Critical Microsoft Access Vulnerability Exploited for NTLM Token Theft
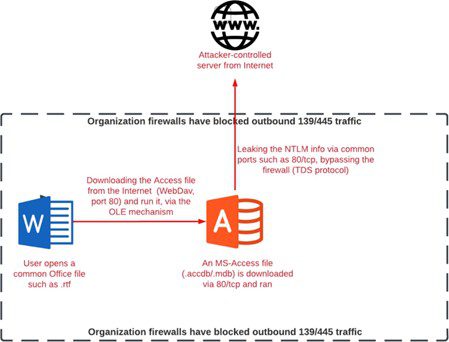
Check Point Research has discovered a vulnerability in Microsoft Access that allows cybercriminals to exploit the “linking to remote SQL Server tables” feature to automatically leak Windows user NTLM tokens to the attacker’s server through any TCP port, including port 80.
NTLM, an authentication protocol introduced by Microsoft in 1993, has long been recognized as outdated due to its vulnerabilities. There are various known attacks on NTLM, including brute-force attacks, Pass-the-Hash, and NTLM Relay attacks. It is important to note that the effectiveness of these attacks can be significantly reduced by blocking outgoing traffic through ports 139 and 445, which NTLM uses.

Abusing link table | Image: Check Point
However, the new vulnerability in Microsoft Access opens up a way to bypass such security measures. By abusing the “Access Linked Tables” feature, an attacker can set up a server listening on port 80 and lure a victim into opening a specially crafted database file. As soon as the victim opens the file and clicks on a linked table, the authentication process begins, during which NTLM tokens can be stolen. An NTLM token includes information that confirms that the user has entered valid credentials (usually a username and password), without the need to send the password itself over the network.
To protect against this attack, it is recommended to be careful about opening attachments from untrusted sources and to consider disabling macros in Microsoft Access or completely removing the program if it is not essential.
Check Point Research has been working with MSRC to address this vulnerability since early 2023. In July 2023, it was confirmed that Microsoft had addressed the vulnerability in the latest version of Office 2021 (Current Channel, version 2306, build 16529.20182), where a warning message is now displayed when attempting to use a PoC exploit, informing the user of the potential danger.





