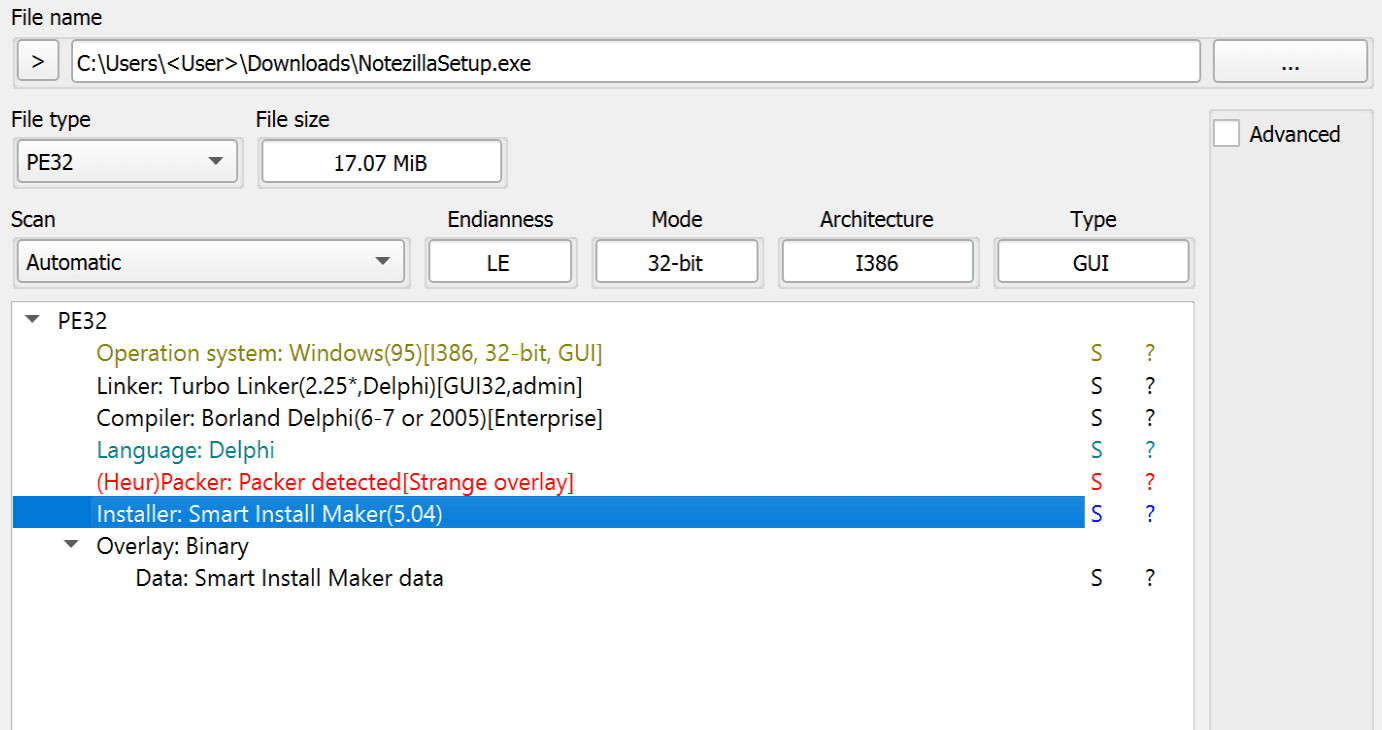
Software Properties of NotezillaSetup.exe
Rapid7, a prominent cybersecurity firm, has uncovered a sophisticated supply chain attack targeting users of well-known Windows software tools Notezilla, RecentX, and Copywhiz. The attack involves the distribution of trojanized installers that, alongside legitimate software, install information-stealing malware capable of downloading additional malicious payloads.
Conceptworld offers three main software products:
- Notezilla: A program that allows users to create sticky notes on their Windows desktops.
- RecentX: A tool that stores recently used files, applications, and clipboard data.
- Copywhiz: Software that enhances file copying and backup operations.
The malicious actors behind this attack compromised the official website of Conceptworld, the Indian company behind these software tools. When unsuspecting users downloaded the installers, they unknowingly received a package that included the legitimate software along with hidden malware. This malware, dubbed “dllFake” by Rapid7, possesses a wide range of capabilities, including stealing sensitive information like browser credentials, cryptocurrency wallet data, and keystrokes, as well as establishing persistence on the infected system by executing the primary payload every three hours through a scheduled task.
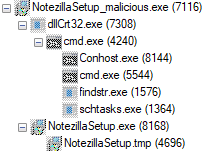
Upon discovering the attack, Rapid7 promptly disclosed the issue to Conceptworld, who acted swiftly and responsibly to remove the malicious installers and replace them with legitimate, signed copies. However, users who downloaded the affected installers within the past month remain at risk and are advised to take immediate action.
To determine if your system has been compromised, look for specific indicators of infection. These include the presence of a hidden scheduled task named “Check dllHourly32” and a persistent command prompt process making outbound network connections using “curl.exe.” If you suspect your system is infected, it is crucial to take immediate steps to mitigate the damage. This includes running a thorough scan with updated antivirus/antimalware software, changing passwords for affected accounts, monitoring financial statements for suspicious activity, and considering professional cybersecurity assistance if needed.
For a deeper dive into the technical details of this attack, including indicators of compromise and mitigation strategies, refer to the comprehensive Rapid7 report. It provides valuable insights for cybersecurity professionals and individuals alike, empowering them to better understand and defend against supply chain attacks.