
In a recent revelation, researchers at Akamai have identified a new attack vector exploiting vulnerabilities in the Common Unix Printing System (CUPS). This discovery highlights how everyday devices, such as printers, can be harnessed to launch large-scale Distributed Denial-of-Service (DDoS) attacks, posing significant risks to organizations worldwide.
The attack leverages a chain of four vulnerabilities disclosed on September 26, 2024, by security researcher Evilsocket. These vulnerabilities, identified as CVE-2024-47176, CVE-2024-47076, CVE-2024-47175, and CVE-2024-47177, collectively allow for remote code execution (RCE) by manipulating Internet Printing Protocol (IPP) URLs. While the original focus was on RCE, Akamai’s team discovered the additional risk of DDoS amplification inherent in these flaws.
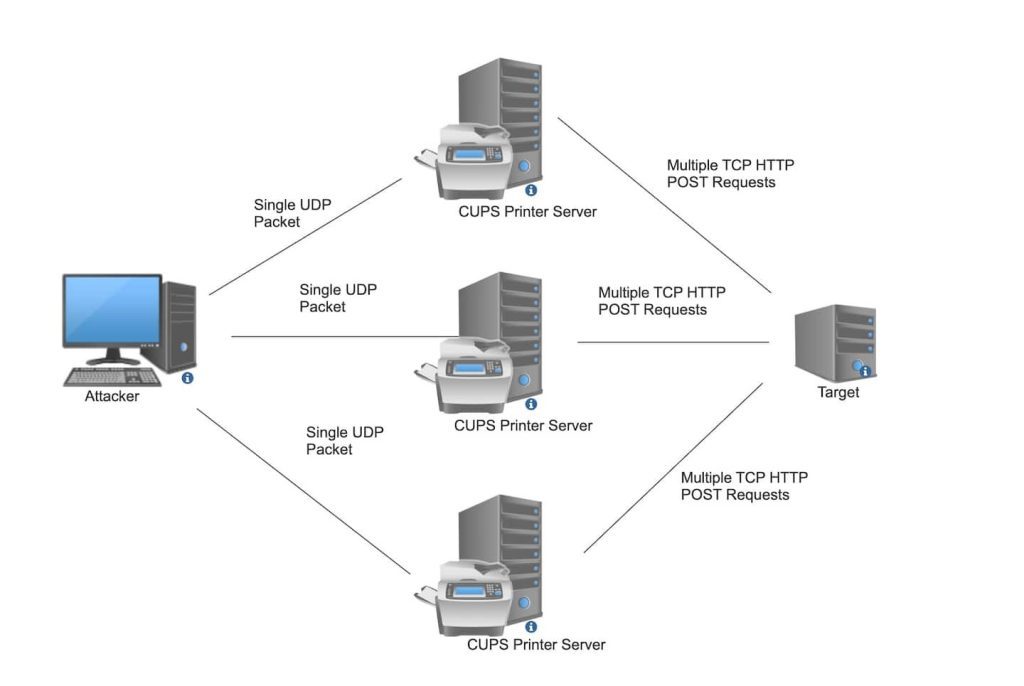
The alarming aspect of this new threat is the minimal effort required by attackers to initiate an assault. According to Akamai’s Security Intelligence and Response Team (SIRT), an attacker needs only to send a single, crafted packet to a vulnerable and internet-exposed CUPS service. This action triggers the compromised device to generate a larger volume of malicious traffic directed at a target system, effectively consuming network bandwidth and CPU resources of both the CUPS host and the victim.
Akamai’s research indicates that over 198,000 devices globally are susceptible to this exploit, with more than 58,000 of them readily accessible on the public internet and capable of being abused for DDoS attacks. Alarmingly, hundreds of these devices exhibit an “infinite loop” behavior, continuously sending requests and amplifying the potential impact on targeted networks.
“The limited resources required to initiate a successful attack highlights the danger,” the report states. “It would take an attacker mere seconds to co-opt every vulnerable CUPS service currently exposed on the internet and cost the attacker less than a single US cent on modern hyperscaler platforms.”
The attack is initiated when an attacker sends a specially crafted packet to a vulnerable CUPS server, specifying the address of a target system as a printer to be added. The CUPS service then attempts to fetch what it believes is an IPP attributes file from the target, resulting in unsolicited and amplified traffic being sent to the victim. This not only affects the target system but also burdens the CUPS server with excessive network and processing demands.
A significant contributing factor to the vulnerability is the widespread use of outdated CUPS versions. Many identified machines are running software released as far back as 2007. Organizations often overlook updating such systems, leaving them exposed to exploitation. Attackers can capitalize on these outdated devices, potentially building botnets for various malicious activities, including further DDoS attacks.
The amplification effect of this exploit is considerable. In testing scenarios, a minimal input from the attacker could result in an amplification factor of up to 600 times, generating substantial traffic aimed at the target. In worst-case scenarios, the amplification factor, while lower, results in significantly higher bandwidth consumption, placing immense strain on network resources.
If all vulnerable CUPS hosts were leveraged simultaneously, the attack could unleash a flood of traffic measuring between 1 GB to 6 GB from a single packet, overwhelming the target’s infrastructure. Moreover, the necessity for the target to handle millions of TCP connections and HTTP requests could lead to service outages and significant operational disruptions.
Akamai recommends several mitigation strategies to combat this threat:
- Update or Remove CUPS: Organizations should assess the necessity of CUPS in their environments. If printing services are essential, updating to the latest version of CUPS is crucial. Otherwise, removing CUPS can eliminate the vulnerability.
- Firewall Configuration: Blocking service ports (UDP/631) from external access can prevent attackers from reaching vulnerable services.
- DDoS Mitigation Solutions: Employing network-level DDoS protection and web application firewalls (WAFs) can help detect and filter malicious traffic patterns associated with this exploit.
- Monitoring and Alerts: Setting up alerts for unusual traffic patterns or spikes can provide early warning signs of an ongoing attack.
The emergence of this DDoS threat via CUPS services underscores the importance of maintaining up-to-date systems and promptly addressing known vulnerabilities. Cyber attackers are increasingly adept at exploiting overlooked or underestimated weaknesses in network infrastructures.
“Threat actors are often quick to leverage newly reported vulnerabilities, with many new releases being exploited within just seven days after initial disclosure,” Akamai warns. “Patching takes time, and hackers are eager to take advantage of that vulnerable transition period.”
Related Posts:
- Critical CUPS Vulnerabilities Expose Linux and Other Systems to Remote Attacks
- Attacker use DDoS attack to hit three major Dutch banks
- 20,000+ Ubiquiti Devices Exposed: Amplification Attacks & Data Leaks