Cobalt Strike User-Defined Reflective Loader
Cobalt Strike User-Defined Reflective Loader written in Assembly & C for advanced evasion capabilities.
- Based on Stephen Fewer’s incredible Reflective Loader project
- Created while working through Renz0h’s Reflective DLL videos from the Sektor7 Malware Developer Intermediate (MDI) Course
Initial Project Goals
- Learn how Reflective Loader works.
- Write a Reflective Loader in Assembly.
- Compatible with Cobalt Strike.
- Cross compile from macOS/Linux.
- Implement Inline-Assembly into a C project.
Future Project Goals
- Use the initial project as a template for more advanced evasion techniques leveraging the flexibility of Assembly.
- Implement Cobalt Strike options such as no RWX, stompPE, module stomping, changing the MZ header, etc.
- Write a decent Aggressor script.
- Support x86.
- Have different versions of the reflective loader to choose from.
- Implement HellsGate/HalosGate for the initial calls that reflective loader uses (pNtFlushInstructionCache, VirtualAlloc, GetProcAddress, LoadLibraryA, etc).
- Optimize the assembly code.
- Hash/obfuscate strings.
- Some kind of template language overlay that can modify/randomize the registers/methods.
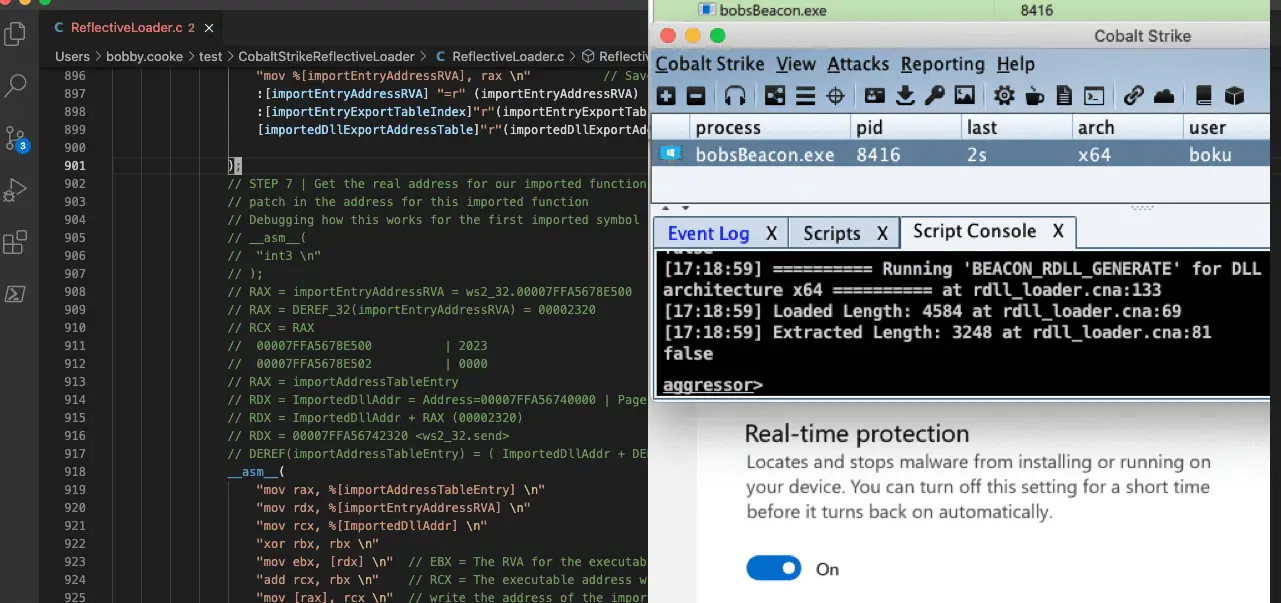
Usage
- Start your Cobalt Strike Team Server with or without a profile
- At the moment I’ve only tested without a profile and with a few profiles generated from Tylous’s epic SourcePoint project
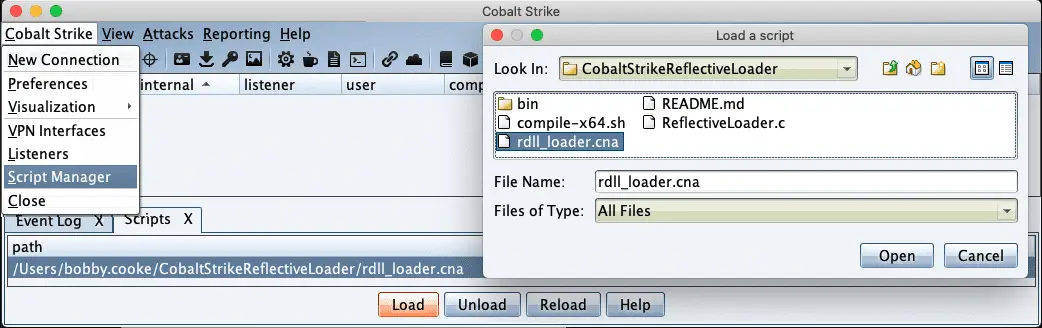
- Go to your Cobalt Strike GUI and import the rdll_loader.cna Agressor script
- Generate your x64 payload (Attacks -> Packages -> Windows Executable (S))
- Use the Script Console to make sure that the beacon created successfully with this User-Defined Reflective Loader
Change log v1.0
Massive update from @s4ntiago_p! New 32bit loader with WOW64 support, 32bit Halos&HellsGate, code optimizations & bug fixes!