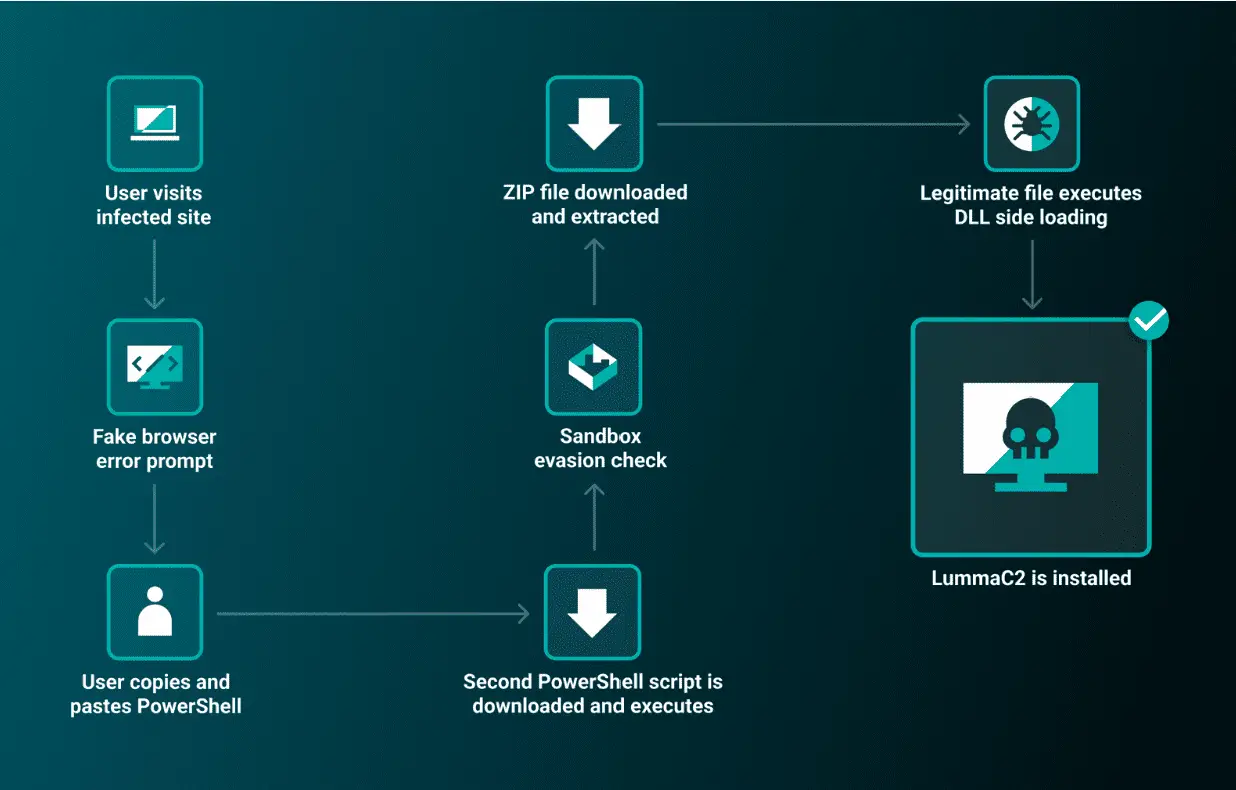
Attack flow
Recently, the ReliaQuest Threat Research Team has unveiled a new execution technique used in the ongoing ClearFake campaign. This JavaScript framework, previously known for its drive-by downloads and fake browser update schemes, has now adopted a novel method to trick users into manually copying and executing malicious code in PowerShell. This technique is designed to bypass traditional security defenses, making it a significant concern for cybersecurity professionals.
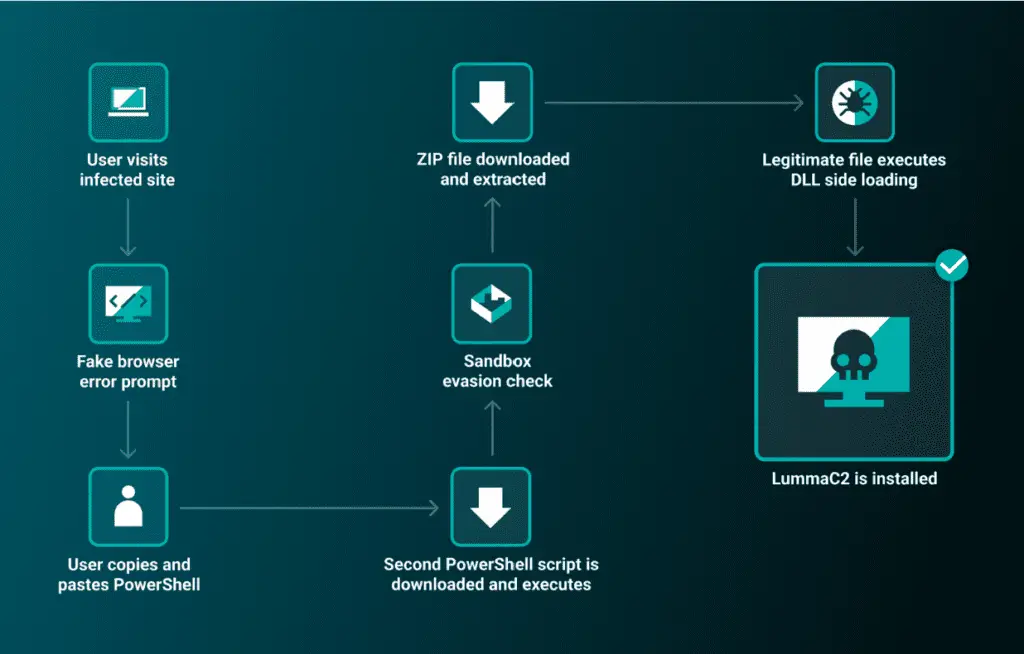
In May 2024, ReliaQuest discovered that ClearFake had evolved its tactics. Unlike the typical drive-by downloads, the adversary now lures users into manually executing PowerShell commands. This change is significant because it allows the malicious code to evade detection by security tools that monitor automated script execution and file downloads. By involving the user in the execution process, the campaign reduces the likelihood of being flagged by security systems.
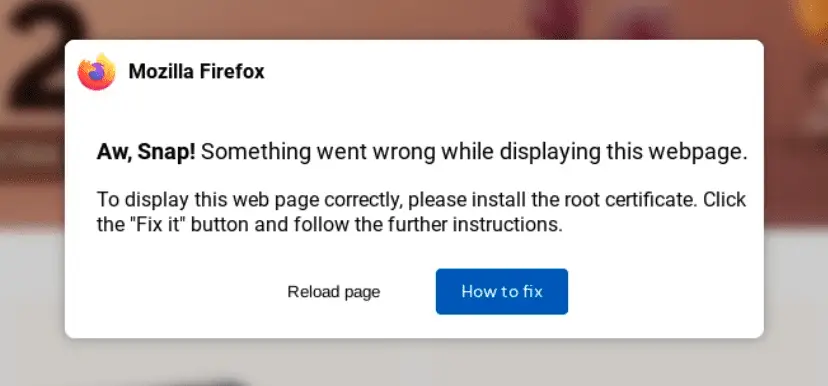
The attack begins with users encountering a fake browser error prompt on a compromised website. The prompt instructs them to install a “root certificate” by clicking a “Fix it” button. Upon clicking, users are presented with obfuscated PowerShell code and guided to copy and paste it into a PowerShell terminal. Once executed, the code initiates a multi-stage infection process, ultimately leading to the installation of LummaC2.
The user is then guided to open a PowerShell terminal and paste the copied code, which executes several malicious actions:
- Executes
ipconfig /flushdnsto clear the DNS cache. - Displays a message box stating: “The operation completed successfully, please reload the page.”
- Assigns and uses specific URLs and user agents to fetch further malicious content.
- Executes the retrieved content using
Invoke-Expression. - Clears the PowerShell screen and user clipboard to hide evidence.
Once the initial PowerShell script is executed, it leads to a multi-stage malware infection process designed to evade sandbox environments. The script checks the infected device’s CPU temperature, terminating if it detects a virtual machine environment. If a physical device is confirmed, the script downloads a ZIP file containing both legitimate and malicious components. This includes “MediaInfo.exe” and the malicious DLL “MediaInfo_i386.dll,” which are used to install the LummaC2 infostealer malware via DLL sideloading.
While this technique may have a lower success rate due to its reliance on user interaction, it poses a significant threat as it can bypass security controls and lead to severe consequences. ReliaQuest observed two case studies highlighting the effectiveness of this new approach. In one case, the attack was partially successful, with technical controls preventing the complete infection chain. In the other case, the attack successfully deployed LummaC2, emphasizing the need for enhanced security measures.
To mitigate this emerging threat, organizations are advised to educate users about the risks of copying and pasting code from untrusted sources, restrict PowerShell usage, and implement robust network security and endpoint protection solutions.