Security researcher Zach Hanley from Horizon3.ai published the technical details and a proof-of-concept (PoC) exploit code for a critical hardcoded credential vulnerability, CVE-2024-28987, in the popular SolarWinds Web Help Desk (WHD) software. This vulnerability, which received a CVSS score of 9.1, has significant implications for organizations using the WHD platform, especially those handling sensitive IT support data.
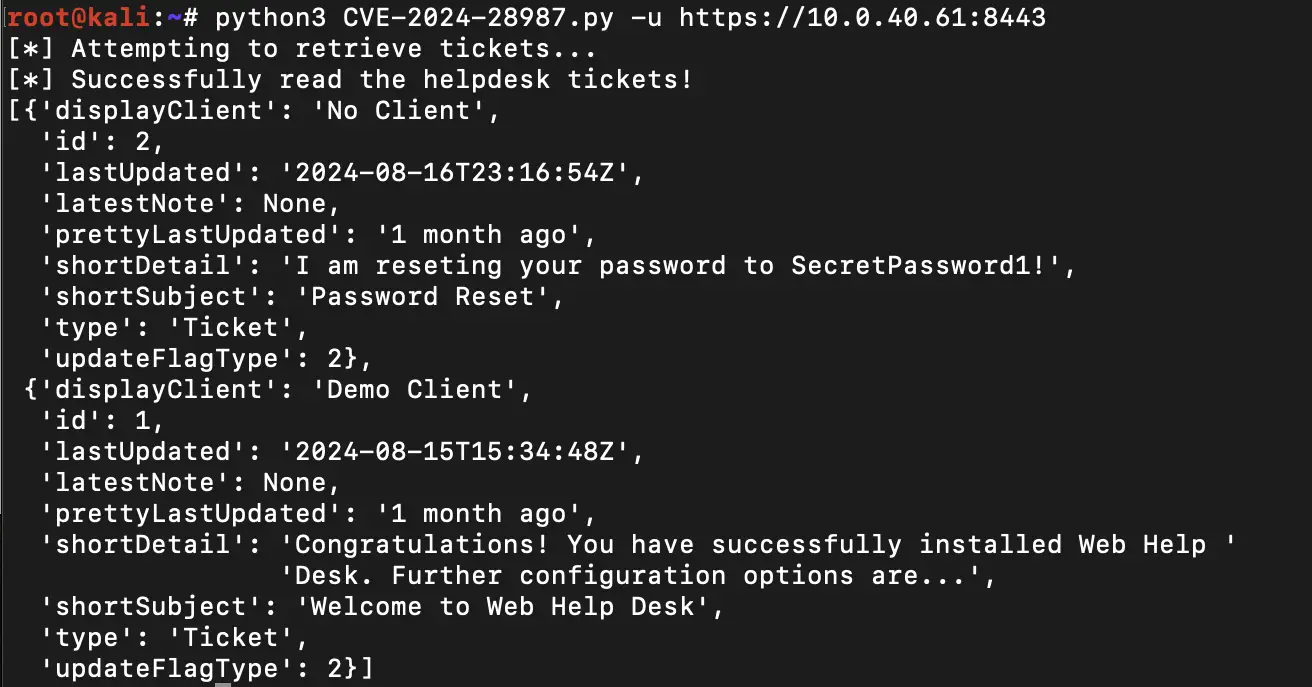
CVE-2024-28987 is a flaw that stems from the presence of hardcoded credentials in SolarWinds Web Help Desk software. These credentials, embedded in the OrionTicketController module, allow unauthenticated attackers to remotely access and modify help desk ticket details. This includes access to sensitive data such as:
- Password reset requests
- Shared service account credentials
- IT onboarding processes
The hardcoded credentials, which were found to be “helpdeskIntegrationUser” and “dev-C4F8025E7,” provide unrestricted access to SolarWinds WHD’s OrionTickets endpoints. Attackers leveraging this vulnerability can perform various actions, including creating, reading, updating, and deleting help desk tickets. The exposure of such sensitive information creates a substantial risk for affected organizations, as these tickets may contain internal procedures and credentials that can be used for further exploitation.
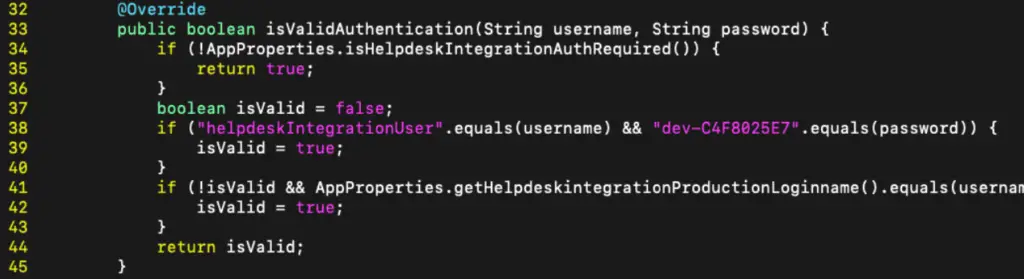
In his analysis, Hanley detailed the steps leading to the discovery of this vulnerability. By reviewing patch differences from previous vulnerabilities such as CVE-2024-28986 and inspecting routes and controllers within the WHD core, the hardcoded credentials were uncovered. Notably, SolarWinds had previously addressed similar vulnerabilities, like CVE-2021-35232, but had missed these specific developer credentials that were directly referenced in the code rather than declared in configuration files.
Hanley and Horizon3.ai have provided a proof-of-concept (PoC) exploit to demonstrate the CVE-2024-28987 vulnerability.
At the time of Hanley’s publication, approximately 827 instances of SolarWinds Web Help Desk were publicly accessible on the internet, making this vulnerability particularly concerning for organizations using WHD.
While the vulnerability doesn’t lead to the complete compromise of the WHD server, it opens the door to lateral movement within an organization’s network by exposing shared credentials and internal IT processes. Organizations relying on WHD for user onboarding, password management, and IT support are especially vulnerable to credential harvesting and unauthorized access.
One potential indicator of compromise is abnormal activity around the OrionTickets endpoints. The WHD logs provide limited visibility, but suspicious IP addresses querying these endpoints can be flagged. Organizations are advised to inspect their WHD access logs for any signs of unauthorized enumeration of help desk tickets.
In response to this discovery, SolarWinds has released a critical hotfix—SolarWinds Web Help Desk 12.8.3 Hotfix 2—which addresses both CVE-2024-28987 and another recently patched vulnerability, CVE-2024-28986.
Related Posts:
- SolarWinds Web Help Desk Hit by Critical Vulnerability (CVE-2024-28987)
- SolarWinds Patches Multiple Critical Vulnerabilities in Access Rights Manager
- CVE-2024-28986 (CVSS 9.8): SolarWinds Web Help Desk Users Must Patch Now!