CoffeeShot: Avoid Detection with Memory Injection
CoffeeShot: Avoid Detection with Memory Injection
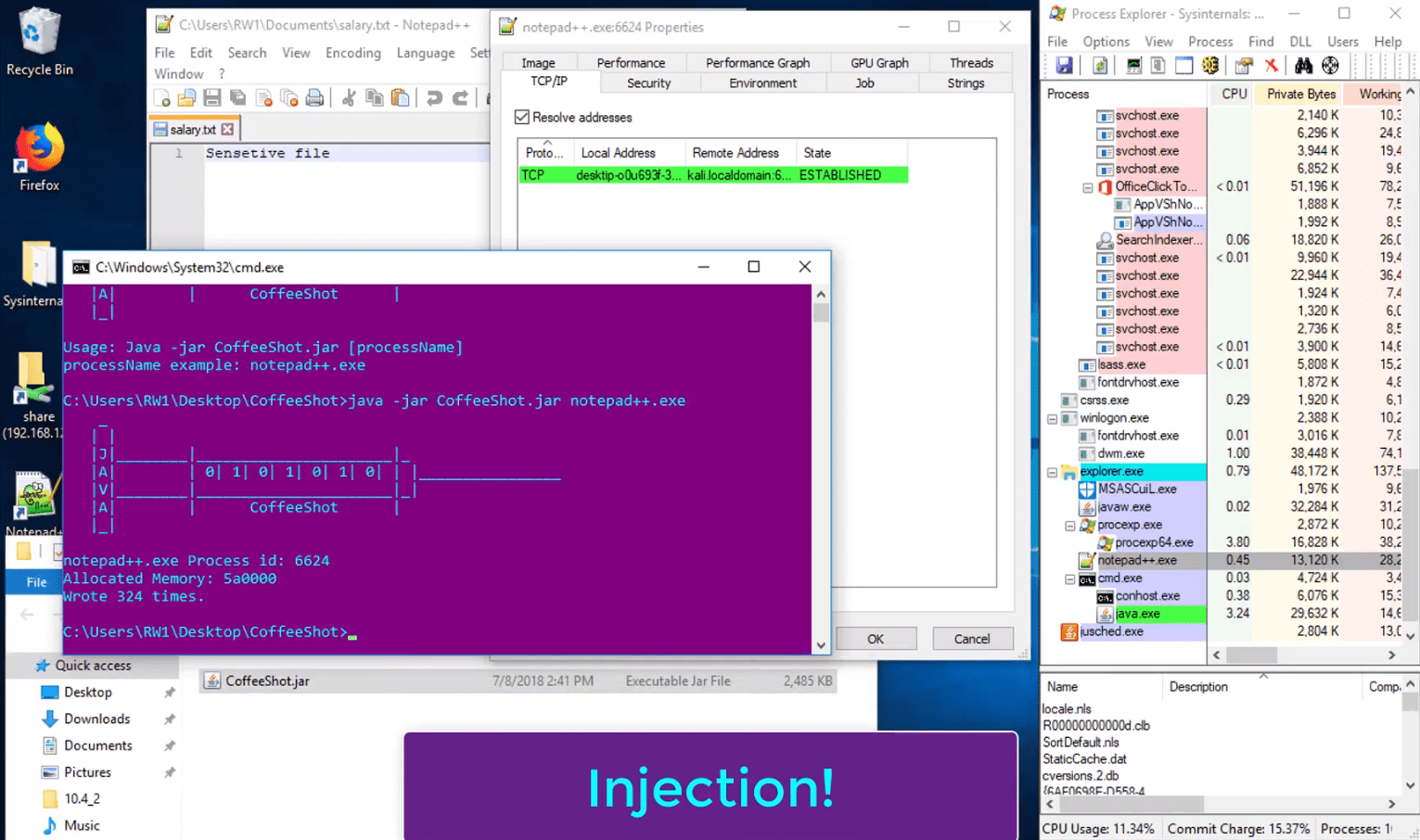
CoffeeShot is an evasion framework that injects payload from Java-based programs into designated processes on Microsoft Windows.
It assists blue team members in assessing the effectiveness of their anti-malware measures against malicious software written in Java. Red team members and pen testers can also use CoffeeShot to bypass the target’s security controls.
It utilizes JNA (Java Native Access) to inject payload from Java-based programs into designated processes on Microsoft Windows.
The memory injection methods that CoffeeShot employs are straightforward and are well-known in the context of traditional, compiled executables. The effectiveness of these techniques at evading AV when they’re implemented in Java highlights the brittle nature even by modern antivirus tools.
Prerequisites:
- Eclipse (or any other IDE that supports Java)
- Java Native Access
- Kali Linux with Metasploit
Getting Started
- Clone the project.
git clone https://github.com/MinervaLabsResearch/CoffeeShot.git - Import to Eclipse.
- Add JNA and JNA-Platform libraries.
- Insert your generated shellcode inside CoffeeShot project.
- Build the Project.
- Export to a runnable JAR file.
Setup
Add JNA and JNA-Platform libraries
- Start Eclipse
- In the project explorer, right-click on CoffeeShot folder, and select “Properties”
- Select “Java Build Path” on the left, and then the “Libraries” tab. Now, click the “Add External JARS…” button
- Locate and select “jna-4.5.0.jar” and “jna-platform-4.5.0.jar” files you downloaded from the JNA github, and then click “Open”
- Finally, click “OK” to close the dialog box. You will know that everything went ok if, when you open your project folder, you see an item called “Referenced Libraries”, and upon expanding this item, you see the packages “jna-4.5.0.jar” and “jna-platform-4.5.0.jar” listed.
Build CoffeeShot with your shellCode
Demo
Author: @3pun0x
Copyright © 2018 Minerva Labs CoffeeShot. All rights reserved.





