Image: Checkmarx Security Research Team
In a concerning development, cryptocurrency enthusiasts are facing a new and highly invasive malware campaign aimed at draining their wallets and stealing sensitive data. Security researcher Yehuda Gelb from the Checkmarx Security Research Team uncovered this sophisticated, multi-vector attack, which employs several deceptive strategies, including a malicious Python package and a fake website, to trick cryptocurrency users.
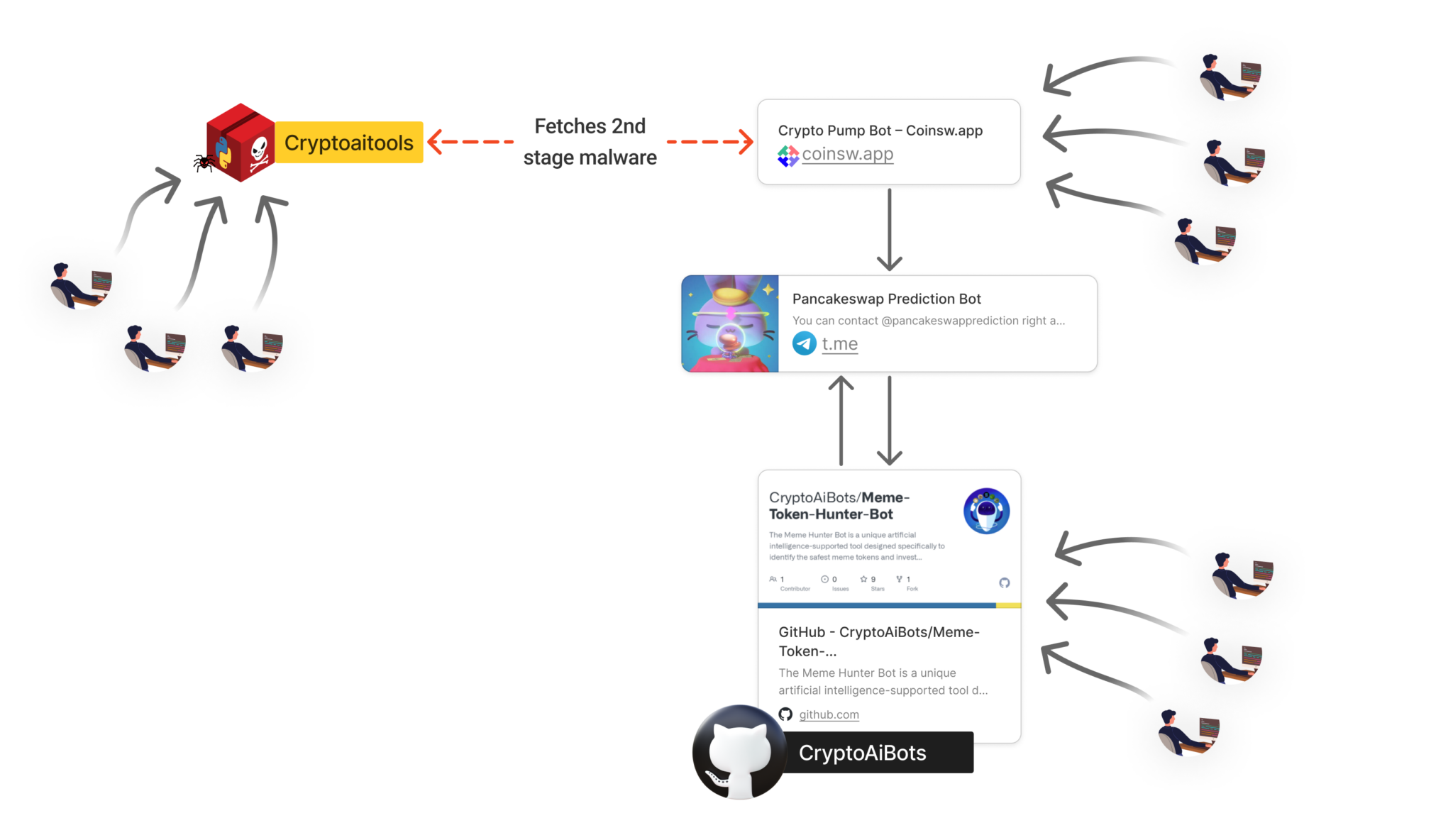
The attack hinges on multiple distribution channels, each crafted to lure unsuspecting users:
- Malicious PyPI Package: A Python package named “cryptoaitools” was uploaded to PyPI, posing as a legitimate cryptocurrency trading tool. This package included “a seemingly functional trading bot implementation,” complete with features for automated trading and liquidity management. Gelb’s analysis reveals, however, that “the malware activated automatically upon installation,” targeting both Windows and macOS systems and initiating data theft.
- Deceptive GitHub Repository: The attackers also set up a GitHub repository titled “Meme-Token-Hunter-Bot,” mirroring the same malicious code found in the PyPI package. This repository could infect any users who clone and execute the code, extending the reach of the campaign.
- Fake Cryptocurrency Website: The attackers established a website at https://coinsw.app, complete with fake user reviews and subscriber statistics to resemble a legitimate AI-driven trading platform. Gelb explains that “the domain hosts a convincing appearance of a cryptocurrency trading bot service,” luring victims with what appears to be a professional tool.
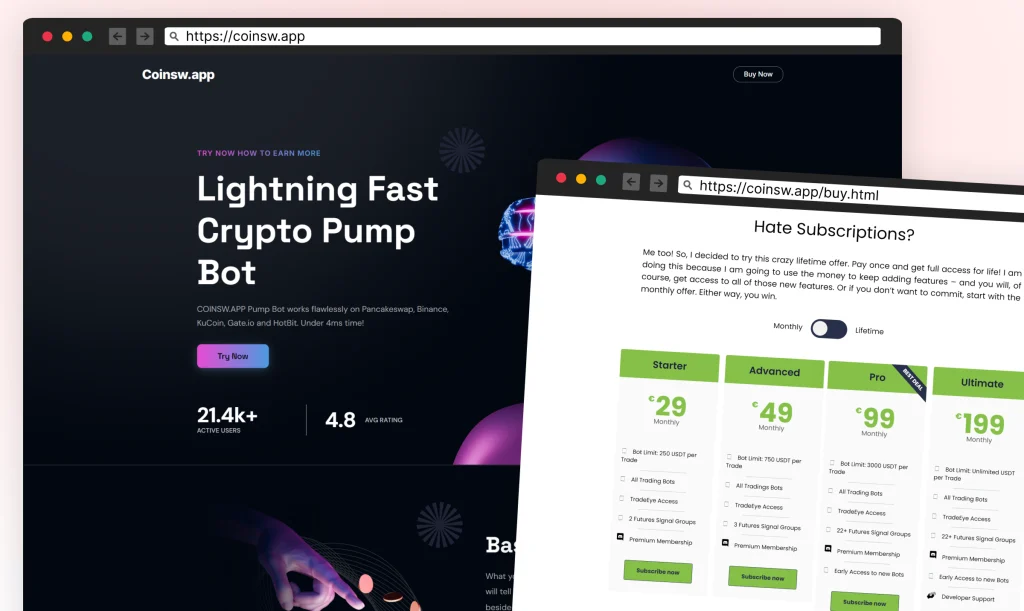
The attackers employed a graphical user interface (GUI) as a social engineering tactic, designed to engage users while the malware operates covertly. Once the second-stage malware is activated, users are presented with a fake “AI Bot Starter” app that prompts them to create a password, displaying a setup progress bar and loading animations. According to Gelb, “While users are engaged and focused on this seemingly legitimate interface… the malware continues its malicious operations in the background, including data theft and system manipulation.”
CryptoAITools is exceptionally invasive, targeting a broad range of sensitive information:
- Cryptocurrency Wallet Data: The malware seeks data from various wallet applications, including Bitcoin, Ethereum, and Electrum, among others.
- Browser Data: It captures saved passwords, cookies, and browsing history, with a particular focus on extensions related to cryptocurrency.
- Sensitive System Files: Including SSH keys and configuration files.
- Social Media and Communication Data: The malware collects data from applications such as Telegram, including configuration files and message databases.
- Apple macOS Data: It even retrieves information from applications like Apple Notes and Stickies on macOS.
Gelb details how the malware exfiltrates this data: it stores the stolen files in a hidden .temp directory, changing file extensions to .minecraft to evade detection. The files are then uploaded to gofile.io, where download links are sent to the attacker via a Telegram bot. This intricate process helps the malware avoid disruption while actively exfiltrating valuable information.
The implications of this campaign are significant. The immediate threat to victims includes financial losses through cryptocurrency theft and potential identity theft due to the breadth of data stolen. Gelb warns, “The true scope of the attack may be larger than initially thought,” especially given the malicious repository on GitHub, which many users starred or forked, potentially widening the pool of victims.
Related Posts:
- Solana Drainer Source Code Leak Reveals MS Drainer Connection, Underscores Growing Threat to Crypto Users
- Fake WalletConnect App on Google Play Drains $70K in Crypto