Recently, concerning security vulnerabilities have surfaced in Cisco’s Expressway Series and TelePresence Video Communication Server (VCS), highlighting the necessity for constant vigilance and proactive response in the world of tech security.
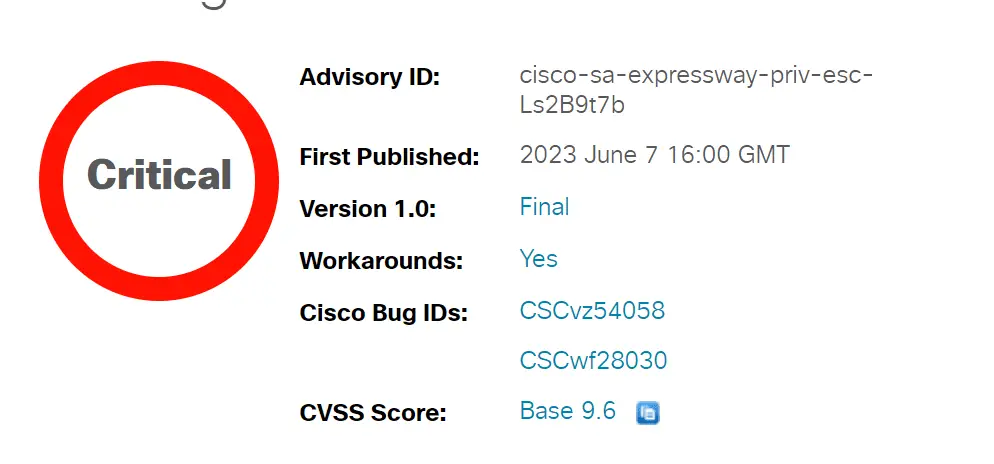
Cisco has reported two significant security vulnerabilities that could allow an authenticated attacker, possessing Administrator-level read-only credentials, to escalate their privileges to Administrator with read-write credentials, a loophole that could potentially lead to disastrous outcomes. The vulnerabilities in question, identified as CVE-2023-20105 and CVE-2023-20192, scored a worrying 9.6 and 8.4 on the CVSS (Common Vulnerability Scoring System) respectively, indicating the severity of the threat posed.

The CVE-2023-20105 vulnerability resides within the change password functionality of the Cisco Expressway Series and Cisco TelePresence VCS. This breach in the system’s defenses is rooted in the improper handling of password change requests, potentially allowing a remote attacker to alter the passwords of any user on the system by sending a crafted request via the web-based management interface. An attacker could exploit this vulnerability to modify the password of an administrative read-write user, thereby impersonating them, a security breach fixed in version 14.2.1.
CVE-2023-20192, the second vulnerability, is embedded within the privilege management functionality. This flaw enables an authenticated, local attacker to gain read-write privileges by exploiting incorrect implementation of user role permissions. Upon authentication as a read-only CLI (Command Line Interface) administrator, the attacker could exploit this vulnerability to execute commands normally exclusive to administrators with read-write capabilities. This would give them access to modify system configuration parameters, significantly amplifying the gravity of the situation. This issue, which primarily affects those who have granted CLI access to a read-only administrator, was rectified in version 14.3.0.
In response to these escalating threats, Cisco has swiftly released software updates that specifically address these vulnerabilities. As an additional measure to circumvent the CVE-2023-20192 vulnerability, organizations can disable CLI access for read-only users as a workaround, further strengthening their cyber defense.