[Collection] Android Forensics tools

- Bandicoot

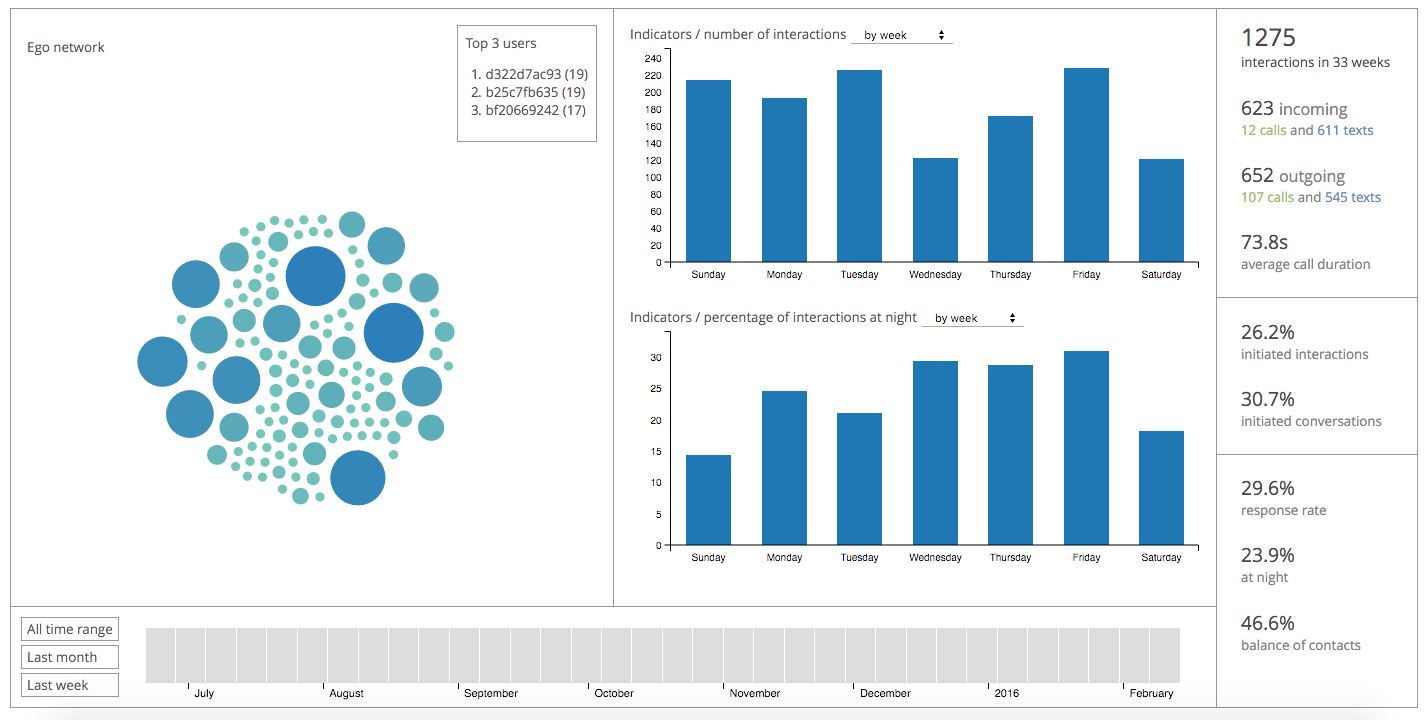
is a Python toolbox to analyze mobile phone metadata. It provides a complete, easy-to-use environment for data-scientist to analyze mobile phone metadata. With only a few lines of code, load your datasets, visualize the data, perform analyses, and export the results. - ACF
This software enables a forensic investigator to map each connection to its originating process. It doesn’t require root privileges on the system but does require adb & USB debugging.
- Android ForensicsAFLogical OSE: Open source Android Forensics app and framework Open Source Edition has been released for use by non-law enforcement personnel, Android aficionados, and forensics gurus alike. It allows an examiner to extract CallLog Calls, Contacts Phones, MMS messages, MMSParts, and SMS messages from Android devices. The full AFLogical software is available free for Law Enforcement personnel. More information is available at https://www.nowsecure.com/
- Android Data Extractor Lite
This Python script dumps all-important SQLite Databases from a connected Android smartphone to the local disk and analyzes these files in a forensically accurate workflow. If no smartphone is connected you can specify a local directory which contains the databases you want to analyze. Afterward, this script creates a clearly structured XML report. If you connect a smartphone you need a rooted and insecure kernel or a custom recovery installed on the smartphone.
- BitPim
BitPim is a program that allows you to view and manipulate data on many CDMA phones from LG, Samsung, Sanyo, and other manufacturers. This includes the PhoneBook, Calendar, WallPapers, RingTones (functionality varies by phone), and the Filesystem for most Qualcomm CDMA chipset-based phones. To see when phones will be supported, which ones are already supported and which features are supported, see online help.
- Fridump
Fridump (v0.1) is an open-source memory dumping tool, primarily aimed to penetration testers and developers. Fridump is using the Frida framework to dump accessible memory addresses from any platform supported. It can be used from a Windows, Linux, or Mac OS X system to dump the memory of an iOS, Android or Windows application.
- LiME
A Loadable Kernel Module (LKM) which allows for volatile memory acquisition from Linux and Linux-based devices, such as Android. This makes LiME unique as it is the first tool that allows for full memory captures on Android devices. It also minimizes its interaction between user and kernel space processes during acquisition, which allows it to produce memory captures that are more forensically sound than those of other tools designed for Linux memory acquisition.
- Project RetroScope
The majority of RetroScope’s code is in the dalvik/vm/zombie directory. Please be sure to read the RetroScope paper before working with RetroScope.A demo of RetroScope recovering a suspect’s chat session from a memory image of the Telegram app is available on YouTube at: https://youtu.be/bsKTmZEgxiE. - PySimReader
This is a modified version of Todd Whiteman’s PySimReader code. This modified version allows users to write out arbitrary raw SMS PDUs to a SIM card. Additionally, debugging output has been added to allow the user to view all APDUs that are sent between the SIM card and PySimReader.
- Andriller –
Android Forensic Tools
Andriller – is a software utility with a collection of forensic tools for smartphones. It performs read-only, forensically sound, non-destructive acquisition from Android devices. It has other features, such as powerful Lockscreen cracking for Pattern, PIN code, or Password; custom decoders for Apps data from Android (and some Apple iOS) databases for decoding communications. Extraction and decoders produce reports in HTML and Excel (.xlsx) formats.