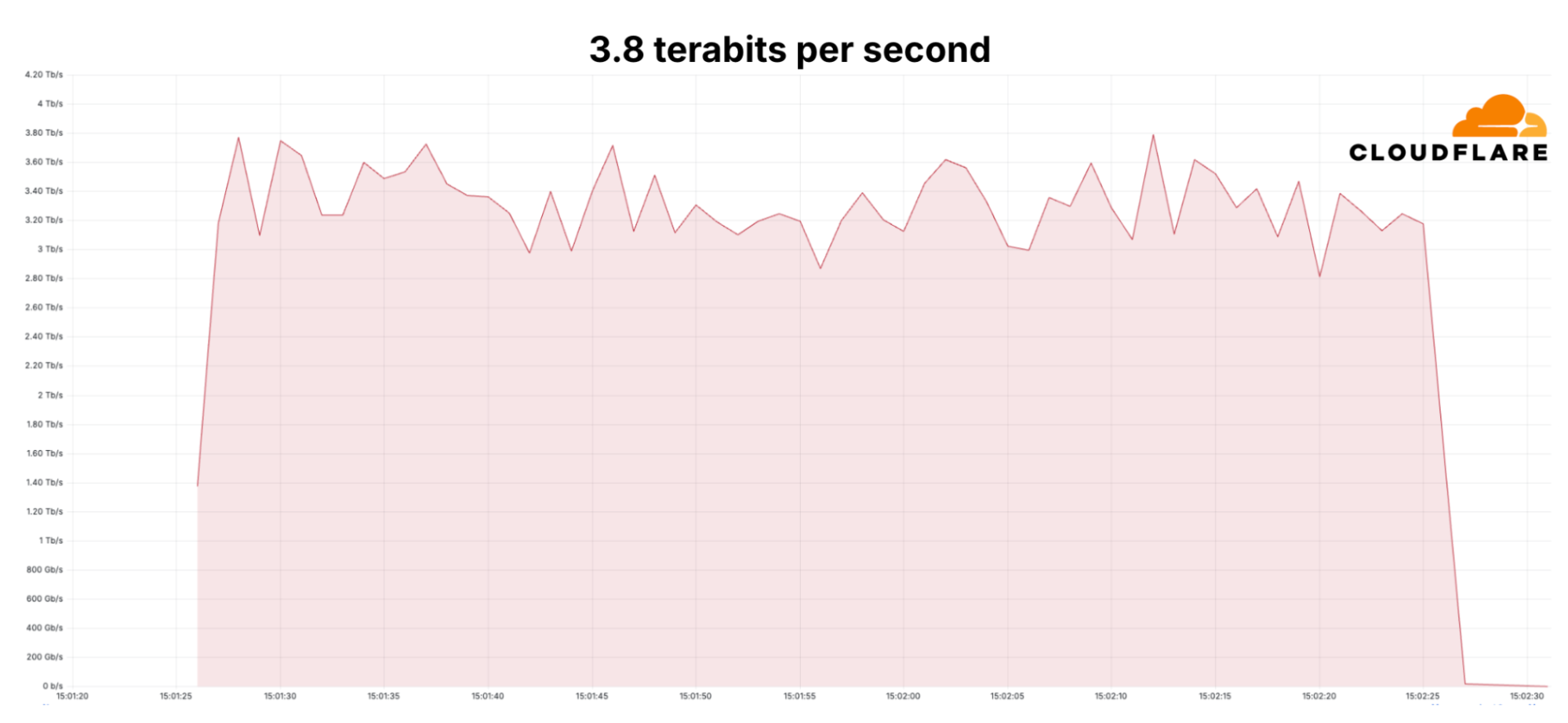
A mitigated 3.8 Terabits per second DDoS attack that lasted 65 seconds | Image: Cloudflare
In a world where cyberattacks grow in size and sophistication, Cloudflare has once again proven the power of its autonomous defenses by successfully mitigating the largest Distributed Denial of Service (DDoS) attack ever recorded—peaking at an unprecedented 3.8 terabits per second (Tbps).
Since early September, Cloudflare’s DDoS protection systems have been combating a relentless wave of hyper-volumetric Layer 3/4 DDoS attacks targeting various industries, including financial services and telecommunications. The largest attack in this campaign clocked in at 3.8 Tbps, marking the highest disclosed DDoS volume ever recorded by any organization.
These attacks, often exceeding 2 billion packets per second (Bpps) and 3 Tbps in size, leveraged compromised devices worldwide—ranging from routers to web servers and DVRs—flooding Cloudflare’s network with massive volumes of data in an attempt to overwhelm services. Despite the scale and intensity, Cloudflare’s defenses mitigated these attacks autonomously, ensuring zero downtime for its customers.
What sets this event apart is Cloudflare’s fully autonomous mitigation response. By leveraging its global anycast network, Cloudflare was able to absorb and distribute attack traffic across multiple data centers worldwide, preventing any single location from being overwhelmed. Attack traffic originating from infected devices across various regions, including Vietnam, Russia, Brazil, Spain, and the U.S., was automatically routed to the nearest Cloudflare data center, where the company’s advanced DDoS protection systems were already in place.
Cloudflare’s detection system uses real-time signature generation to pinpoint suspicious traffic patterns, allowing it to surgically drop malicious traffic while ensuring legitimate users remain unaffected. These signatures are distributed globally across Cloudflare’s servers, ensuring fast and precise mitigation on a network-wide scale.
Cloudflare’s success in mitigating this record-setting attack lies in the architecture of its global network. With over 100 Tbps of network capacity, Cloudflare can handle even the most monstrous attacks without breaking a sweat. Its infrastructure ensures that attack traffic is not only distributed geographically but also across multiple servers within each data center, preventing bottlenecks and maintaining network performance.
For high-bandwidth attacks, such as this 3.8 Tbps DDoS, Cloudflare’s network employs sophisticated techniques to inspect and drop harmful packets at wire speed, ensuring the attack traffic is blocked before it can do any damage. This level of defense is powered by Cloudflare’s use of the eXpress Data Path (XDP) and extended Berkeley Packet Filters (eBPF), which operate directly within the network interface card (NIC) to process packets efficiently and autonomously.
While Cloudflare customers using its HTTP reverse proxy services, Magic Transit, and Spectrum are protected by default, other internet properties may not be so lucky. Many on-premise and cloud-based DDoS defenses simply do not have the capacity to absorb attacks of this magnitude. Without the global reach and intelligent systems required to handle these extreme volumes, unprotected or inadequately protected services could easily be taken offline by similar attacks.
The campaign targeted bandwidth saturation and resource exhaustion across multiple sectors. Leveraging UDP-based traffic, the attackers focused on exhausting both CPU cycles and network bandwidth to disrupt services. The attack was powered by compromised devices, including home routers exploiting a recently discovered vulnerability (CVE 9.8), demonstrating how attackers are harnessing everyday devices to generate massive attack volumes.
Related Posts:
- Cloudflare successfully blocked DDoS attacks up to 2 Tbps
- Minecraft Server Hit with Record-Breaking 3.15 Billion Packet Rate DDoS Attack
- Proposed US Ban on Chinese Tech Impacts Autonomous Vehicles