CVE-2023-50358: A zero-day vulnerability affecting QNAP NAS devices
A severe zero-day vulnerability (CVE-2023-50358) has been discovered in QNAP Network Attached Storage (NAS) devices. This flaw allows attackers to execute commands remotely, potentially taking full control of vulnerable systems. Threat actors are already actively exploiting this vulnerability in the wild.
Unit 42 researchers detected suspicious attack traffic targeting QNAP devices via their Advanced Threat Prevention platform on Nov. 7, 2023. Subsequently, their analysis uncovered a new vulnerability related to the traffic (though not directly exploited).
The flaw assigned the identifier CVE-2023-50358, was an OS command injection vulnerability—a type of exploit that could allow attackers to execute arbitrary commands over a network. With low attack complexity and the potential for critical impact, this vulnerability is a siren call for threat actors. The prospect of remotely executing code on a device without requiring complex maneuvers makes it an irresistible target for those with malicious intent. This elevates the urgency of protecting IoT devices, transforming it from a routine security task to an imperative mission.
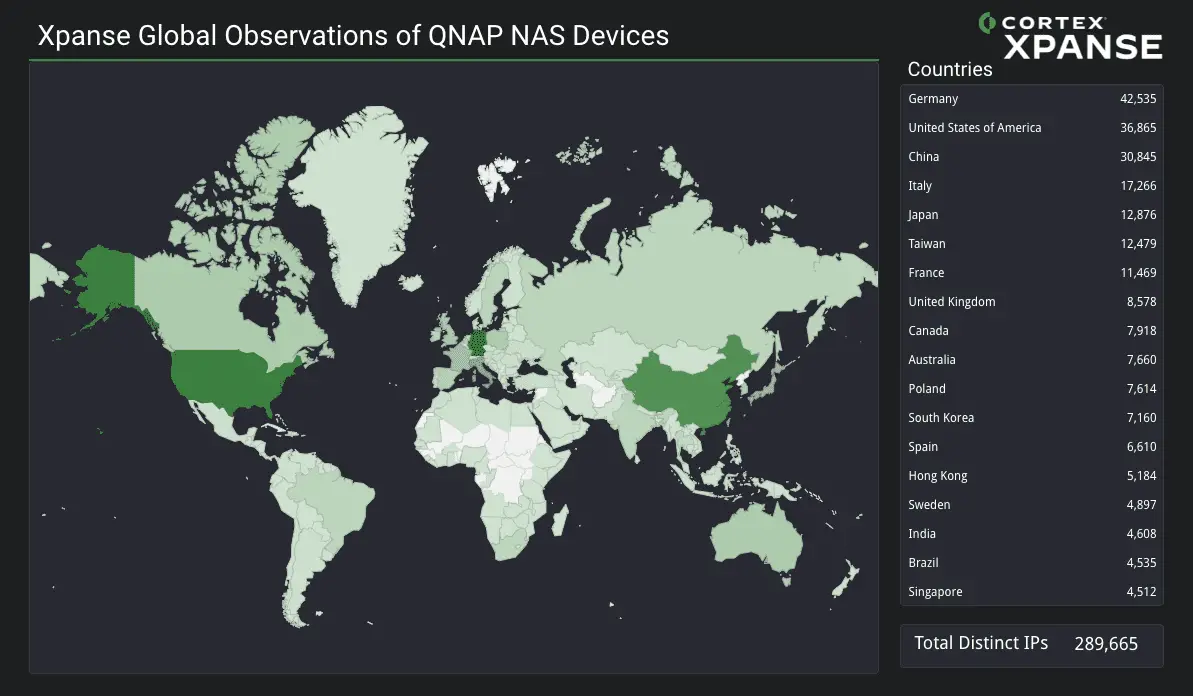
Researchers detected vulnerable devices from 289,665 separate IP addresses.

Global heatmap and list showing the countries most affected by this vulnerability | Image: Unit 42
Recognizing the gravity of the situation, QNAP, with acknowledgment to Palo Alto Networks, swiftly issued a security advisory. QNAP’s recommendation was clear and straightforward: update to the latest version of QTS or QuTScloud hero, specifically QTS 5.1.5 or QuTS hero h5.1.5. This recommendation wasn’t just a precaution; it was a necessary step to fortify defenses against the looming threat.
In addition, QNAP provided a simple yet effective self-test procedure. By accessing a specific URL on their device, users could quickly determine their vulnerability status.
- Test the following URL in your browser:
- https://<NAS IP address>:<NAS system port>/cgi-bin/quick/quick.cgi
- If you get the following response (HTTP 404 error), your system is not vulnerable:
- “Page not found or the web server is currently unavailable. Please contact the website administrator for help.”
- If you get an empty page (HTTP 200), continue to the next step.
- Update your operating system to one of the following versions or later:
- QTS 5.0.0.1986 build 20220324 or later
- QTS 4.5.4.2012 build 20220419 or later
- QuTS h5.0.0.1986 build 20220324 or later
- QuTS h4.5.4.1991 build 20220330 or later
- Test the above URL again in your browser.
- If you get the following response (HTTP 404 error), your system is now free from the vulnerability:
- “Page not found or the web server is currently unavailable. Please contact the website administrator for help.”
- If you get an empty page (HTTP 200), please contact QNAP technical support for assistance.





