Cloak v2.8 releases: evade deep-packet-inspection based censorship
Cloak
Cloak is a pluggable transport that works alongside traditional proxy tools like OpenVPN to evade deep-packet-inspection-based censorship.

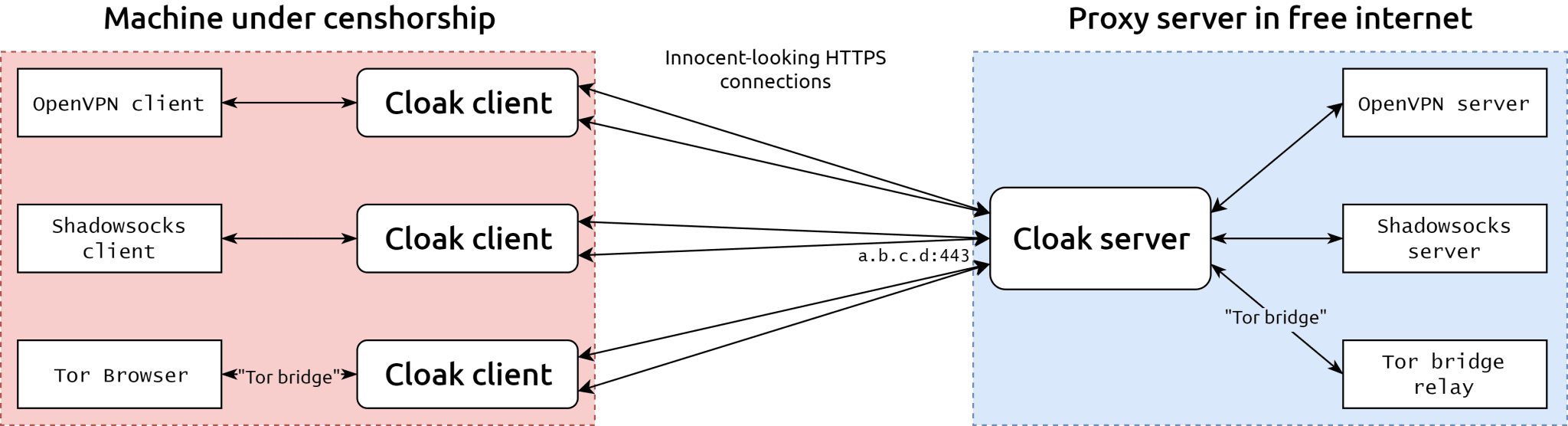
Cloak is not a standalone proxy program. Rather, it works by masquerading proxy tool’s traffic as normal web browsing traffic. In contrast to traditional tools which have very prominent traffic “fingerprints”, it’s very difficult to precisely target Cloak with little false positives. This increases the collateral damage to censorship actions as attempts to block Cloak could also damage services the censor state relies on.

To a third-party observer, a host running Cloak server is indistinguishable from an innocent web server. Both while passively observing traffic flow to and from the server, as well as while actively probing the behaviours of a Cloak server. This is achieved through the use of a series of cryptographic stegnatography techniques.
Since Cloak is transparent, it can be used in conjunction with any proxy software that tunnels traffic through TCP or UDP, such as Shadowsocks, OpenVPN, and Tor. Multiple proxy servers can be running on the same server host machine and Cloak server will act as a reverse proxy, bridging clients with their desired proxy end.
Cloak multiplexes traffic through multiple underlying TCP connections which reduces head-of-line blocking and eliminates TCP handshake overhead. This also makes the traffic pattern more similar to real websites.
Cloak provides multi-user support, allowing multiple clients to connect to the proxy server on the same port (443 by default). It also provides traffic management features such as usage credit and bandwidth control. This allows a proxy server to serve multiple users even if the underlying proxy software wasn’t designed for multiple users
Cloak has two modes of Transport: direct and CDN. Clients can either connect to the host running Cloak server directly, or it can instead connect to a CDN edge server, which may be used by many other websites as well, thus further increasing the collateral damage to censorship.
Changelog v2.8
- Use https://github.com/refraction-networking/utls to produce ClientHello fingerprints.
Install & Use
Copyright (C) 2022 cbeuw