In the vast interconnected cosmos of digital systems, security stands as the bedrock of trust. Cisco, a revered name in the tech industry, has long been synonymous with reliable and robust networking solutions. Yet, even the mightiest fortresses have their weak points, as recently demonstrated by a vulnerability discovered in Cisco’s BroadWorks platforms.
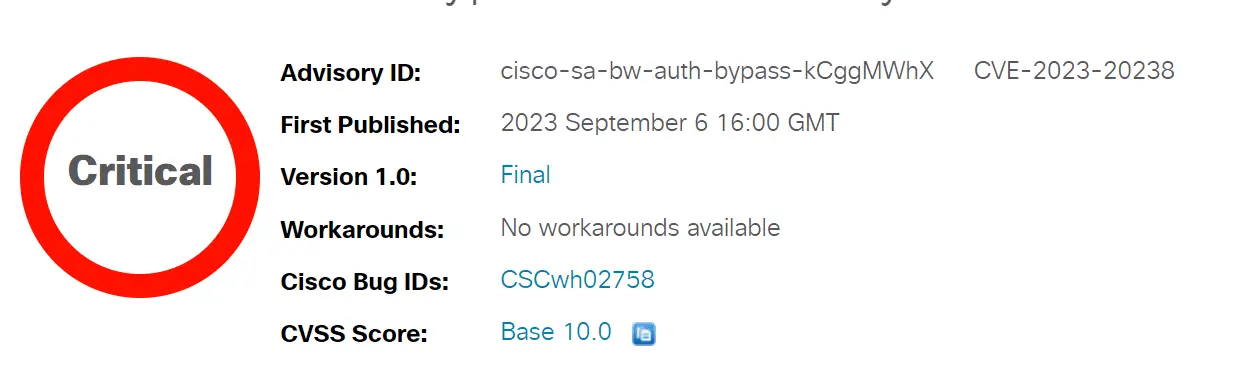
The vulnerability, known as CVE-2023-20238, is an authentication bypass flaw, with a maximum CVSS score of 10—signifying its critical nature. The platforms in the limelight are the Cisco BroadWorks Application Delivery Platform and the Cisco BroadWorks Xtended Services Platform. The flaw lies in their single sign-on (SSO) implementation, acting as a potential gateway for unauthorized users.

How does this happen? The root of this flaw traces back to the method BroadWorks platforms utilize to validate SSO tokens. In simpler terms, the gatekeeper of these platforms can be tricked with forged credentials.
The successful exploitation of this vulnerability paves the way for multiple avenues of mischief. Imagine a cyber marauder, armed with nothing more than a valid user ID for the Cisco BroadWorks system, gaining unhindered access. The damage could range from toll fraud to executing high-privilege commands, dependent on the nature of the forged account.
The implications are staggering. If the impersonated account holds administrator privileges, the attacker would be in the driving seat, potentially viewing confidential data, tweaking customer settings, or even altering other users’ configurations.
The reach of CVE-2023-20238 is not limited. The vulnerability rears its head in instances where BroadWorks platforms run a vulnerable Cisco BroadWorks release and have specific applications enabled. The list is
- AuthenticationService
- BWCallCenter
- BWReceptionist
- CustomMediaFilesRetrieval
- ModeratorClientApp
- PublicECLQuery
- PublicReporting
- UCAPI
- Xsi-Actions
- Xsi-Events
- Xsi-MMTel
- Xsi-VTR
While the situation might seem dire, there’s a beacon of hope. As of now, the Cisco PSIRT has found no evidence of CVE-2023-20238’s exploitation in the wild. Additionally, in line with its commitment to user security, Cisco has already taken action by releasing software patches to neutralize this threat.
| Cisco BroadWorks Application Delivery Platform and BroadWorks Xtended Services Platform Release | First Fixed Release |
|---|---|
| 22.0 and earlier | Migrate to a fixed release. |
| 23.0 | AP.platform.23.0.1075.ap385341 |
| Release Independent (RI) | 2023.06_1.333 and 2023.07_1.332 |
Unfortunately, there are no workarounds that address this vulnerability.