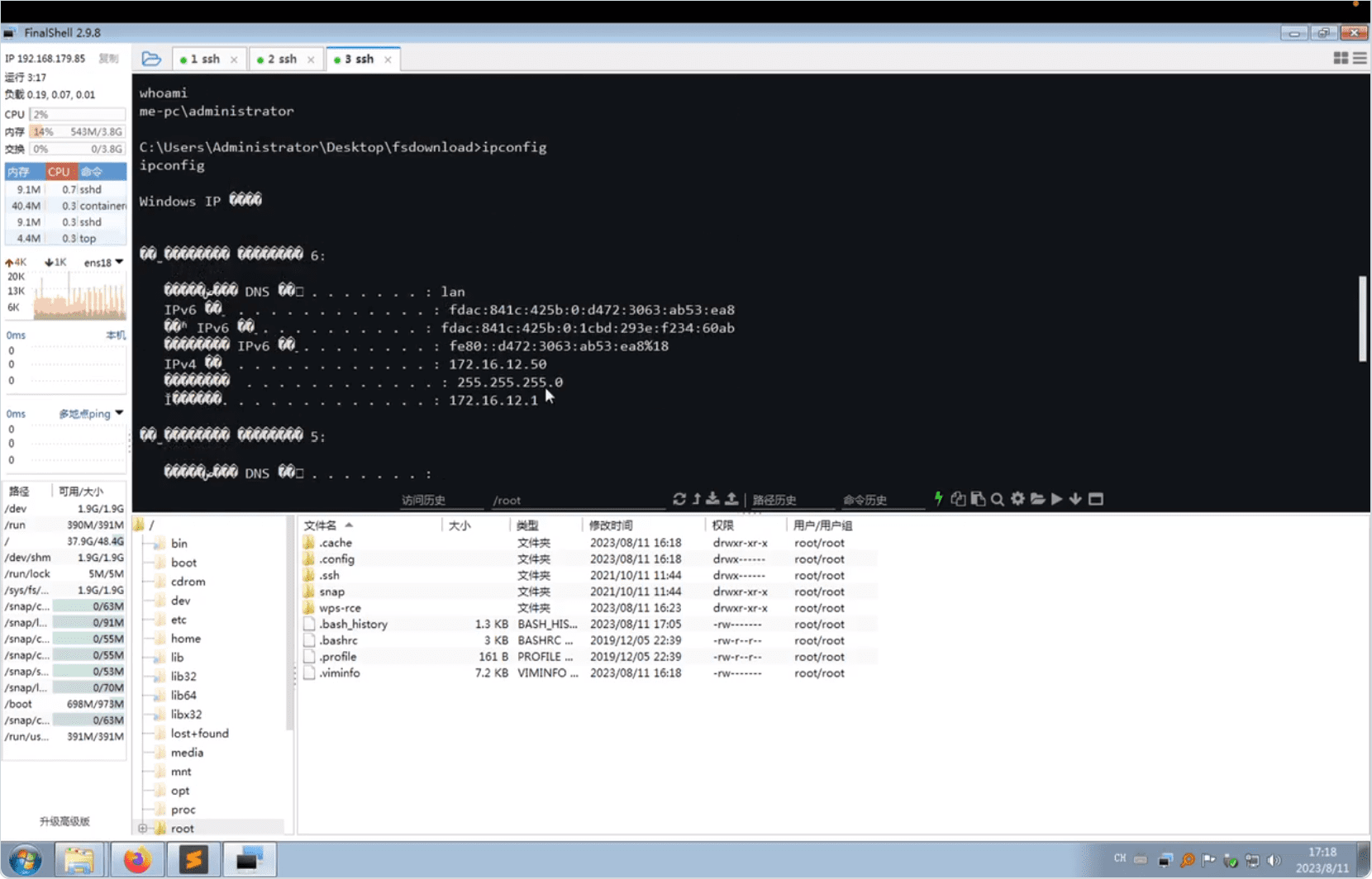
WPS Office, a burgeoning name in the world of digital office suites, found its reputation challenged on August 11, 2023, when a security researcher unveiled the disturbing details of a critical vulnerability that can lead to Remote Code Execution (RCE).
Developed by China’s Kingsoft, WPS Office has become a household name in China and parts of Asia, and is now making waves in the West. Offering a complete package that includes a word processor, spreadsheet tools, presentation software, and PDF reader, it’s a free and open-source alternative to Microsoft Office, available for Windows, macOS, Linux, iOS, Android, and HarmonyOS.
With an impressive tally of over 494 million monthly active users and more than 1.2 billion installations as of 2022, WPS Office’s rise to prominence is undeniable. Its popularity is rooted in its accessibility, flexibility, and user-friendly interface.

The disclosed vulnerability has stirred concerns among users and industry experts alike. The vulnerability affects WPS Office versions 2023 Personal Edition < 11.1.0.15120 and 2019 Enterprise Edition < 11.8.2.12085.
At the root cause of this security flaw is a component known as WebExtension. This is not just a fancy tech term; it’s an integral part of how modern office suites function.
WebExtensions, commonly referred to as Office plug-ins or applications, are a technology that extends the capabilities of Microsoft Office. They enable third-party developers to incorporate unique services and features, using common Web technologies like HTML, CSS, and JavaScript.
In simple terms, think of WPS Office as having an embedded browser that can interpret HTML, JavaScript, and CSS code.
The vulnerability discovered stems from WPS’s inability to correctly handle JavaScript code within the handling of WebExtension. This malfunction leads to an overflow, resulting in Remote Code Execution (RCE) in WPS Office software. This is not a novel error in the world of tech; similar flaws have been previously exposed in platforms like Chrome and WeChat Windows Version < 3.1.2.141.
For users of WPS Office, it’s a moment to reflect on digital safety and remain vigilant for updates and patches. In the meantime, you can protect yourself from this vulnerability by:
- Not opening suspicious documents from unknown sources.
- Keeping your antivirus software up to date.
- Using a firewall to protect your computer from unauthorized access.
- Being careful about what websites you visit and what links you click on.