CobaltStrikeScan
Scan files or process memory for Cobalt Strike beacons and parse their configuration.
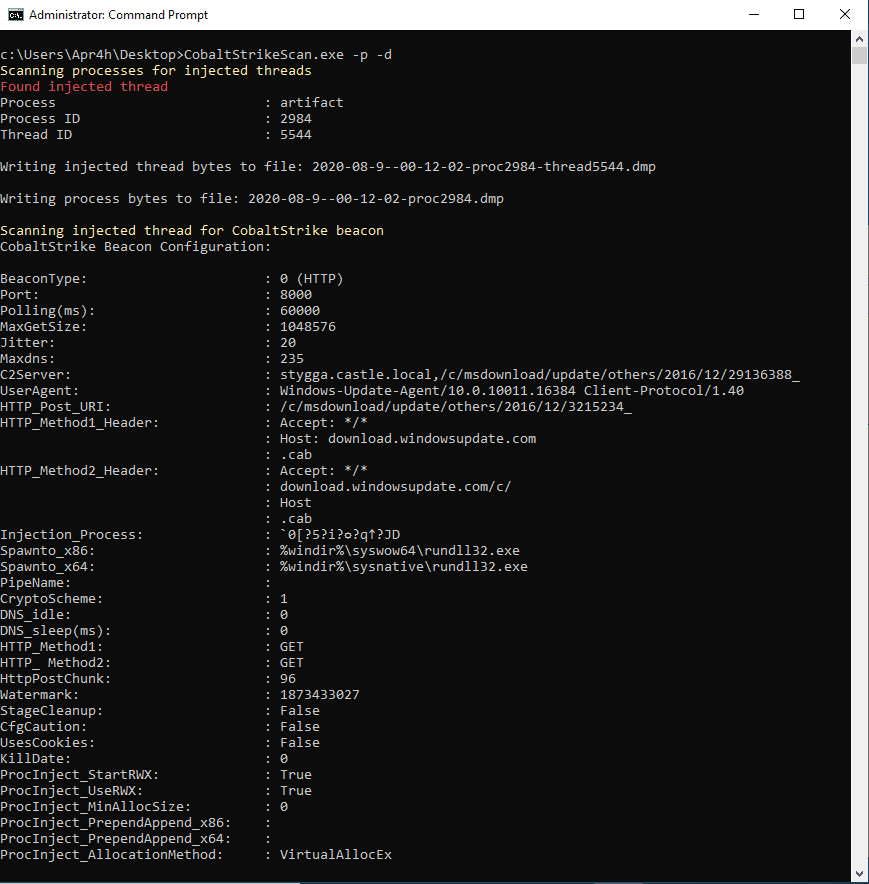
CobaltStrikeScan scans Windows process memory for evidence of DLL injection (classic or reflective injection) and performs a YARA scan on the target process’ memory for Cobalt Strike v3 and v4 beacon signatures.
Alternatively, it can perform the same YARA scan on a file supplied by an absolute or relative path as a command-line argument.
If a Cobalt Strike beacon is detected in the file or process, the beacon’s configuration will be parsed and displayed to the console.
Changelog v1.1.2
Bug Fixes
- Fixed bug preventing some beacon configs being output to console
- Modified YARA rule to improve detection of non-encoded beacon config
Install
Requirements
- 64-bit Windows OS
- .NET Framework 4.6
- Administrator or SeDebugPrivilege is required to scan process memory for injected threads
Cloning this repo
CobaltStrikeScan contains GetInjectedThreads as a submodule.
git clone --recursive https://github.com/Apr4h/CobaltStrikeScan.git
Use
Source: https://github.com/Apr4h/