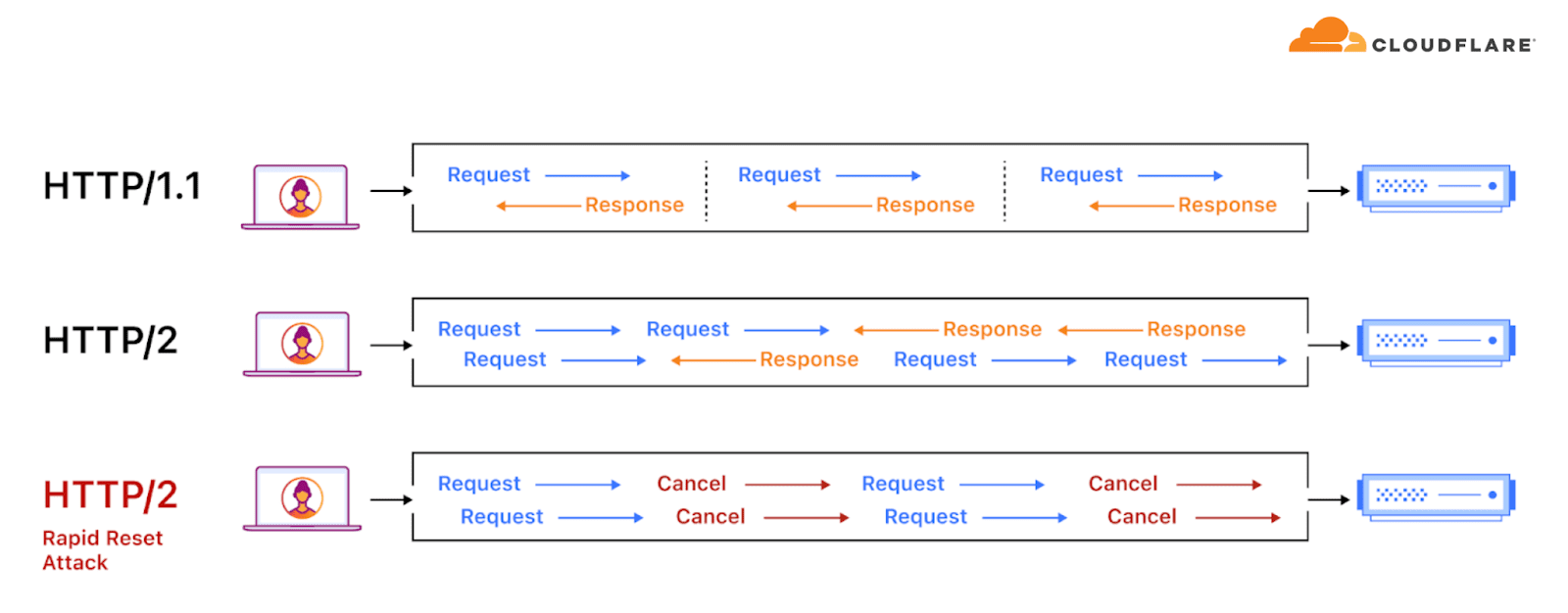
Illustration of an HTTP/2 Rapid Reset DDoS attack | Image: CloudFlare
The recent unveiling of the HTTP/2 Rapid Reset (CVE-2023-44487) vulnerability earlier this month followed a comprehensive industry-wide disclosure, which delved into an orchestrated DDoS assault against providers such as Amazon Web Services (AWS) by unidentified actors leveraging this flaw.
Cloudflare indicated on Thursday that it had mitigated thousands of volumetric HTTP Distributed Denial-of-Service (DDoS) attacks that exploited the recently disclosed vulnerability known as HTTP/2 Rapid Reset. Out of these, 89 instances surpassed a staggering 100 million requests per second (RPS).

In a report, this internet infrastructure and security firm stated, “The campaign contributed to an overall increase of 65% in HTTP DDoS attack traffic in Q3 compared to the previous quarter. Similarly, L3/4 DDoS attacks also increased by 14% alongside numerous attacks in the terabit-per-second range — the largest peaked at 2.6 Tbps.”
The total number of HTTP DDoS attack requests for this quarter skyrocketed to 89 trillion, surpassing Q2 2023’s 54 trillion and Q1 2023’s 47 trillion. Q4 2022 witnessed an attack request count of 65 trillion.
Fastly, in a disclosure of its own on Wednesday, noted that it had countered a similar attack, peaking at approximately 250 million RPS and lasting roughly three minutes.
On RPS DDoS attacks, Cloudflare remarked, “Botnets that leverage cloud computing platforms and exploit HTTP/2 are able to generate up to x5,000 more force per botnet node. This allowed them to launch hyper-volumetric DDoS attacks with a small botnet ranging 5-20 thousand nodes alone.”
The main targets of HTTP DDoS attacks encompass sectors such as gaming, IT, cryptocurrency, computer software, and telecommunications.
The firm observed, “For the second consecutive quarter, DNS-based DDoS attacks were the most common. Almost 47% of all attacks were DNS-based. This represents a 44% increase compared to the previous quarter. SYN floods remain in second place, followed by RST floods, UDP floods, and Mirai attacks.”
A notable shift was the decline in DDoS ransom attacks, with Cloudflare suggesting this was due to threat actors realizing organizations are reluctant to pay ransom.
This disclosure coincides with a surge in internet traffic fluctuations and DDoS attacks in the aftermath of the conflict between Israel and Hamas. Cloudflare thwarted several attempted attacks targeting Israeli and Palestinian websites.