
Infostealer Infection Flow
Even with strengthened password security and multi-factor authentication (MFA), hackers are finding new ways to break in. A report by CyberArk reveals a sinister trend: the rise of ‘infostealer’ malware specifically designed to steal web session cookies.
Why Cookies? It’s All About Access
Hackers covet your cookies because these tiny files are your digital passport to websites and services. With stolen cookies, they can bypass passwords and MFA, effortlessly hijacking your active sessions. It’s a simple, chillingly effective method.
How the Malware Spreads

Infostealers deploy a variety of methods to ensnare their victims, often casting a wide net through phishing, malvertising on platforms like Google and Facebook, and impersonating illegal software. Once the unsuspecting user takes the bait, the malware springs to life, pilfering login and session data across various applications. Remarkably, these pilferers require no elevated privileges to abscond with cookies, allowing them to operate under the radar. Once executed, the malware goes to work, targeting browsers and apps like Telegram, Discord, and Steam to harvest sensitive data.
The Fallout: From Theft to Ransomware
Stolen cookies are a hacker’s goldmine. They can be used to drain bank accounts, hijack social media profiles for scams, or even serve as the first step in devastating supply chain attacks and ransomware infections.
Who’s Behind It? Top Infostealers Revealed
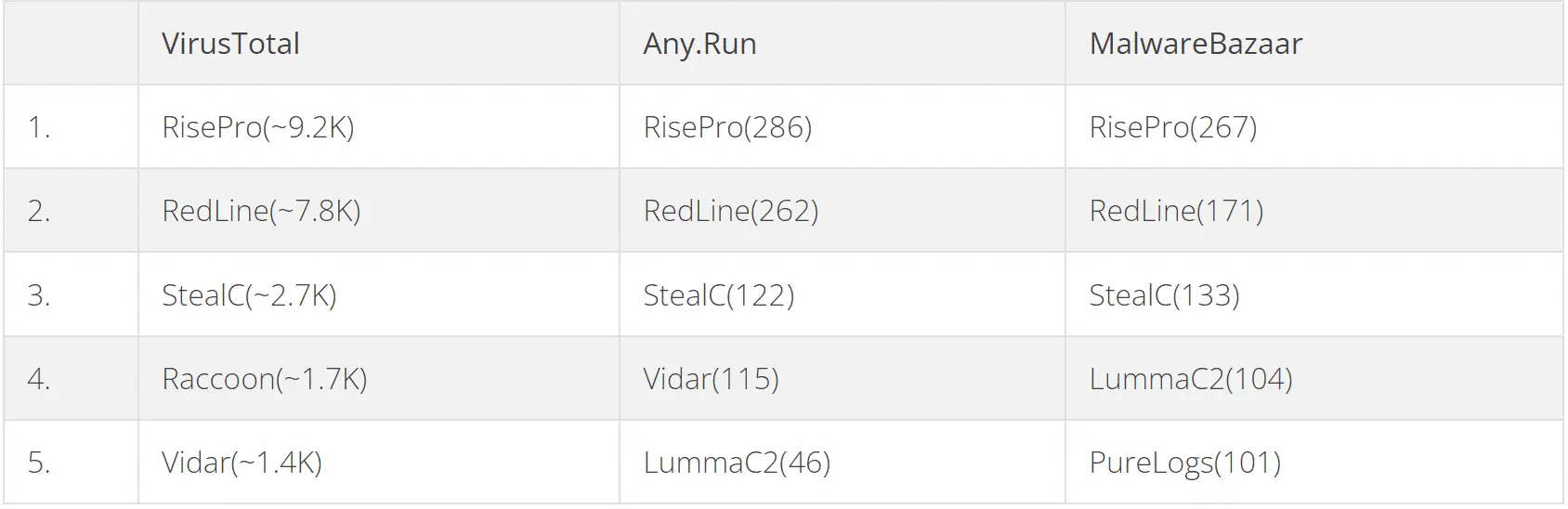
CyberArk’s analysis unmasks the most prevalent infostealers in the wild:
- RisePro: The sheer volume of RisePro attacks is alarming. Researchers criticize its sloppy programming, which could help defenders detect it faster.
- StealC: This malware cleverly fetches part of its configuration from its command and control server, potentially hindering analysis and detection.
- LummaC2: A smaller but rapidly innovating player, LummaC2 could be the next big threat, much like how LockBit grew to dominate the ransomware landscape.
How to Protect Yourself
CyberArk stresses that user awareness is key. Be cautious about emails, suspicious ads, and downloads from untrusted sources. Additionally, they recommend:
- Security Solutions: Employ robust Endpoint Detection and Response (EDR) solutions.
- Secure Browsing: Consider browsers like CyberArk Secure Browser, which can protect cookies and session tokens within secure cloud infrastructure.
The Takeaway
Cookie theft is a rapidly emerging threat that bypasses traditional defenses. By understanding the techniques and staying vigilant, you can help safeguard your digital life.