CVE-2023-42465: SUDO Affected by Stack/Register Flaw, OpenSSH, OpenSSL, and MySQL are Vulnerable
The digital realm is no stranger to ingenious exploits, and the latest breakthrough in cybersecurity research is no exception. Researchers have unveiled “Mayhem,” a formidable attack technique that targets the very heart of computing systems: CPU internals and stack variables. This attack method represents a significant evolution in cyber threats, as it successfully manipulates a computer’s memory to corrupt stack and register variables.
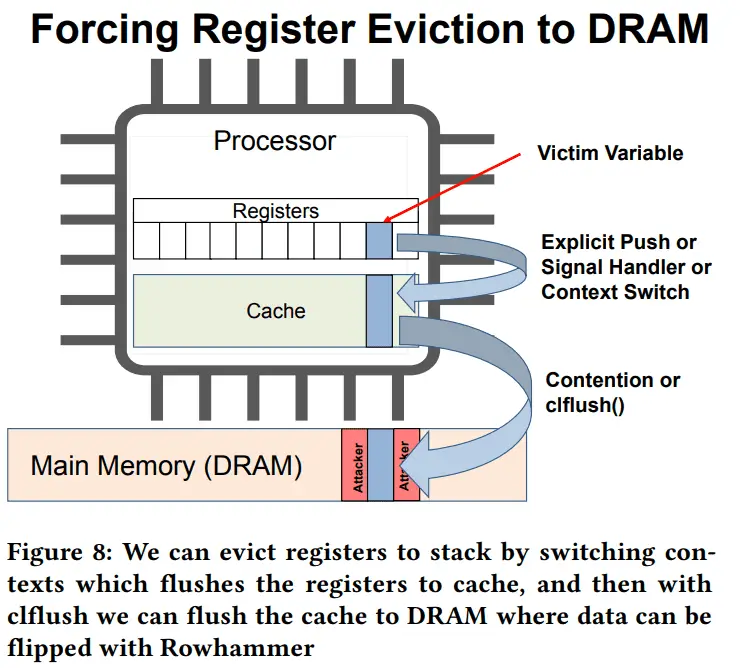
“Mayhem” leverages the notorious Rowhammer effect, a phenomenon where rapid access to a DRAM row causes bit flips in adjacent rows. This ingenious attack manipulates these bit flips to corrupt stack variables and even register values within a process. This manipulation is achieved by targeting register values stored in the process’s stack, which, when flushed out to memory, become susceptible to Rowhammer attacks. Upon reloading, these corrupted values wreak havoc, undermining the integrity of the process.

Image Credit: Vernam Lab
Mayhem’s methodology is both intricate and alarming. It exploits the Rowhammer effect, where repeated access to a DRAM row leads to bit flips in adjacent rows, to inject faults into a system’s critical data areas. This technique can bypass security protocols, potentially leading to unauthorized access or control over sensitive systems and data.
The researchers demonstrated Mayhem’s capabilities through several high-impact scenarios, including bypassing SUDO and SSH authentication and targeting OpenSSL security checks stored in the stack. This new approach to exploiting Rowhammer extends the attack surface far beyond previously known vulnerabilities, raising critical concerns about the security of current systems and the need for more robust protection mechanisms.
“The idea is that any bit can be flipped in auth, and it will result in a mis-authentication. We prove this is a potential vulnerability in OpenSSH, OpenSSL, MySQL, and SUDO. To mitigate this, it is important to have tight logic such that a single-bit flip will not result in unintended execution,” researchers wrote. Also, the exploit code will be available here.
Researchers issued CVE-2023-42465 for SUDO for this vulnerability. This flaw classified as critical has been found in sudo up to 1.9.14. Engineer Todd C. Miller has submitted a commit to migrating the CVE-2023-42465 bug in September.
Update on December 25
The OpenSSH project confirmed that this attack also affected OpenSSH. Tracked as CVE-2023-51767, OpenSSH through 9.6, when common types of DRAM are used, might allow row hammer attacks (for authentication bypass) because the integer value of authenticated in mm_answer_authpassword does not resist flips of a single bit.





