When it comes to building an optimized, highly available, and secure network infrastructure across hybrid and multi-cloud environments, VMware’s Aria Operations for Networks stands as a beacon in the industry. Its capabilities extend beyond the standard fare, providing network visibility and analytics to bolster micro-segmentation security, minimizing risk during application migration, and facilitating confident management and scaling of VMware NSX, VMware SD-WAN, and Kubernetes deployments.
However, cybersecurity is a dynamic field. No product, however well-designed, is entirely immune to vulnerabilities. VMware recently faced this reality when multiple vulnerabilities were privately reported in Aria Operations for Networks. Thankfully, VMware has already released patches to address these security concerns.

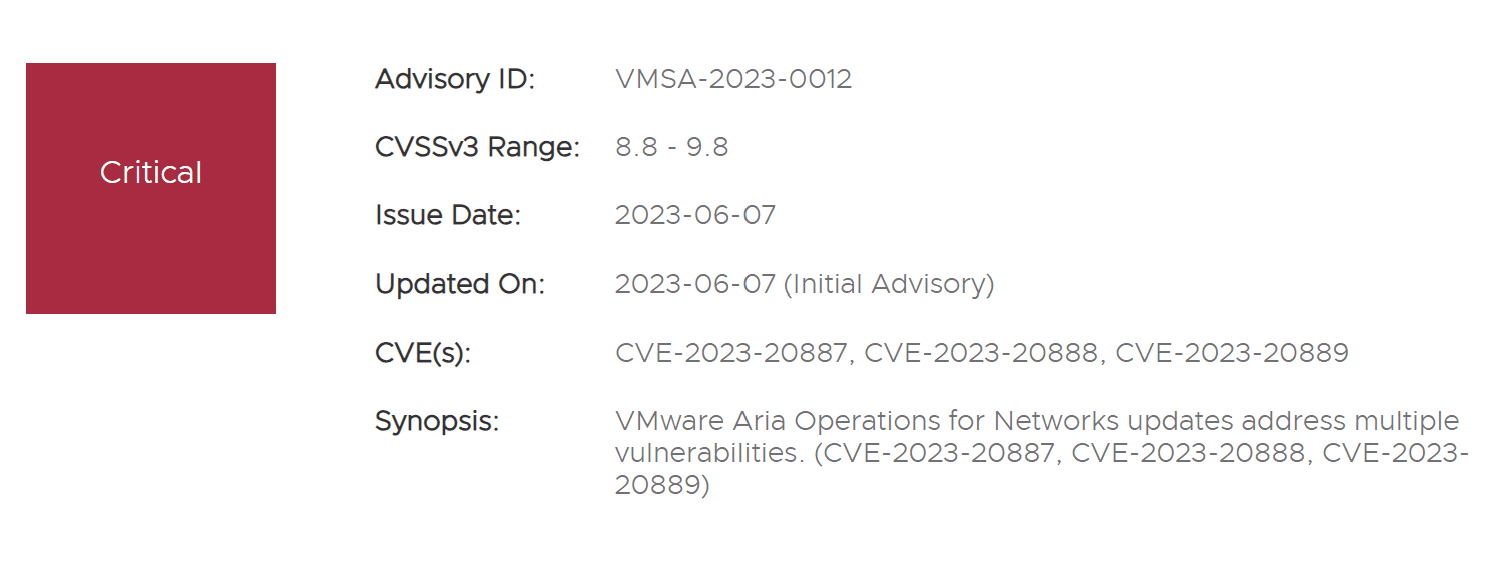
1. CVE-2023-20887: Command Injection Vulnerability
With a CVSS score of 9.8, the most severe of these vulnerabilities involve the potential for a malicious actor to perform a command injection attack. In a nutshell, the CVE-2023-20887 vulnerability, if exploited, could result in remote code execution—a scenario that spells serious trouble for network security.
Command injection is a form of attack in which the attacker can execute arbitrary commands on the host operating system via a vulnerable application. It is a prevalent class of vulnerabilities often occurring due to inadequate input/output data validation.
2. CVE-2023-20888: Authenticated Deserialization Vulnerability
Another significant threat, with a CVSS score of 9.1, involves an authenticated deserialization vulnerability. In this context, a malicious actor with network access and valid ‘member’ role credentials could execute a deserialization attack, once again leading to remote code execution.
Deserialization vulnerabilities occur when an application deserializes data without properly validating or sanitizing the data first. An attacker can exploit this vulnerability to run arbitrary code, control program flow, or crash the application.
3. CVE-2023-20889: Information Disclosure Vulnerability
The third vulnerability (CVSS score of 8.8) pertains to potential information disclosure through another possible command injection attack. If successfully exploited, the attacker could gain access to sensitive information, which could have a wide range of consequences depending on the nature of the disclosed information.
Information disclosure vulnerabilities can be especially damaging because they can expose sensitive user or system data that can then be used in further attacks, leading to a significant breach of privacy and security.
Mitigating the Threats
Following the identification of these vulnerabilities, VMware acted swiftly to mitigate them. The company recommends applying patches for Aria Operations for Networks versions 6.2 through 6.10. Timely patching ensures the secure operation of your network, reducing the likelihood of data breaches or cyber-attacks.