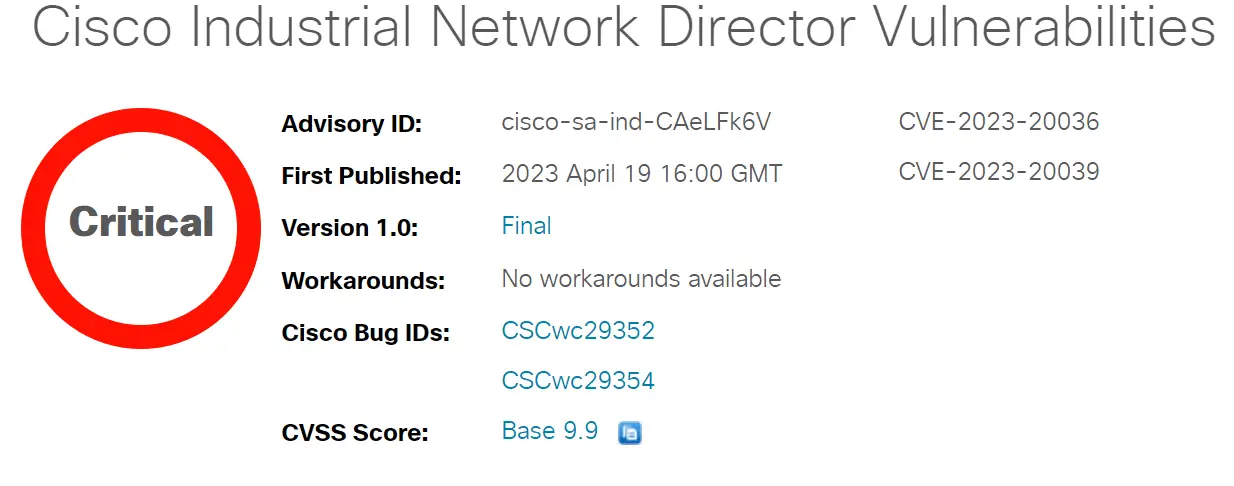
Cisco Industrial Network Director (IND) is a crucial tool for managing industrial networks, especially in environments that demand high-security standards. Recently, two vulnerabilities have been identified in IND, with the potential for authenticated attackers to inject arbitrary operating system commands or gain access to sensitive data. Cisco has released software updates to address these vulnerabilities, and it is essential for organizations to be aware of the risks and take appropriate action.

- CVE-2023-20036: Command Injection Vulnerability
With a CVSS score of 9.9, the Cisco Industrial Network Director Command Injection Vulnerability is the more severe of the two. This vulnerability is present in the web UI of Cisco IND and allows an authenticated, remote attacker to execute arbitrary commands with administrative privileges on the underlying operating system of an affected device.
The CVE-2023-20036 vulnerability stems from improper input validation when uploading a Device Pack. Attackers can exploit it by altering the request sent during the upload process. A successful exploit can enable the attacker to execute arbitrary commands as NT AUTHORITY\SYSTEM on the affected device’s operating system.
- CVE-2023-20039: File Permissions Vulnerability
The second vulnerability, with a CVSS score of 5.5, relates to file permissions in Cisco IND. An authenticated, local attacker can exploit this vulnerability to read application data due to insufficient default file permissions applied to the application data directory.
By accessing files in the application data directory, a successful exploit could allow an attacker to view sensitive information, potentially leading to further security breaches.
Mitigation and Remediation
Cisco has released software updates that address both of these vulnerabilities, and organizations are urged to update their systems to the first fixed release, IND version 1.11.3, or later. There are no known workarounds for these vulnerabilities, making it crucial for users to apply the software updates as soon as possible.
At the time of writing, Cisco’s Product Security Incident Response Team (PSIRT) is not aware of any public announcements or malicious use of the vulnerabilities described in this advisory.