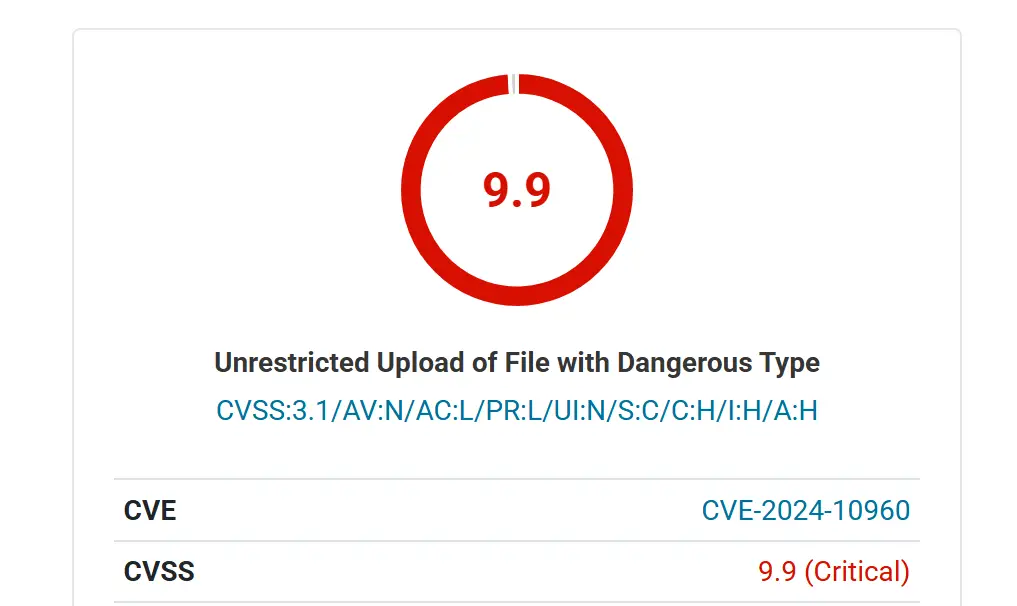
A critical vulnerability has been discovered in the popular Brizy – Page Builder plugin for WordPress, potentially allowing attackers to upload malicious files and compromise entire websites. With over 80,000 active installations, the flaw posed a significant risk to a large number of WordPress users. The vulnerability, identified as CVE-2024-10960, has been assigned a CVSS score of 9.9, indicating its severity.
The flaw resided in the plugin’s storeUploads function and affected all versions up to and including 2.6.4. Crucially, it allowed authenticated users with Contributor-level access or higher to bypass file type validation and upload arbitrary files to the server. This opens the door to a range of attacks, including remote code execution, where attackers could gain complete control of the affected website.
The vulnerability was discovered and responsibly reported by security researcher stealthcopter. A patched version, 2.6.5, has been released and is available for download through the WordPress plugin repository.
Website owners using the Brizy Page Builder plugin are strongly advised to update to version 2.6.5 immediately. Users who have automatic updates enabled should ensure that the update has been applied. Those managing multiple WordPress installations are urged to prioritize updating all affected sites.