Cisco IOS XE implant scanning & detection

Cisco IOS XE implant scanning
This repository contains information regarding post-exploitation activities linked to the Cisco IOS XE Software Web Management User Interface mass exploitations. Cisco Talos published a fingerprint that could check if the implant was active on Cisco IOS XE devices. For reference:
curl -k -X POST “https://DEVICEIP/webui/logoutconfirm.html?logon_hash=1“
Upgraded Implant
Investigated network traffic to a compromised device has shown that the threat actor has upgraded the implant to do an extra header check. Thus, for a lot of devices, the implant is still active, but now only responds if the correct Authorization HTTP header is set.
An alternate method for Cisco IOS XE implant scanning
We took another look at the initial blog post by Cisco Talos and noticed an extra location check in the implant code:
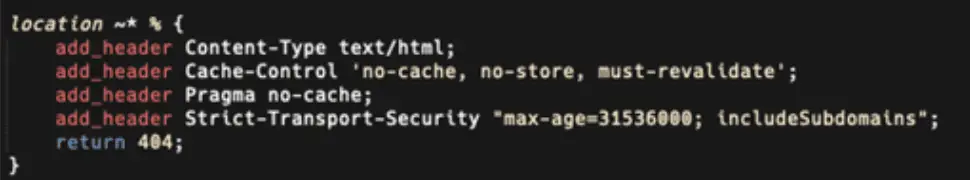
Based on the above screenshot of the implant code shared by Cisco Talos we found another method that can be used to fingerprint the presence of the implant.
curl -k “https://DEVICEIP/%25“
If the implant is not present, you will get a different response. For example:
Script to check for compromise
We created a small script that checks for compromise using the above fingerprinting method. A script can be found here:
Example usage:
Download
git clone https://github.com/fox-it/cisco-ios-xe-implant-detection.git
Copyright (C) 2023 fox-it
Source: https://github.com/fox-it/





