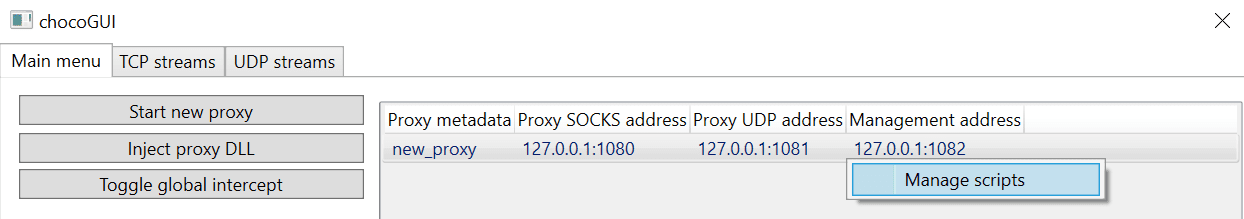
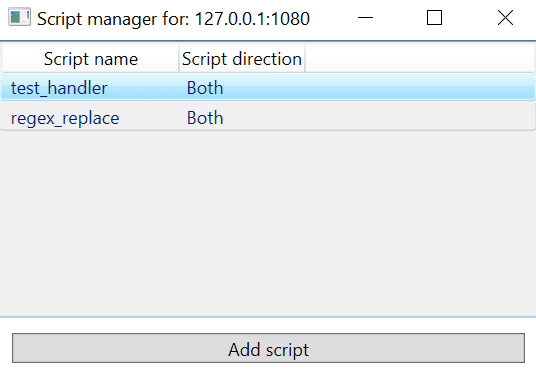
The proxy supports the use of Python script for processing and modifying packets automatically. By right-clicking on the proxy entry in the Main window and selecting the Manage scripts option, a new Script manager window is opened.
In the new Script manager window, new Python scripts can be added and removed. The proxy will execute the scripts in the specified order, returning the bytes to be sent to the server.
Download
Copyright (C) 2019 rveldhoven
 Use
Use