Crafty Infostealer Campaign Leverages Fake Adobe Reader Installer, Advanced Tricks to Evade Detection
Security experts from AhnLab SEcurity intelligence Center (ASEC) have uncovered a sophisticated malware campaign where attackers are tricking users into downloading a dangerous infostealer disguised as a legitimate Adobe Reader installation file. This malware employs several evasive techniques to bypass security measures and steal sensitive data.
The Disguise
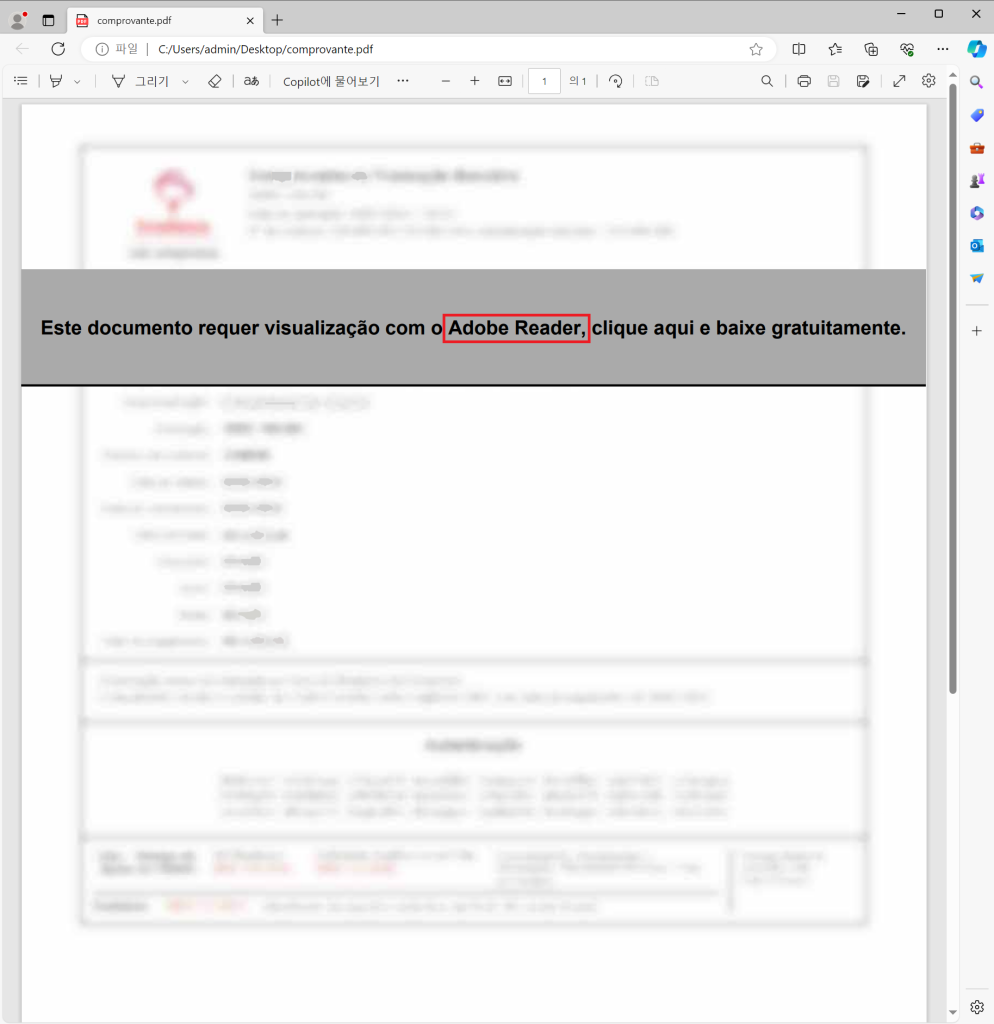
The fake PDF file | Image: ASEC
The attack begins with a seemingly innocent PDF file, often written in Portuguese, that claims an Adobe Reader update is needed to view the document. This common tactic aims to lower victims’ suspicion. Upon clicking within the PDF, victims are redirected to download a malicious file named ‘Reader_Install_Setup.exe’, complete with the familiar Adobe Reader icon.
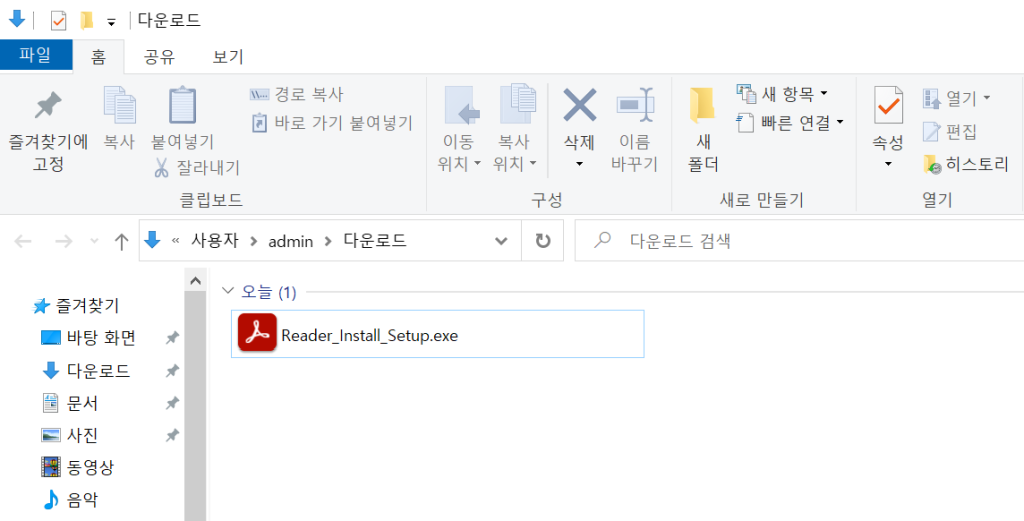
Reader_Install_Setup.exe | Image: ASEC
The Attack Flow

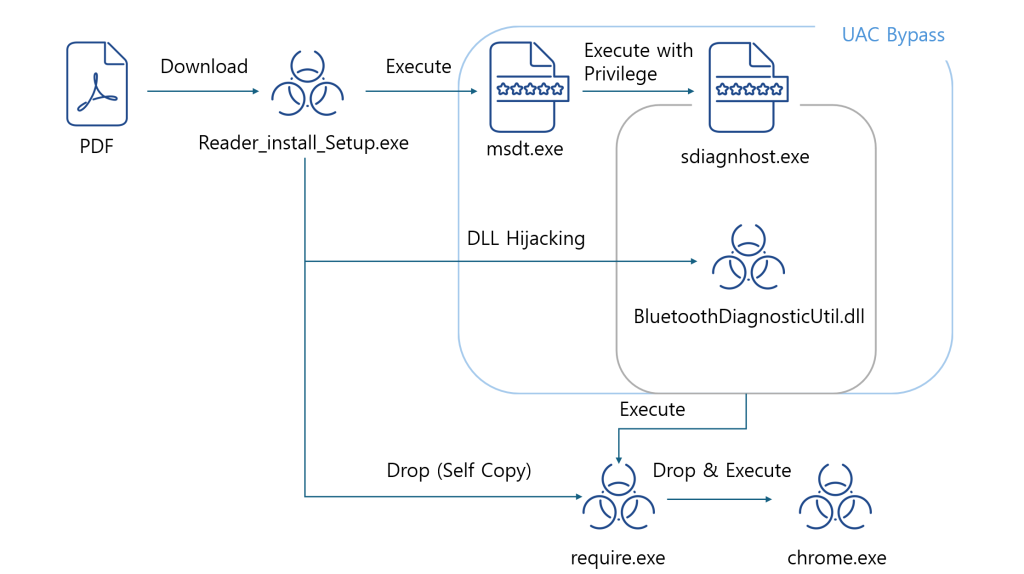
The flow chart | Image: ASEC
- Execution: Once the victim runs the fake installer, the malware creates additional files and takes advantage of a legitimate Windows system file (msdt.exe) to launch a privileged process (sdiagnhost.exe).
- Evasion: Through a technique called ‘DLL hijacking,’ the malware forces the privileged process to load a malicious library, bypassing User Account Control (UAC) – a key Windows security barrier.
- Payload: The final stage involves a fake ‘chrome.exe’ file that masquerades as the Google Chrome browser. This file collects system and browser data, sending it back to the attacker’s command-and-control (C2) servers.
The Threat is Real
This infostealer can harvest a wide range of sensitive information, including:
- System specifications
- Browser history
- Saved passwords
- Other personal data
This stolen information could be used for identity theft, financial fraud, or further targeted attacks.
Protect Yourself
- Be Skeptical: Never download software updates from sources other than the official vendor’s website (in this case, Adobe).
- Trust Your Tools: Keep your antivirus and anti-malware software up-to-date and run regular scans.
- Verify Before Opening: If a PDF or other document seems suspicious, inspect links carefully before clicking on them.
- Think Before Executing: Avoid running executable files (those ending in ‘.exe’) from untrusted sources.





