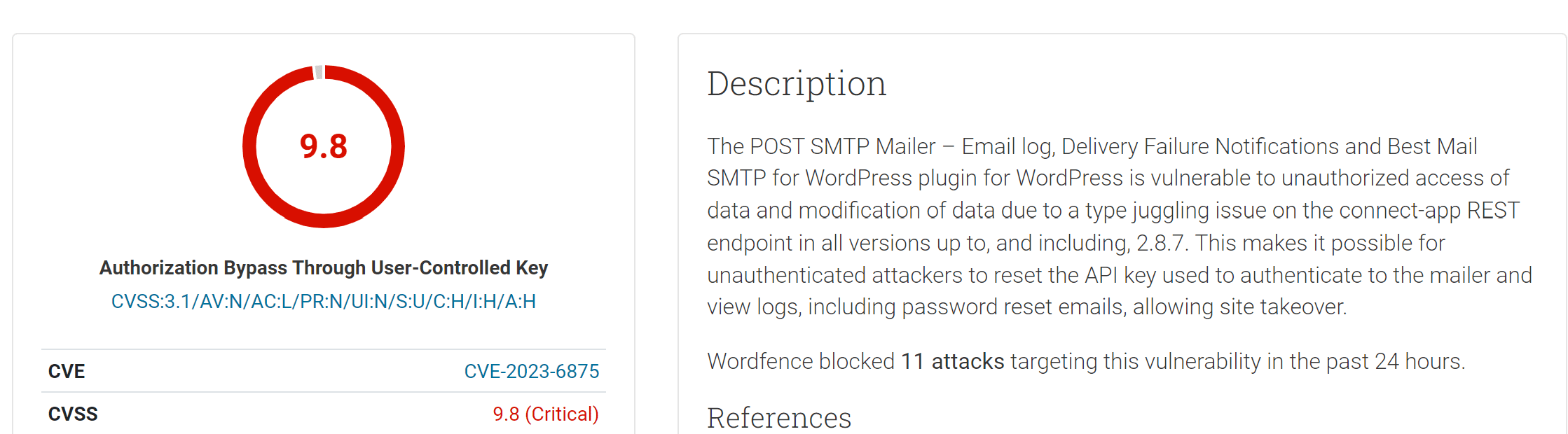
Recently, a critical flaw named CVE-2023-6875 has emerged, targeting Post SMTP, a popular WordPress SMTP plugin, and posing a grave threat to over 300,000 websites. This vulnerability is not just a bug; it’s a gateway for attackers, leading straight to the core of WordPress email security.
Post SMTP, renowned for its robust email deliverability solutions, is a staple in the WordPress community. Its free version offers substantial features, while the Pro version elevates the game with detailed email logging, advanced reporting, and seamless integrations with Microsoft 365, Amazon SES, and Zoho SMTP. It’s the trusted armor for WordPress emails, safeguarding them from the abyss of spam folders and unreliable delivery.
CVE-2023-6875, with a CVSS score of 9.8, exists in the Post SMTP landscape, exploiting a type juggling issue in the connect-app REST endpoint. Present in all versions up to 2.8.7, this flaw is like an open backdoor for unauthenticated attackers. They can not only reset the API key, central to the authentication to the mailer but also gain the ability to view sensitive logs. This includes password reset emails and opening site takeover opportunities.
Credit goes to the security researcher Ulyses Saicha, who reported this flaw. His discovery shed light on a vulnerability that affected all versions of the plugin before 2.8.8.
The threat is not hypothetical. Wordfence, a leading security solution for WordPress, reports witnessing at least 11 attack attempts per day against the sites it protects.

For website owners, the message is clear: update to the latest version of Post SMTP, stay informed and remain vigilant.