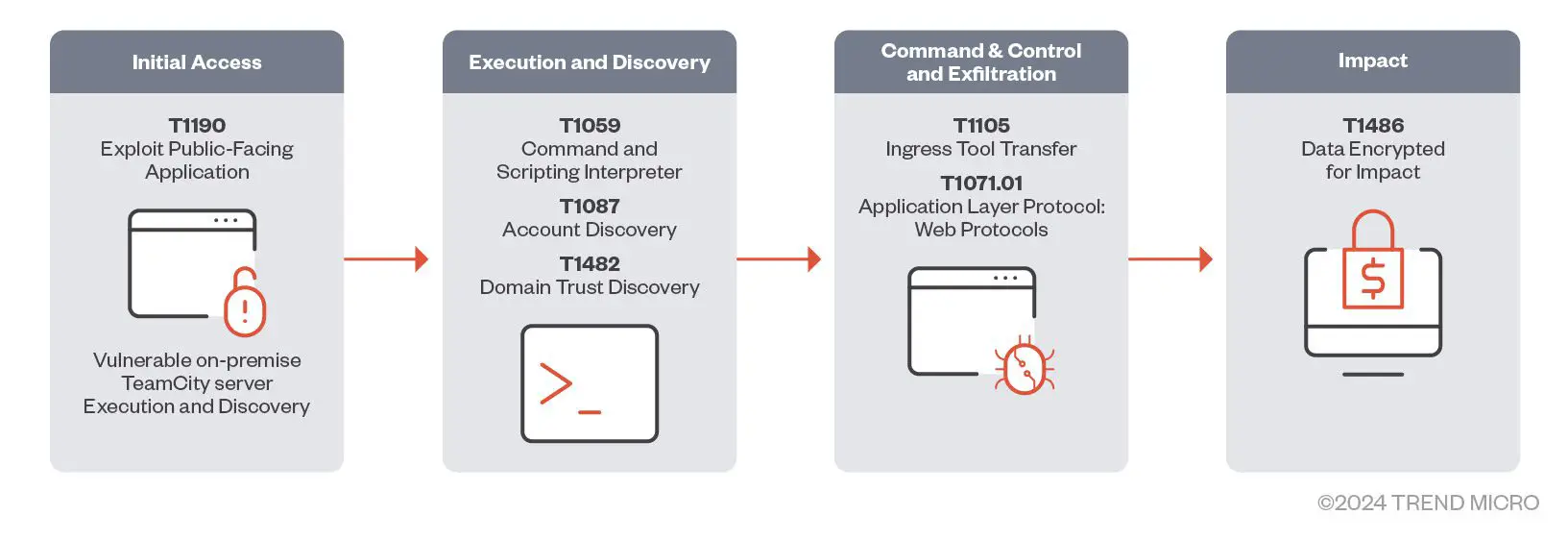
Attack diagram
A wave of cyberattacks is crashing down on organizations using the TeamCity CI/CD platform, exploiting recently disclosed vulnerabilities that allow hackers to seize control of servers. The Trend Micro cybersecurity team has uncovered a devastating campaign where threat actors are using these flaws to unleash Jasmin ransomware, XMRig cryptocurrency miners, and backdoors like SparkRAT.
The Vulnerabilities: Your Doorway to Disaster
CVE-2024-27198, with a Critical CVSS score of 9.8, is an authentication bypass vulnerability that exposes systems to remote code execution (RCE) by exploiting an alternative path issue. Meanwhile, CVE-2024-27199, marked by a High CVSS score of 7.3, is a directory traversal vulnerability that can also lead to authentication bypass, enabling attackers to leak sensitive information and tamper with specific system settings. The disclosure of these vulnerabilities has been compounded by the release of public proof-of-concept exploits, significantly increasing the risk of widespread exploitation.
The Fallout: From Cryptominers to Corporate Espionage

Trend Micro has observed a disturbingly diverse array of malware unleashed on compromised systems:
- Jasmin Ransomware: This potent threat encrypts critical data, holding it ransom until a hefty payment is made. A successful attack can cripple business operations and lead to immense financial loss.
- XMRig Cryptocurrency Miner: Attackers hijack infected systems’ computing power to mine cryptocurrency for their own profit, slowing down servers and driving up electricity costs for the victim organization.
- SparkRAT Backdoor: This remote access trojan grants hackers near-silent control over a compromised machine, allowing them to exfiltrate data, deploy additional malware, or maintain a persistent foothold for future attacks.
- Cobalt Strike Beacons: These sophisticated tools, often favored by advanced hacking groups, facilitate lateral movement within a network and enable attackers to steal sensitive information or deploy devastating payloads on a larger scale.
The Domino Effect of System Compromise
Successful exploitation doesn’t end with malware installation. Attackers also use their foothold in TeamCity servers for network reconnaissance and to establish persistence for long-term access.
Protect Yourself Now!
If your organization uses TeamCity On-Premises, time is of the essence. Patch these vulnerabilities immediately! JetBrains has released fixes, and even the US Cybersecurity and Infrastructure Security Agency (CISA) has flagged this as a majorly exploited threat.