Image: Cofense
As enterprises increasingly integrate Microsoft Copilot into their workflows, cybercriminals are seizing the opportunity to exploit user unfamiliarity with this AI-powered assistant. A recent report from Cofense highlights a sophisticated phishing campaign leveraging Microsoft Copilot branding to deceive employees into divulging their credentials.
According to Cofense, attackers are distributing phishing emails that appear to originate from “Co-pilot.” These emails, crafted to mimic legitimate Microsoft communications, typically contain a fake invoice notification. “With new services like this, employees may not be aware of what types of emails they should be receiving from the provider,” the report states. “They may not be accustomed to the formatting or appearance of these emails and so, it is easy to imagine a scenario where an employee uses this service for the first time and is sent this spoofed invoice for services, tricking them into clicking on a link.”
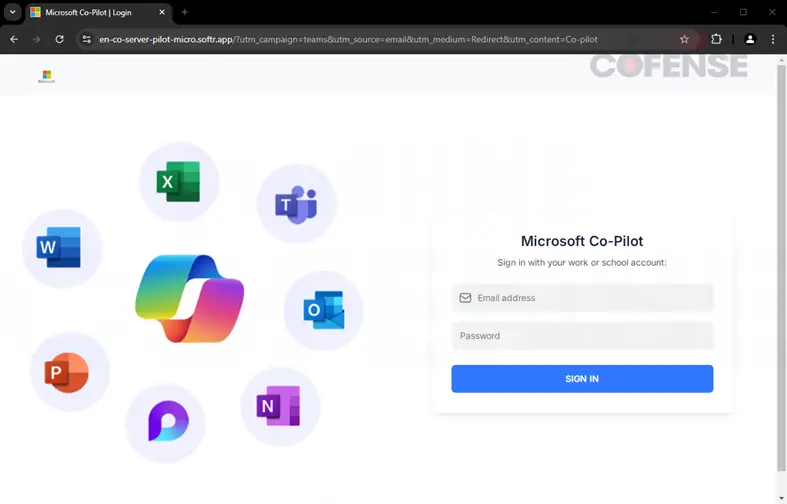
The deception does not end with the email. Upon clicking the embedded link, users are redirected to a phishing page designed to resemble a Microsoft Copilot welcome page. “The page leads the user to believe that they are continuing to a payment dashboard, which aligns with the context of the initial phishing email,” Cofense explains. Notably, the URL does not belong to Microsoft but rather an unrelated domain (e.g., “ubpages.com”), a crucial red flag for those paying close attention.
Once the user reaches the phishing page, they encounter a login prompt replicating Microsoft’s branding, replete with logos and design elements. However, security researchers noted a significant discrepancy: “One thing to notice is that it does not provide a section for a forgotten password. This is a common theme in most credential phishing sites because the threat actor cannot facilitate a password reset because it is not a legitimate service.”
After entering their credentials, victims are directed to a fraudulent Microsoft Authenticator multi-factor authentication (MFA) page. This final deception buys attackers additional time to exploit the compromised account. “This small window where the employee is waiting for an MFA prompt may be all the time they need to reliably change passwords or perform whatever tasks that the threat actor would like,” Cofense warns.
Related Posts:
- Mac Users Rejoice! Microsoft’s Copilot App Lands on the Mac App Store
- New Attack on Microsoft 365 Copilot Steals Personal Data
- Cybercriminals Escalate Attacks with Sophisticated HR-themed Phishing Scam
- Exploring the AI-Powered Windows Search Copilot+ PCs Feature
- Microsoft Integrates AI Agents into GitHub Copilot