“Command-Jacking”: New Supply Chain Attack Hijacks CLI Tools

In a report by Yehuda Gelb and Elad Rapoport from the Checkmarx Security Research Team, a new supply chain attack technique has been uncovered that could compromise the integrity of Command Line Interface (CLI) tools used by developers. The report highlights how attackers can leverage entry points in popular programming ecosystems to Trojanize CLI commands and execute malicious code on victims’ systems. This subtle, yet highly dangerous, method allows attackers to bypass traditional security checks and could have widespread implications for the open-source community.
The technique centers around the exploitation of “entry points,” a common feature used in packaging systems like Python’s PyPI, npm (JavaScript), Ruby Gems, and others. Entry points allow developers to expose specific functionalities as CLI commands without users needing to know the internal structure of the package.
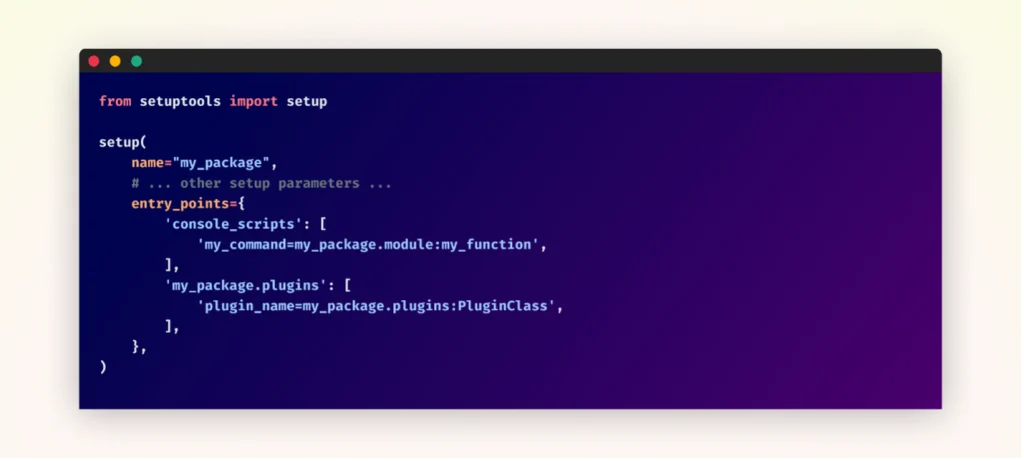
An example of how entry points might be defined in setup.py | Image: Checkmarx
“Entry points, while a powerful and useful feature for legitimate package development, can also be manipulated to deliver malicious code across multiple programming ecosystems,” the report states. While developers typically use entry points to simplify workflows, attackers can take advantage of them to run harmful code when specific commands are executed, making it an ideal technique for stealthy, long-term attacks.
One of the most concerning aspects of this technique is “command-jacking.” In this scenario, malicious packages masquerade as widely used third-party tools or even fundamental system commands. Once a user installs a compromised package, executing a seemingly legitimate command like aws or docker could actually trigger a hidden malicious script designed to steal sensitive information.
For instance, the report explains, “An attacker might create a package with a malicious ‘aws’ entry point. When unsuspecting developers who regularly use AWS services install this package and later execute the aws command, the fake ‘aws’ command could exfiltrate their AWS access keys and secrets“. The potential for such an attack in continuous integration (CI) environments, where cloud credentials are often stored for automated deployments, is alarming.
To make these attacks even more difficult to detect, the researchers explain a technique known as “command wrapping.” In this case, attackers not only run their malicious code but also execute the legitimate command afterward, making everything appear normal to the victim.
“This method of command wrapping is particularly dangerous as it executes malicious code without the user’s knowledge while maintaining the appearance of normal operation,” the report adds. By hiding their actions behind the real output of legitimate commands, attackers can maintain access for extended periods without raising suspicion.
This new attack vector is not limited to Python. The researchers confirmed that similar risks exist in npm, Ruby Gems, NuGet (.NET), Dart Pub, and Rust Crates. In each of these ecosystems, entry points could be abused in a similar fashion to Trojanize CLI commands and compromise systems.
“The open source ecosystem, due to its widespread adoption, has become a prime target for supply chain attacks. Malicious actors often exploit built-in features of open source packages to automatically distribute and execute harmful code,” the researchers note.
The discovery of this attack method underscores the need for developers and security teams to scrutinize the packages they install and review the entry points defined in their package metadata. Additionally, package managers should enhance security tools to detect suspicious entry point manipulations.
Gelb and Rapoport also call for “more comprehensive Python package security measures” and advocate to “develop comprehensive security measures that account for entry point exploitation” to better defend against this evolving threat.
For more detailed insights into this attack technique, visit the full report from the Checkmarx Security Research Team.





