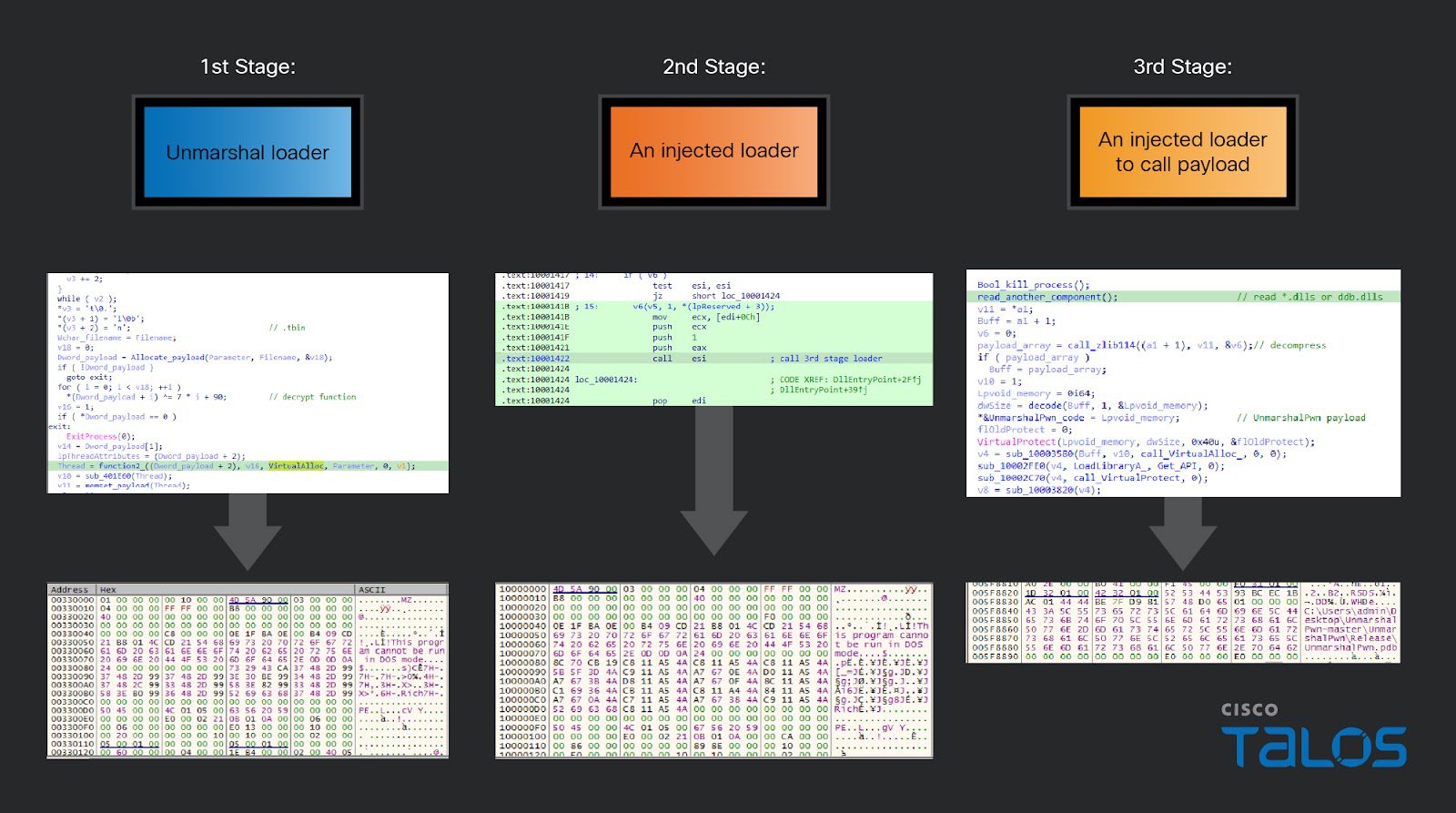
UnmarshalPwn malware
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical warning about a Microsoft COM for Windows vulnerability, CVE-2018-0824, which is currently being exploited by malicious actors. This vulnerability allows remote code execution, potentially granting attackers significant control over compromised systems.
What is the Vulnerability?
CVE-2018-0824 resides in Microsoft COM for Windows, a core component of the operating system. The flaw stems from its inability to properly handle serialized objects, making it susceptible to specially crafted files or scripts. Attackers can leverage this vulnerability through various means, such as email attachments or compromised websites, tricking users into opening malicious files.
Exploitation and Impact
While CISA has not directly linked this vulnerability to ransomware campaigns, Cisco’s Talos security team has reported that the notorious APT41 hacking group has been exploiting CVE-2018-0824 for local privilege escalation. APT41’s sophisticated “UnmarshalPwn” malware utilizes this vulnerability to gain deeper access and control within compromised systems.
Mitigation and Response
CISA strongly urges all federal agencies to patch their systems and apply the latest security updates by August 26, 2024. Given the active exploitation of this vulnerability, timely patching is crucial to mitigate the risk of compromise.
Security experts recommend the following steps for organizations and individuals to safeguard their systems:
- Apply Patches: Ensure that all systems are updated with the latest security patches from Microsoft.
- Email Security: Implement robust email security measures to detect and block malicious attachments.
- Web Filtering: Use web filtering solutions to prevent access to known malicious sites.
- User Training: Educate users about the dangers of phishing attacks and the importance of not opening unsolicited files or clicking on suspicious links.
- Intrusion Detection Systems (IDS): Deploy IDS to detect and respond to unusual activities on the network.
Related Posts:
- Chinese APT41 Group Breaches Taiwanese Research Institute
- CISA Adds 12 New Known Actively Exploited Vulnerabilities to its Catalog
- Google Project Zero team found a Windows zero-day vulnerability
- “The Com” Phishing Attacks Escalate, Targeting Businesses with Fake Login Pages