The Korean Computer Emergency Response Team(KR-CERT) is currently issuing a warning about the new 0-day vulnerability. According to the published security alert, this vulnerability affects Flash Player version 28.0.0.137 (current) and earlier.
KR-CERT said: “An attacker can persuade users to open Microsoft Office documents, web pages, spam e-mails, etc. that contain Flash files that distribute the malicious [Flash] code.”
Simon Choi, a security researcher at South Korean security firm Hauri Inc., said North Korea’s hacker activists have successfully exploited the 0day vulnerability and that they actually started using it in mid-November 2017. Choi said the attackers are attacking South Korean users.
Flash 0day vulnerability that made by North Korea used from mid-November 2017. They attacked South Koreans who mainly do research on North Korea. (no patch yet) pic.twitter.com/bbjg1CKmHh
— IssueMakersLab (@issuemakerslab) February 1, 2018
KR-CERT recommends that users should disable or uninstall Adobe Flash Player until Adobe releases a patch.
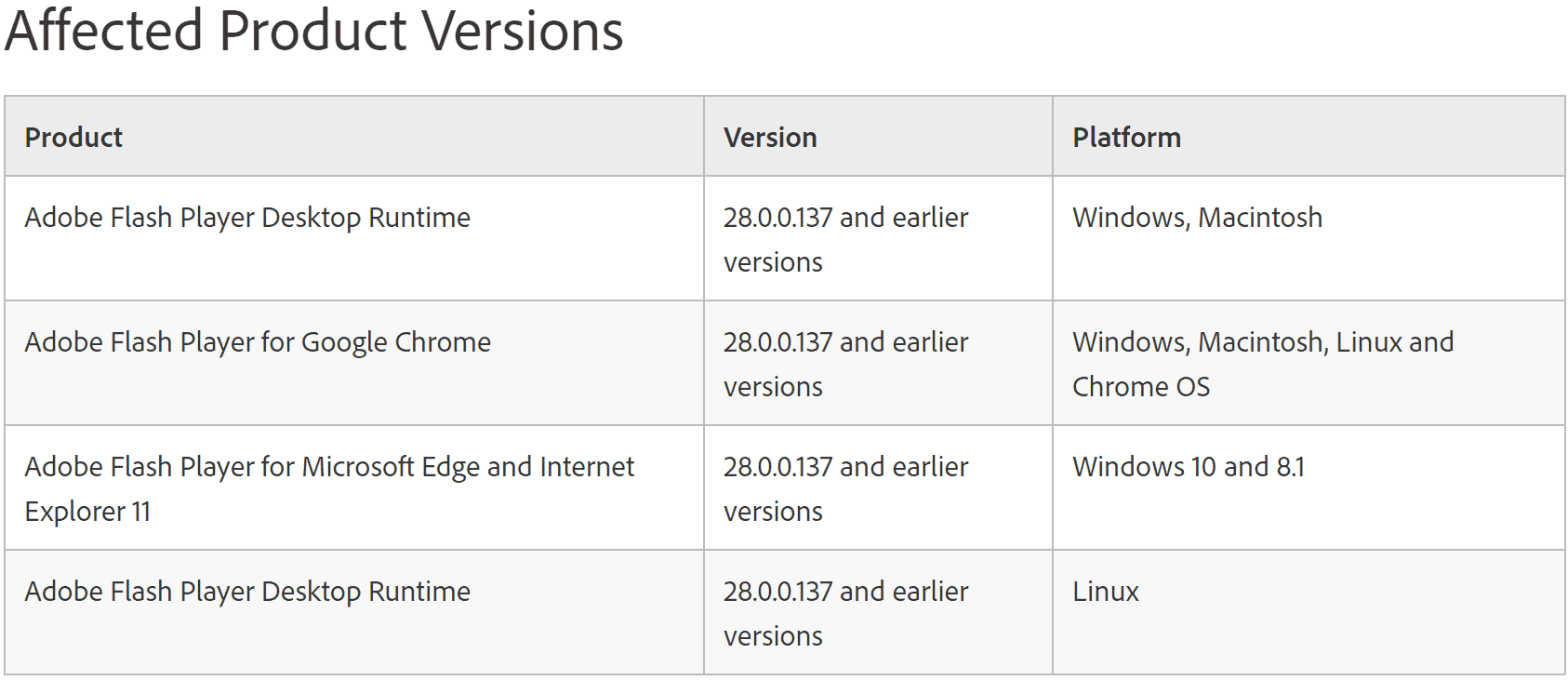
A critical vulnerability (CVE-2018-4878) exists in Adobe Flash Player 28.0.0.137 and earlier versions. Successful exploitation could potentially allow an attacker to take control of the affected system.
Adobe is aware of a report that an exploit for CVE-2018-4878 exists in the wild, and is being used in limited, targeted attacks against Windows users. These attacks leverage Office documents with embedded malicious Flash content distributed via email.
Adobe will address this vulnerability in a release planned for the week of February 5.