Crassus Windows privilege escalation discovery tool
Why “Crassus”?
Accenture made a tool called Spartacus, which finds DLL hijacking opportunities on Windows. Using Spartacus as a starting point, we created Crassus to extend Windows privilege escalation finding capabilities beyond simply looking for missing files. The ACLs used by files and directories of privileged processes can find more than just looking for missing files to achieve the goal.
Features
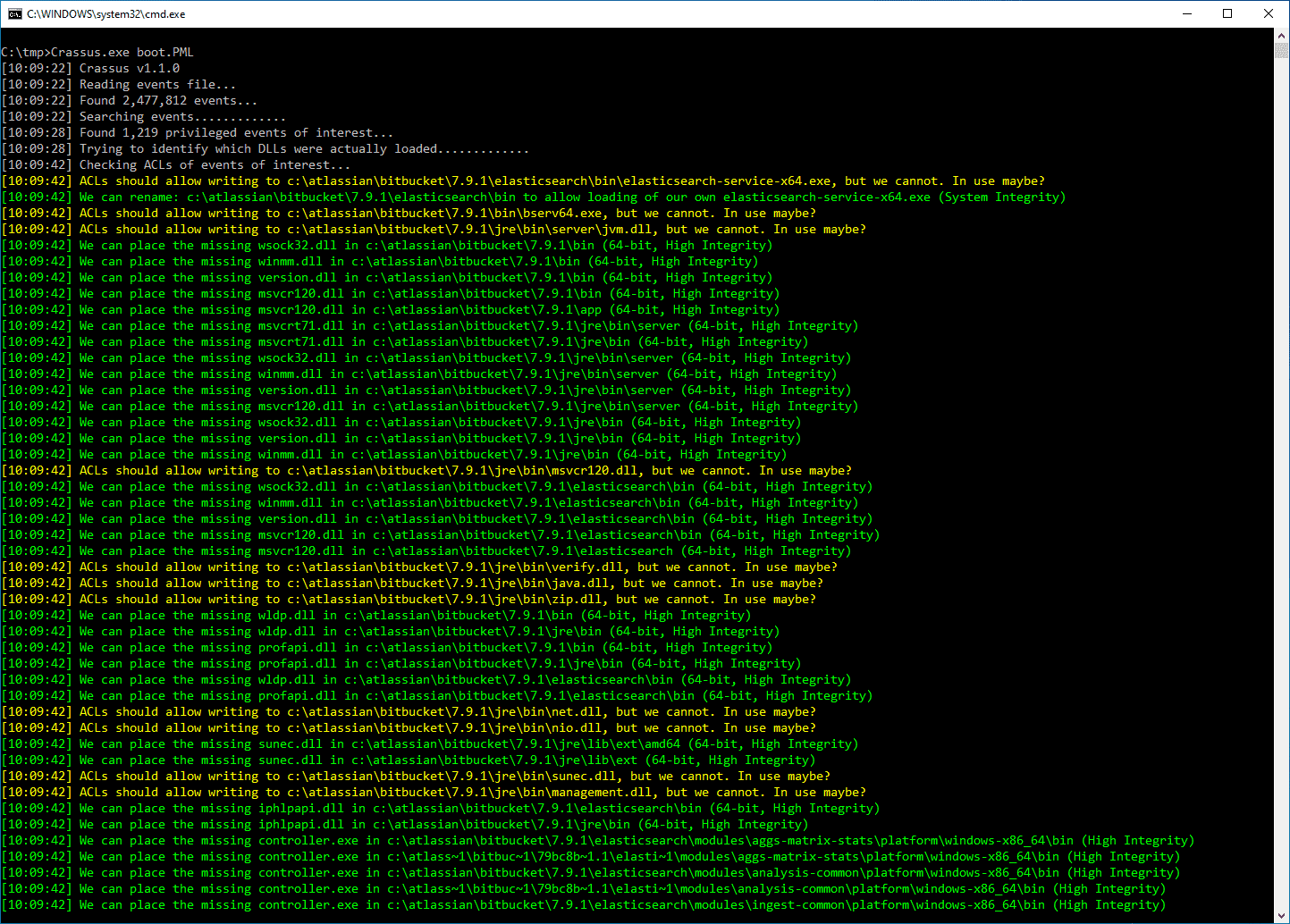
- Parsing ProcMon PML files natively. The log (PML) parser has been implemented by porting partial functionality to C# from https://github.com/eronnen/procmon-parser/. You can find the format specification here.
- Crassus will create source code for proxy DLLs for all missing DLLs that were identified. For instance, if an application is vulnerable to DLL Hijacking via version.dll, Crassus will create version.cpp and version.def files for you with all the exports included in it. By default, the proxy DLLs will launch calc.exe. Build scripts are included to build the DLLs on Visual Studio or MinGW.
- For other events of interest, such as creating a process or loading a library, the ability for unprivileged users to modify the file or any parts of the path to the file is investigated.
- Able to process large PML files and store all events of interest in an output CSV file.
Use
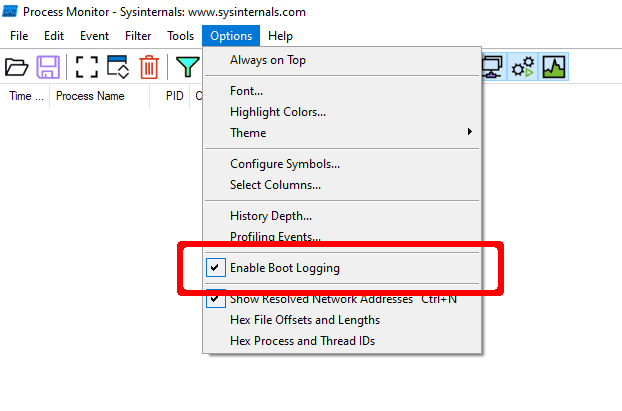
- In Process Monitor, select the Enable Boot Logging option.
- Reboot.
- Once you have logged in and Windows has settled, optionally also run scheduled tasks that may be configured to run with privileges.
- Run Process Monitor once again.
- When prompted, save the boot log.
- Reset the default Process Monitor filter using Ctrl-R.
- Save this log file, e.g., to boot.PML. The reason for re-saving the log file is twofold:
- Older versions of Process Monitor do not save boot logs as a single file.
- Boot logs by default will be unfiltered, which may contain extra noise, such as a local-user DLL hijacking in the launching of of Process Monitor itself.
Install
Copyright (c) 2022 Accenture Security