The release of public PoC exploit code targeting a maximum severity zero-day flaw in Cisco IOS XE (CVE-2023-20198) has dramatically amplified the risk landscape for countless organizations worldwide. Previously, only a few advanced attackers knew how to exploit this bug. Now, hackers across the entire spectrum of skill levels can gain full control over vulnerable routers and switches with shocking ease. Businesses, infrastructure providers, and government entities face an escalating wave of attacks.
Background on the Vulnerability
In late October 2023, Cisco alerted administrators about the zero-day within its IOS XE software, specifically targeting devices with an enabled Web User Interface (Web UI) and active HTTP or HTTPS server features. This critical security loophole was actively exploited, allowing unauthenticated attackers to seize complete control of the routers and switches.
Cisco first became aware of the exploitative attacks on September 28, following reports from their Technical Assistance Center (TAC) about unusual activity on customer devices. This led to the discovery that the vulnerability permitted attackers to create high-level user accounts on the affected devices, thereby commandeering the entire system.
How the Attack Works
Researchers from Horizon3.ai provided an in-depth look at the exploitation process. They revealed that attackers could manipulate HTTP requests to the Web Services Management Agent (WSMA) service in iosd—a pivotal binary in Cisco’s software suite. This manipulation involved generating a configuration file for OpenResty, which is susceptible under CVE-2023-20198.
Through SOAP requests to WSMA, attackers could execute commands granting them access to the configuration features, enabling them to create a user with the highest privileges (level 15). This breach effectively hands full control over to the attackers, allowing them to install malicious implants directly onto the devices without exploiting further vulnerabilities.
Recent Developments and Cisco’s Response

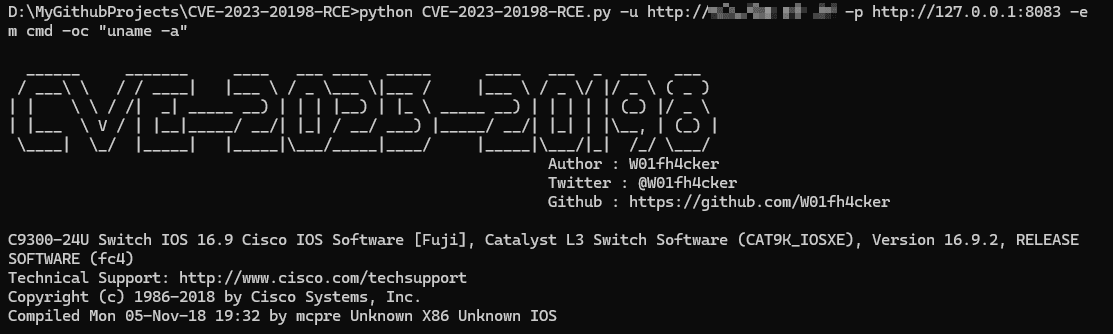
Today, the situation escalated when a security researcher known as W01fh4cker released a proof-of-concept (PoC) exploit code for CVE-2023-20198, making the exploit widely accessible and increasing the urgency for defensive measures.
Recommendations and Conclusion
Responding swiftly, Cisco updated its security bulletin on October 30, 2023, providing necessary patches for IOS XE to mitigate the vulnerability. The company has urged all users with potentially vulnerable configurations to update their devices immediately to prevent exploitation.
Organizations using Cisco IOS XE are strongly advised to review their device configurations and disable the Web UI feature if it is not in use. Additionally, keeping the firmware of network devices updated is crucial in defending against such severe vulnerabilities.