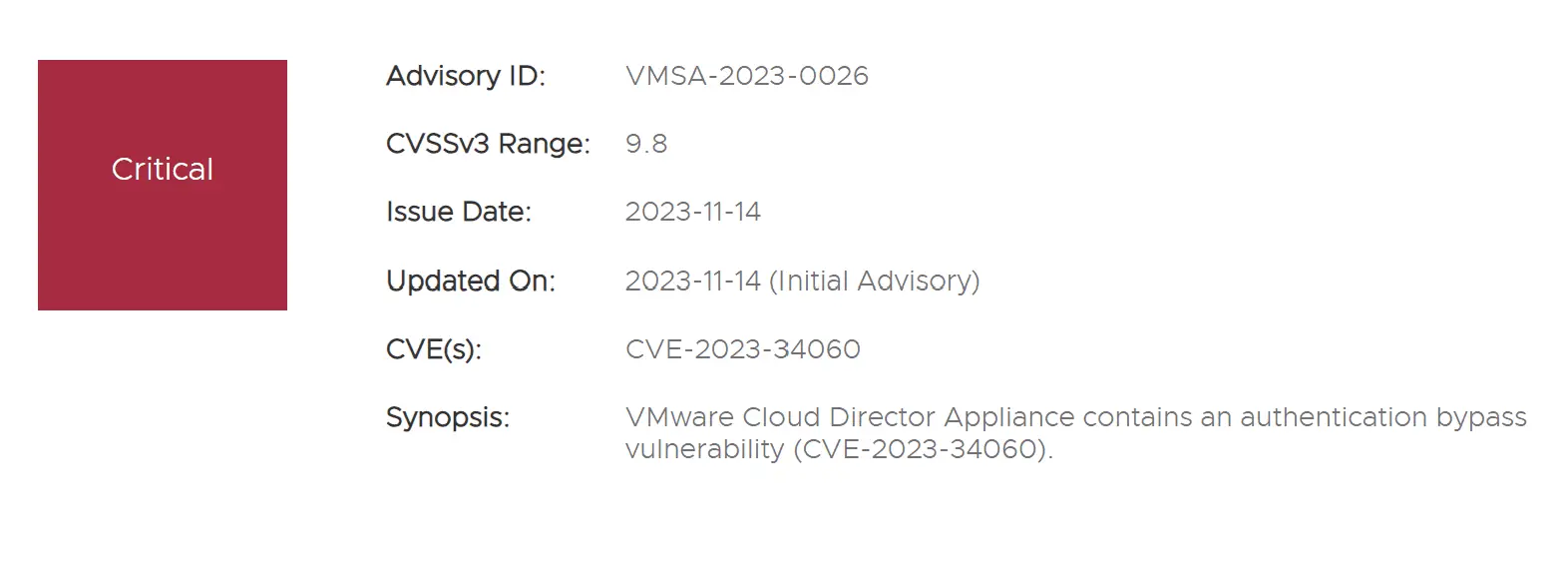
VMware has recently disclosed a critical authentication bypass vulnerability affecting VMware Cloud Director Appliance deployments. This vulnerability tracked as CVE-2023-34060 and assigned a CVSS score of 9.8 (considered critical), allows malicious actors with network access to bypass login restrictions when authenticating on port 22 (ssh) or port 5480 (appliance management console) on upgraded versions of VMware Cloud Director Appliance 10.5. This vulnerability does not affect new installations of VCD Appliance 10.5, Linux deployments, or other appliances, nor does it affect port 443 (VCD provider and tenant login).

This authentication bypass vulnerability arises from a misconfiguration within the appliance’s login process. When an upgraded version of VMware Cloud Director Appliance 10.5 is running, an attacker with network access can exploit this misconfiguration to gain unauthorized access to the appliance. This access could potentially compromise sensitive data, disrupt cloud operations, or even allow for the deployment of malware.
While VMware is currently working on a definitive patch for this vulnerability, they have provided a temporary workaround to mitigate the risk of exploitation. The workaround involves downloading a custom script from a knowledgebase article and running it on affected cells. This script will modify the configuration of the appliance’s login process to prevent the authentication bypass vulnerability from being exploited.
Given the critical nature of the CVE-2023-34060 vulnerability, it is strongly recommended that all users of VMware Cloud Director Appliance 10.5 apply the temporary workaround as soon as possible. Additionally, users should closely monitor VMware’s security updates page for the release of a permanent patch and apply it promptly once available.