Palo Alto Networks this week informed customers that it has patched a vulnerability (CVE-2022-0024) in Palo Alto Networks PAN-OS, the software that runs on the company’s next-generation firewalls.
PAN‑OS is the software that runs all Palo Alto Networks next-generation firewalls. By leveraging the key technologies that are built into PAN‑OS natively—App‑ID, Content‑ID, Device-ID, and User‑ID—you can have complete visibility and control of the applications in use across all users and devices in all locations all the time. And, because inline ML and the application and threat signatures automatically reprogram your firewall with the latest intelligence, you can be assured that all traffic you allow is free of known and unknown threats.
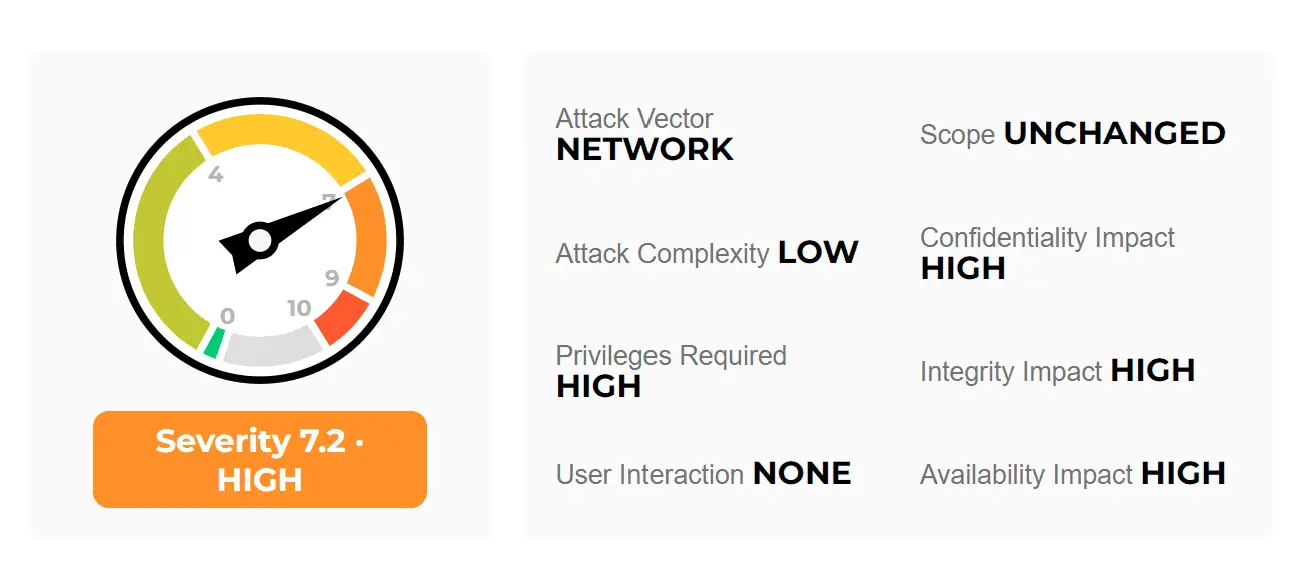
The issue was classified by the company as “high” severity that can be exploited by an authenticated attacker to execute arbitrary code on affected firewalls. CVE-2022-0024 has a CVSS score of 7.2, and impacts PAN-OS but does not impact Panorama appliances or Prisma Access customers.

The flaw “enables an authenticated network-based PAN-OS administrator to upload a specifically created configuration that disrupts system processes and potentially execute arbitrary code with root privileges when the configuration is committed on both hardware and virtual firewalls.”
The company “is not aware of any malicious exploitation of this issue.”
Affected version
- PAN-OS 8.1 versions earlier than PAN-OS 8.1.23;
- PAN-OS 9.0 versions earlier than PAN-OS 9.0.16;
- PAN-OS 9.1 versions earlier than PAN-OS 9.1.13;
- PAN-OS 10.0 versions earlier than PAN-OS 10.0.10;
- PAN-OS 10.1 versions earlier than PAN-OS 10.1.5.
Palo Alto Networks has been patched with the release of PAN-OS 8.1.23, PAN-OS 9.0.16, PAN-OS 9.1.13, PAN-OS 10.0.10, PAN-OS 10.1.5, and all later PAN-OS versions.