Cr3dOv3r v0.4.4 releases: Your best friend in credential reuse attacks
Cr3dOv3r
Your best friend in credential reuse attacks.
You give Cr3dOv3r an email then it does two simple useful jobs with it:
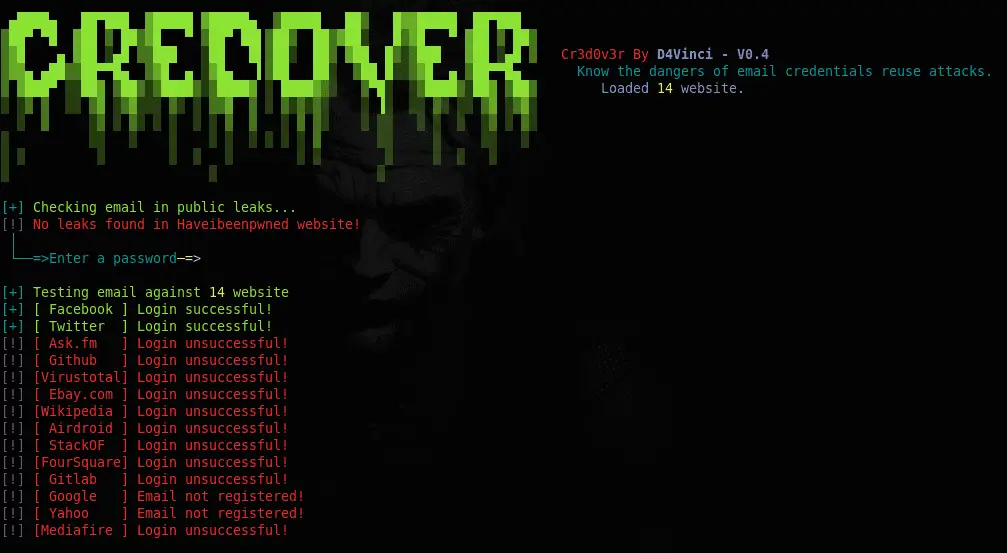
- Search for public leaks for the email and returns the result with the most useful details about the leak (Using haveibeenpwned API) and tries to get the plain text passwords from leaks it finds (Using @GhostProjectME).
- Now you give it a password or a leaked password then it tries this credentials against some well-known websites (ex: Facebook, Twitter, Google…), tells if the login successful and if there’s captcha somewhere blocking our way!
Some of the scenarios Cr3dOv3r can be used in it
- Check if the targeted email is in any leaks and then use the leaked password to check it against the websites.
- Check if the target credentials you found is reused on other websites/services.
- Checking if the old password you got from the target/leaks is still used in any website.
Installing and requirements
To make the tool work at its best you must have :
- Python 3.x.
- Linux or windows system.
- The requirements mentioned in the next few lines.
Installing
+For windows : (After downloading the ZIP and unzip it)
cd Cr3dOv3r-master python3 -m pip install -r win_requirements.txt python3 Cr3dOv3r.py -h
+For Linux :
git clone https://github.com/D4Vinci/Cr3dOv3r.git chmod 777 -R Cr3dOv3r-master cd Cr3dOv3r-master pip3 install -r requirements.txt python3 Cr3dOv3r.py -h
If you want to add a website to the tool, follow the instructions in the wiki
Usage

Disclaimer
This tool is created to show how could credential reuse attacks get dangerous and it’s not responsible for misuse or illegal purposes. Use it only for Pentest or educational purpose !!!
Copying a code from this tool or using it in another tool is accepted as you mention where you get it from 😄
Pull requests are always welcomed 😀
Copyright (c) 2017 Karim shoair
Source: https://github.com/D4Vinci/





