CSCGuard: Protects and logs suspicious and malicious
CSCGuard
Protects and logs suspicious and malicious usage of .NET CSC.exe and Runtime C# Compilation
Features
- Able to detect and prevent runtime C# compilation used by malware even when “GenerateInMemory” is used
- Limited Heuristic detection of suspicious usage of CSC.EXE
- Variable threshold to allow pass-thru to original CSC.EXE or to deny execution
- Optional Windows Event Log creation whenever CSCGuard is triggered
- Captures Evidence in %USERPROFILE%\CSCGuard\Log\ to allow future analysis
- Provides detailed logs for users to review all parameters passed to CSC.EXE
- Minorly customizable using App.Config
Log and Evidence
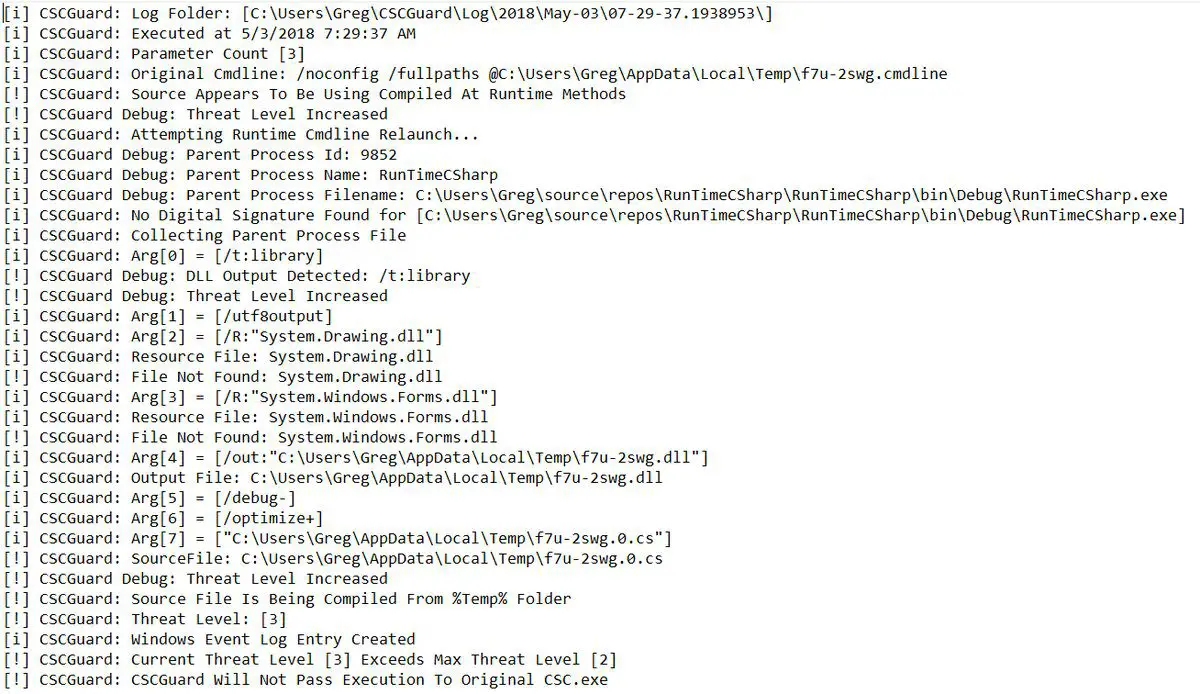
CSCGuard will attempt to capture the following files and evidence upon execution:
- The Parent Process .EXE which called CSC.EXE
- All C# source files passed as parameters to CSC.EXE
- The compiled binary results (if passed to CSC.EXE)
- Any temporary files in the source folder that appear to be related to the CSC.EXE execution (Runtime Compilation).
Log parent folder is by default set to %USERPROFILE%\CSCGuard\Log. Each execution generates an individual log file folder in the following format MM-DD\HH-mm-ss.fffffff
Example: %USERPROFILE%\CSCGuard\Log\2018\May-03\00-04-15.7864500
Log Files
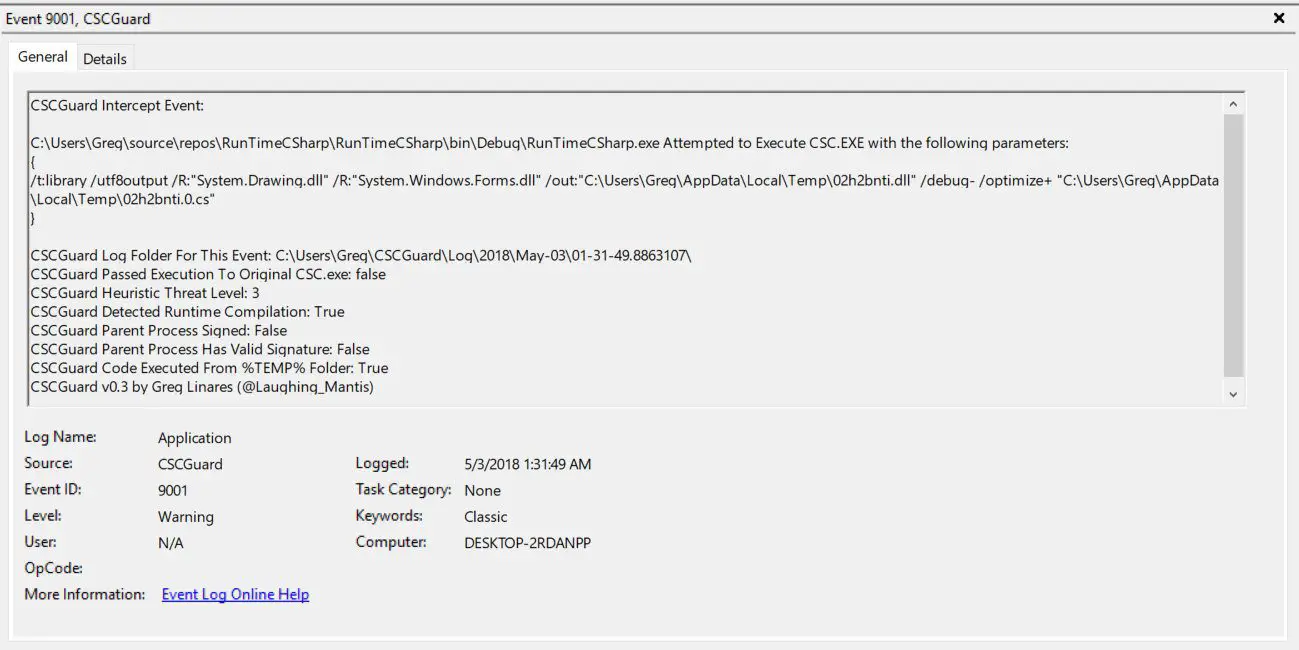
CMDLine.txt – Contains the original (or runtime generated) Commandline passed to CSC.EXE CSCGuard.txt – Contains debug and detailed information of the intercept event and all the information gathered.
Evidence Files
Additional files collected in this folder are all the evidence files gathered by CSCGuard in order to help analysis:
- Parent Process Binary
- Compiled File Results (If passthru allowed)
- C# source files
- Resource files
Installation
- Compile the source and take the resulting CSCGuard.exe and CSCGuard.exe.config files or use the provided binaries.
- You will need to elevate your privileges to TrustedInstaller in order to change the .NET Framework folders – I suggest using the tools RunAsSystem and RunFromToken tools in order to easily accomplish this.
- IMPORTANT! Backup the original CSC.EXE and CSC.EXE.Config files stored in your \Windows\Microsoft.NET\Framework & Framework64 sub .NET version folders and rename them to CSCGuard.EXE and CSCGuard.Exe.config in their current folders (See Config section)
- Rename and move CSCGuard.exe and CSCGuard.exe.config to CSC.EXE and CSC.EXE.Config in the .NET Folders in order to replace and intercept CSC execution.
Usage
CSCGuard is meant to be used in the sandbox, analysis, or non-production environments. I simply have not tested enough conditions to guarantee it’s performance or security within real user environments, please use at your own risk. The code is ugly but its functional, being a hack done in a single day in order to analyze some malware.

By default, CSCGuard will prevent suspicious CSC execution (See MaxThreatLevel in Config). In order to analyze malware, set MaxThreatLevel to some ridiculous number like 999 in order to allow passthru to CSC.exe in order to collect files.
Author: @Laughing_Mantis
Source: https://github.com/glinares/