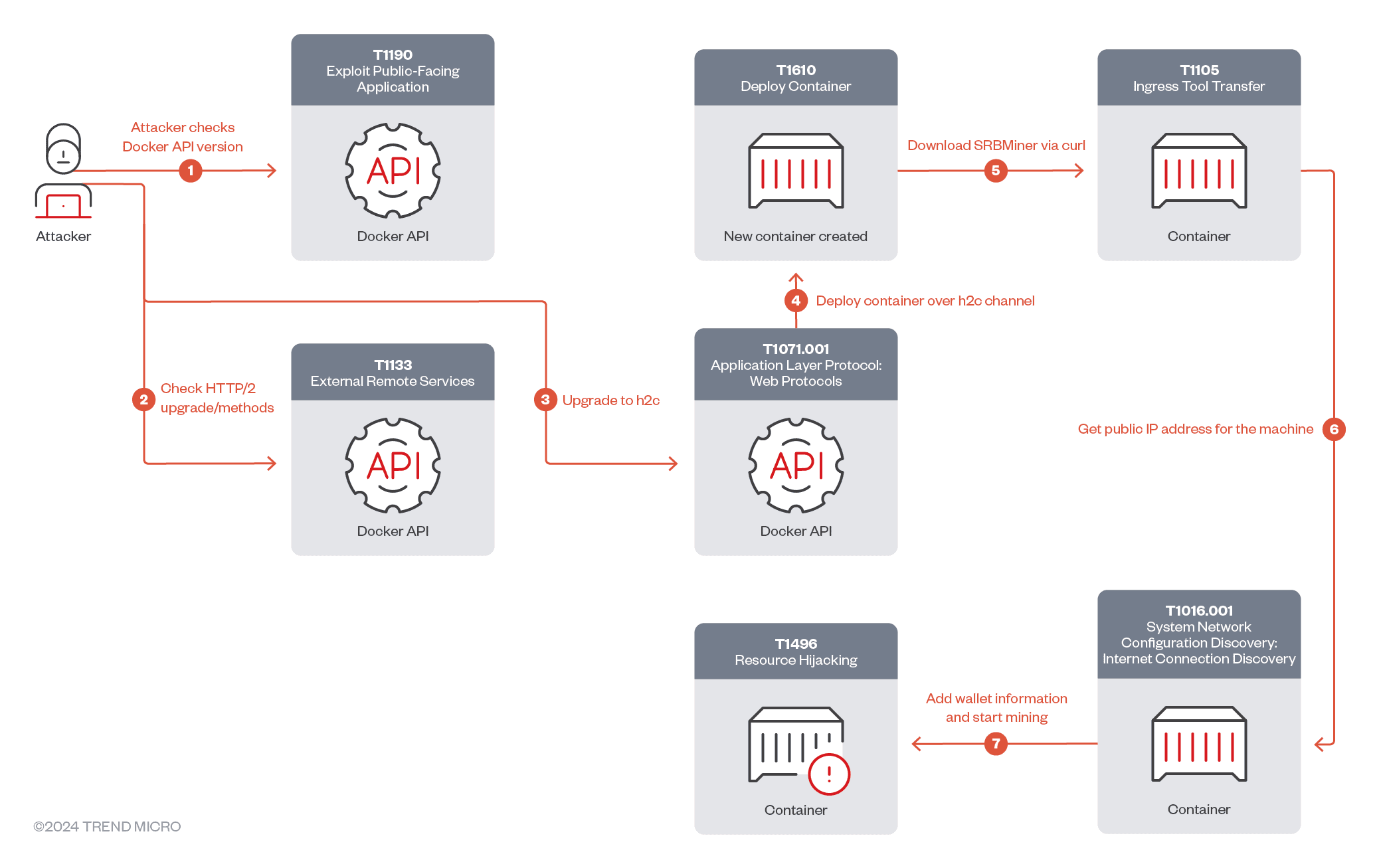
Attack chain | Image: Trend Micro
Trend Micro researchers have uncovered a new and unconventional method used by cybercriminals to deploy the SRBMiner cryptominer on Docker remote API servers. This attack leverages the gRPC protocol over h2c (clear text HTTP/2) to evade security solutions and mine XRP cryptocurrency, developed by Ripple Labs.
The attack begins with the threat actor scanning for vulnerable Docker API servers. Once identified, the attacker checks the availability and version of the Docker API and proceeds to send a request for a gRPC/h2c upgrade. According to the researchers, this upgrade request is crucial, as it allows the attacker to manipulate Docker functionalities remotely without detection.
Once the connection is upgraded, the attacker utilizes gRPC methods to perform tasks like file synchronization, authentication, and SSH forwarding. Trend Micro’s report notes that “these methods are designed to facilitate various operations within Docker, including health checks, file synchronization, authentication, secrets management, and SSH forwarding.” These functionalities allow attackers to execute commands as though they were directly managing the server.
After establishing control, the attacker deploys the SRBMiner cryptominer. This is done by building a Docker image using a legitimate base image, debian:bookworm-slim, and deploying the miner in the /usr/sbin directory. The malware is downloaded from GitHub and unzipped into a temporary directory before the cryptomining process begins. The threat actor then provides their Ripple wallet address to collect the mined cryptocurrency.
One of the reasons this attack is particularly concerning is the use of the gRPC protocol over h2c, which allows the attacker to bypass security layers. By using this method, the threat actor can obscure their activities, making it difficult for security tools to detect the cryptominer deployment. The attackers also take advantage of Docker’s remote API features to execute commands stealthily and ensure continuous mining.
This attack demonstrates the evolving strategies of cybercriminals, who continue to find innovative ways to exploit containerized environments like Docker. As noted by the researchers, “containerization platforms like Docker are instrumental in modern-day application development, but their features can become security liabilities if not meticulously protected.” The use of gRPC over HTTP/2 in this attack highlights the importance of securing Docker remote APIs and monitoring unusual activities.
Related Posts:
- Cryptojacking Campaign Exploits Atlassian Confluence CVE-2023-22527 Vulnerability
- DOCKER deletes 17 malicious container images