Image: Alter Solutions
Security researcher Yann Gascuel (Alter Solutions) has detailed a critical privilege escalation vulnerability (CVE-2023-42931) affecting the following macOS versions:
- macOS Monterey prior to 12.7.2
- macOS Ventura prior to 13.6.3
- macOS Sonoma prior to 14.2
The vulnerability granted unprivileged users, including those with guest access, the ability to escalate permissions and gain full root control over the system.
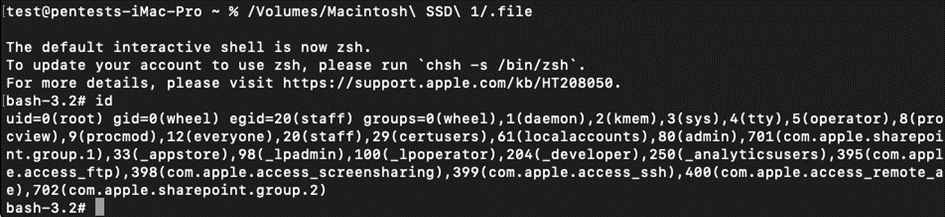
The heart of CVE-2023-42931 lies in the exploitation of the “diskutil” command line utility, which permits local users, including those with guest access, to mount filesystems with specific options that could lead to a privilege escalation. Notably, this vulnerability allows for an attack vector from any user level in macOS Ventura and earlier versions, although Sonoma users not in the “admin” group are prompted for an admin password, somewhat mitigating the risk for that OS version.
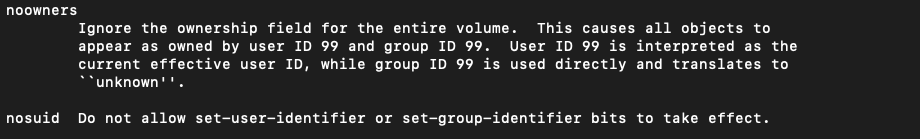
GASCUEL’s research uncovered that by leveraging the -mountOptions argument of diskutil to mount a filesystem with the “noowners” flag, an attacker could modify a root-owned file into any arbitrary binary and add the setuid bit to it, thereby facilitating a privilege escalation when remounted in “owners” mode. This process, while theoretically straightforward, was hampered by macOS’s modern disk/filesystem hierarchy and the protective measures of System Integrity Protection (SIP), which prevents modifications of sensitive system files at the kernel level.
Despite these obstacles, GASCUEL identified a viable exploit path through a “.file” placeholder file in the root filesystem, which met all the criteria for the exploit to succeed:
- Owned by root when mounted in “owners” mode;
- Considered owned by myself when mounted in “noowners” mode;
- Not protected by SIP.
Following this discovery, GASCUEL outlined the exploit process, which involves preparing a setuid shell payload, modifying the permissions of the “.file” to make it writable, and then executing the payload to gain root access.

In response to GASCUEL’s findings, Apple has issued a patch that essentially ignores the “noowners” mount option for internal storage mounted with diskutil, even when executed with root privileges via sudo. This fix is crucial in mitigating the vulnerability and protecting macOS users from potential exploitation.
Apple has addressed this vulnerability in its latest security updates. Affected macOS users should patch their systems as soon as possible.