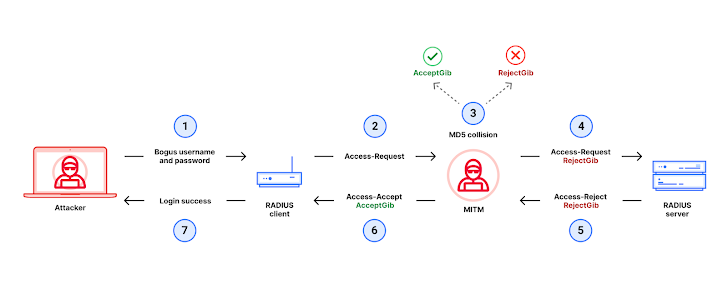
Cisco has issued a security advisory for a critical vulnerability (CVE-2024-3596) in the RADIUS protocol, a widely used authentication and authorization framework for network access. This vulnerability could allow an attacker to bypass multi-factor authentication (MFA) and gain unauthorized access to networks.
The vulnerability stems from a flaw in the MD5 Response Authenticator signature used in the RADIUS protocol. An attacker with network access can exploit this flaw to forge RADIUS responses, effectively bypassing authentication measures. This could lead to unauthorized access to sensitive network resources.
Cisco has confirmed that a wide range of its products are affected by this vulnerability, including:
- Network and Content Security Devices:
- Adaptive Security Appliance (ASA) (CSCwk71992)
- Firepower Device Manager (FDM) (CSCwk69454)
- Firepower Management Center (FMC) Software (CSCwk71817)
- Firepower Threat Defense (FTD) Software (CSCwk67902)
- Identity Services Engine (ISE) (CSCwk67747)
- Secure Email Gateway (CSCwk70832)
- Secure Web Appliance (CSCwk70834)
- Network Management and Provisioning:
- Application Policy Infrastructure Controller (APIC) (CSCwk70836)
- Crosswork Change Automation (CSCwk70850)
- Nexus Dashboard (CSCwk70840)
- Routing and Switching – Enterprise and Service Provider:
- ASR 5000 Series Routers (CSCwk70831)
- Catalyst SD-WAN Controller (CSCwk70854)
- Unified Computing:
- UCS Central Software (CSCwk71967)
- UCS Manager (CSCwk70842)
Cisco has confirmed that the following products are not affected by this vulnerability:
- Nexus Dashboard Insights
- Secure Workload
- Firepower 4100/9300 FXOS Firepower Chassis Manager
- Secure Malware Analytics Appliance
- Umbrella Active Directory (AD) Connector
- Cisco Evolved Programmable Network Manager (EPNM)
- DNA Spaces Connector
- Policy Suite
- Ultra Cloud Core – Policy Control Function
- UCS B-Series Blade Servers
- Various Aironet and Catalyst series access points and wireless LAN controllers
The Cisco Product Security Incident Response Team (PSIRT) is aware of proof-of-concept exploit code available for this vulnerability but has not detected any malicious exploitation in the wild.
Cisco strongly recommends that customers apply the available patches for their affected products as soon as possible. There are no workarounds available for this vulnerability.
Related Posts:
- BlastRADIUS Vulnerability (CVE-2024-3596): Flaw in RADIUS Protocol Exposes Networks to Attack
- Cisco releases patch to fix three high security bugs
- Hackers use Cisco Router flaws to attack Iran, 3,500 routers hacked