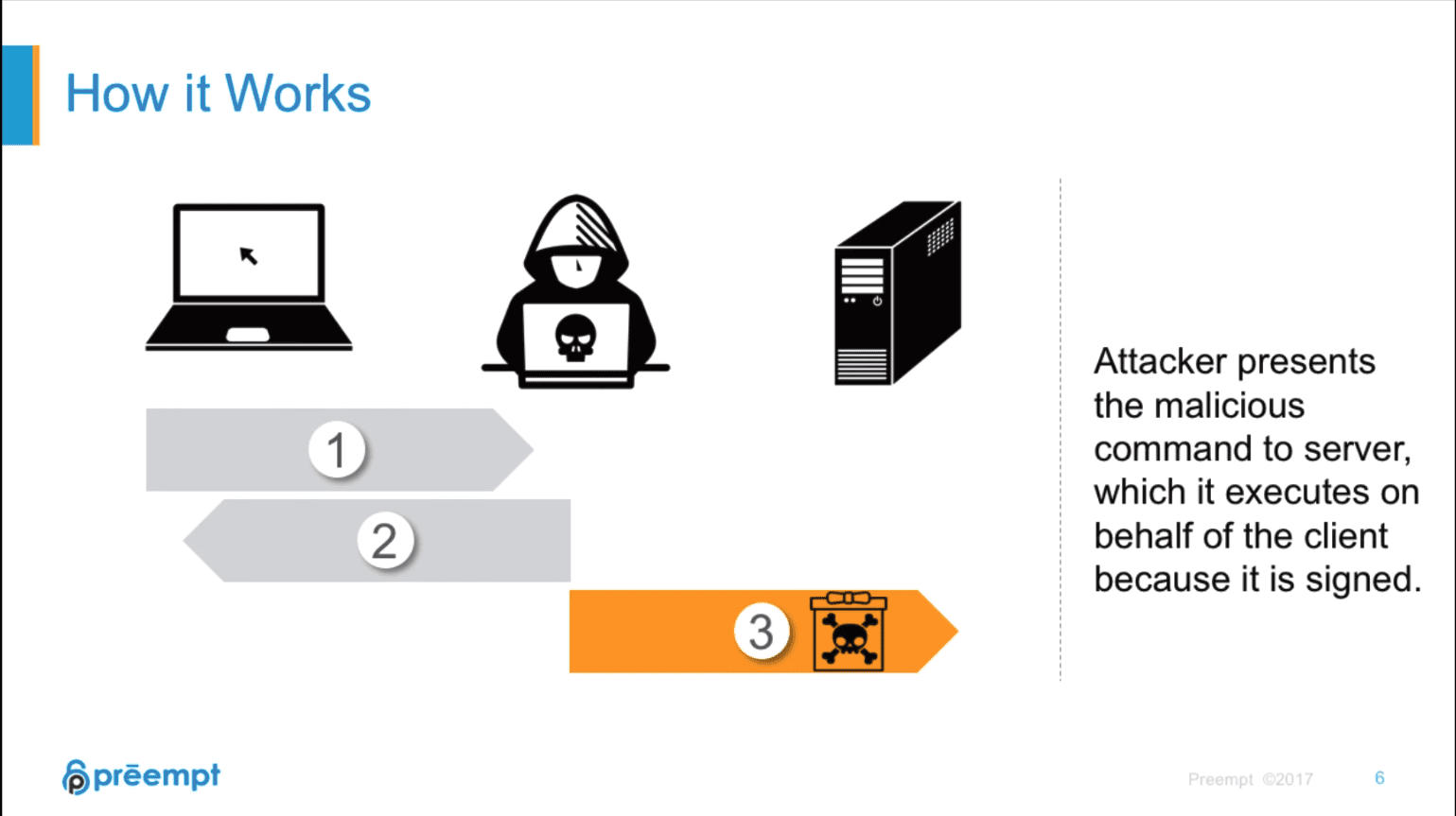
The newly discovered Credential Security Support Provider protocol (CredSSP) vulnerability on the Windows platform allows hackers to use Remote Desktop Protocol (RDP) and Windows Remote Manager (WinRM) to remotely steal data or run malicious code. The CredSSP protocol was originally designed to provide cryptographic authentication when Windows hosts use RDP or WinRM for remote connections.
This vulnerability (CVE-2018-0886) was discovered by a researcher at a company named Preempt Security. There is a logical encryption vulnerability in the CredSSP protocol. A hacker can use a wireless connection to initiate a man-in-the-middle attack. Physical connection to the network, you can also initiate a remote call (Remote Procedure Call) to steal the authentication information in the computer process.

Image: preempt
When a host or server uses Windows’ RDP or WinRM protocol to connect remotely, a hacker’s man-in-the-middle attack can execute malicious code remotely. Once the hacker obtains the computer account login authentication information in the connection process, he has the administrator authority to execute the code remotely.
This attack could be mounted in many real world scenarios. To list a few:
- An attacker with WiFi/Physical access – If an attacker has some physical access to your network, then he could easily launch a man-in-the-middle attack. If you also have WiFi deployed in areas of your network, you might be vulnerable to key reinstallation attacks (KRACK), thus making all machines that do RDP via WiFI exposed to this new attack.
- Address Resolution Protocol (ARP) poisoning – Despite being an old attack technique, many networks are still not 100% protected from ARP poisoning. If this is the case in your network, this new vulnerability means an attacker with control of one machine could easily move laterally and infect all machines in the same network segment.
- Attacking sensitive servers (including domain controllers) – Sometimes, an attacker has control of several workstations in an organization and needs to find a way to infect sensitive business-critical servers (which might require higher privileges). If the network has some vulnerable routers/switches (e.g., CVE-2018-0101 that allows remote code execution on some Cisco routers), it might be relatively easy to infect your critical servers. An attacker will simply infect the router/switch near the server and wait for an IT admin to log-on to the server using RDP.
Most corporate internal networks use the Windows RDP protocol for remote login. Preempt’s researchers reported this vulnerability to Microsoft last August but until now Microsoft released a patch for the vulnerability. If the user’s server is a Windows operating system, update the system as soon as possible; try not to use RDP and DCE/RPC ports at ordinary times; don’t use an administrator account when logging in remotely.