crackerjack
CrackerJack is a Web GUI for Hashcat developed in Python.
Architecture
This project aims to keep the GUI and Hashcat independent. In a nutshell, here’s how it works:
- User uploads hashes select wordlist/rules/mask etc, and clicks “start”.
- Web server spawns a new screen.
- Generates the hashcat command based on the settings.
- Runs the command on the screen.
- Monitors the screen’s output, parses it and displays it in the GUI.
This allows CrackerJack to be future-proof as it ties to the input/output of Hashcat. Also, if the GUI is not working for whatever reason, hashcat will keep running.
Features
- Minimal dependencies
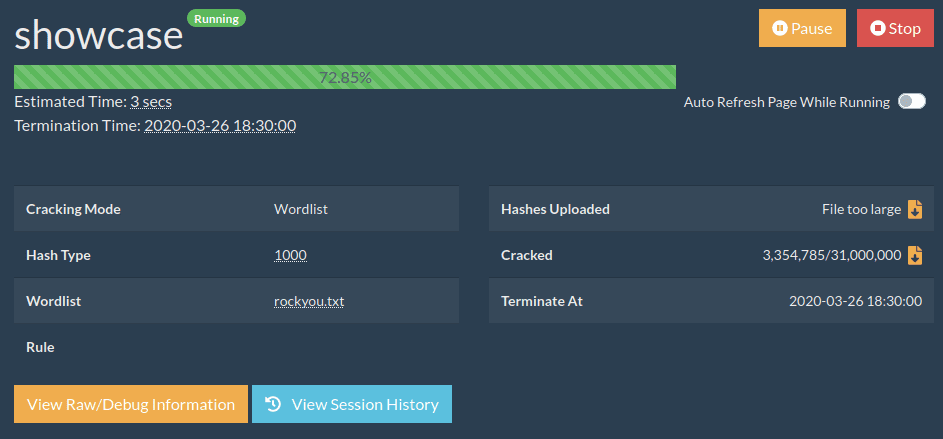
- Complete hashcat session management.
- Start/stop/pause/restore running sessions.
- Terminate cracking jobs after a specific date/time.
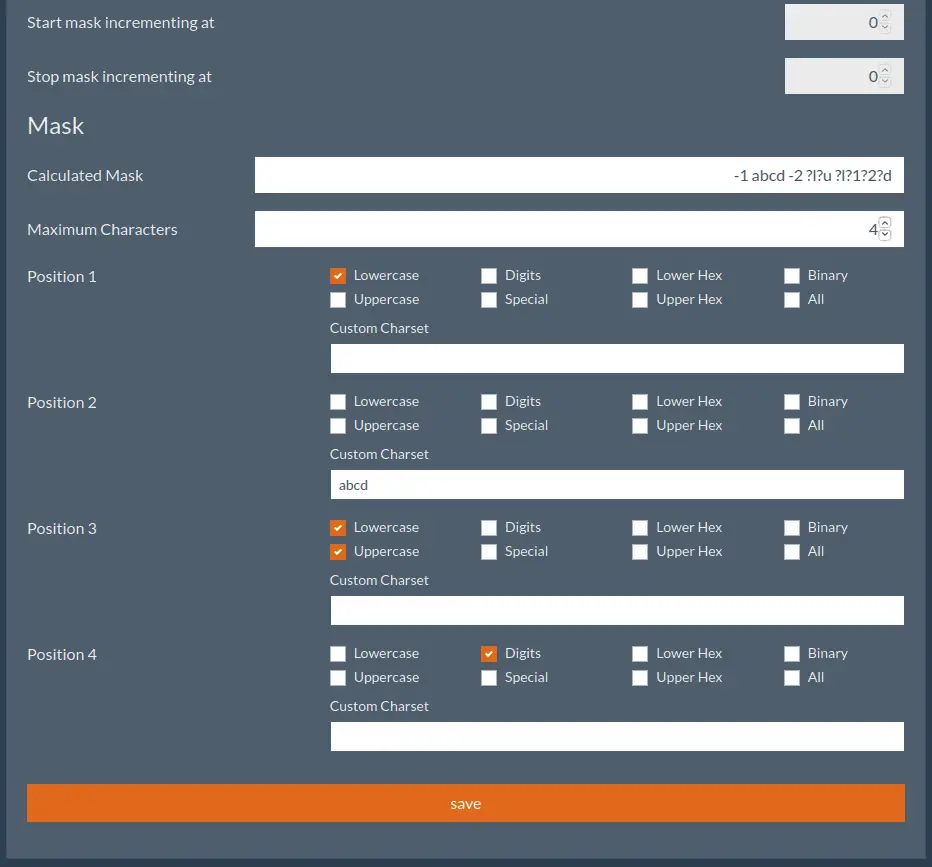
- Web interface for mask generation (?a?l?u).
- Web Push notifications when a password is cracked.
- Swagger 2.0 API.
- Create wordlists from already cracked passwords and feedback into the cracking session.
- Session history to track which attacks you have already performed.
- Multi-user support (local and/or LDAP).
- Wordlist/Mask/Rule support.
- Multiple theme support (Bootswatch).
- Straight-forward setup.
- The entire configuration is via the GUI. No need for manually editing config files.
- Run locally on Linux and Windows (WSL).
- Install on a server using ansible scripts (Ubuntu 14/16/18 and CentOS 7/8).
- Easy backups – all user data are in the ./data directory.
- Troubleshoot sessions via SSH.
Limitations
- Not a solution for queueing jobs – it’s only for on-demand password cracking.
- Not meant to be a replacement for command-line usage. It’s complimentary and only supports basic and most common cracking tasks.
- Will not install any GPU drivers. The main assumption is that you have a cracking rig already set up and are looking for a Web GUI.
- Wordlists and rules should already be present in the system.
Changelog v1.1.2
[New]Added “Test Connection” feature to LDAP settings.
Install
Copyright (c) 2020 Context Information Security