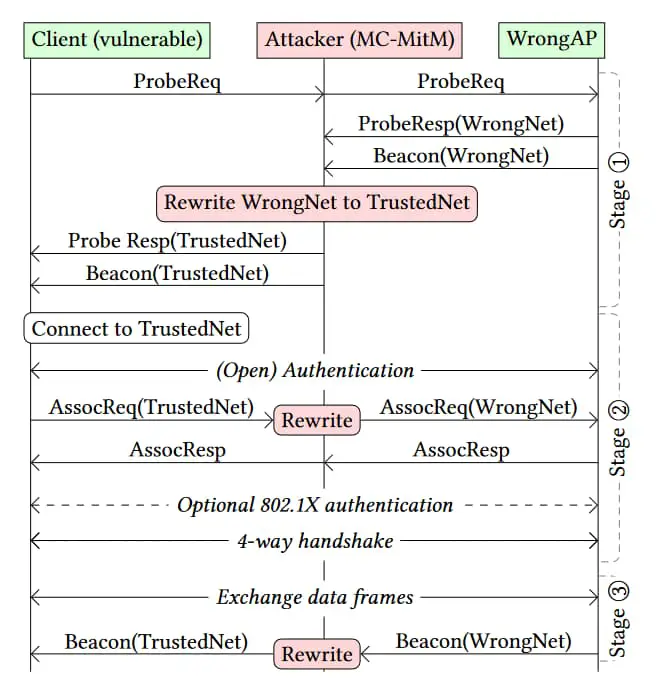
Diagram illustrating details of the SSID Confusion Attack. | Image: Top10vpn
A recently discovered vulnerability in the WiFi standard has revealed significant security risks, allowing attackers to mislead users into connecting to insecure networks. This vulnerability, identified as CVE-2023-52424 and dubbed the SSID Confusion Attack, was uncovered by security researcher Mathy Vanhoef in collaboration with Top10VPN. The findings are set to be presented at the WiSec ’24 conference in Seoul.
The SSID Confusion Attack exploits a design flaw in the IEEE 802.11 WiFi standard. This flaw allows attackers to trick victims into connecting to a network with a spoofed SSID (network name), leading to potential traffic interception and manipulation. The attack is particularly concerning as it affects all WiFi clients across all operating systems.

The attack can manipulate the auto-disconnect feature in certain VPN clients, causing the VPN connection to disable when the device connects to a predefined “trusted” network. This leaves the victim’s traffic vulnerable to interception.
The root cause lies in the IEEE 802.11 standard, which does not mandate SSID authentication during network discovery. This oversight allows attackers to perform a man-in-the-middle (MitM) attack, spoofing the SSID of a trusted network and downgrading the victim’s connection to a less secure one.
Various WiFi networks and authentication protocols are vulnerable to the SSID Confusion attack:
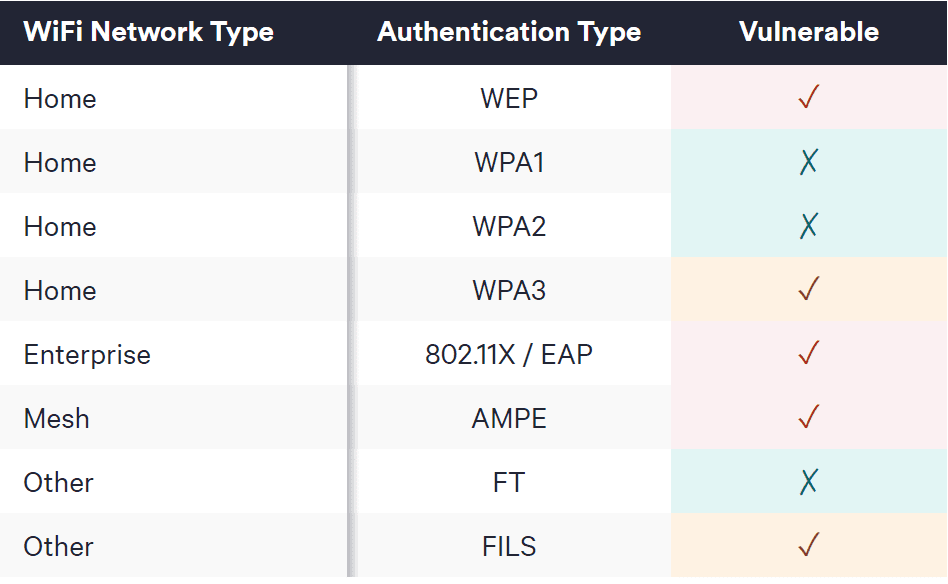
- Home Networks: Particularly WPA3 networks, due to the optional mode where the SSID is not used in the SAE handshake.
- Enterprise Networks: Vulnerable due to the use of 802.1X and EAP protocols, which do not use the SSID to derive the Pairwise Master Key (PMK).
- Mesh Networks: Vulnerable under the same conditions as WPA3 networks.
- Other Protocols: FILS is vulnerable when using a shared key from an EAP handshake, while FT is not vulnerable.
For an SSID Confusion attack to succeed, several conditions must be met:
- The victim attempts to connect to a trusted network.
- An attacker is within range to perform a MitM attack.
- A second network with the same credentials as the trusted network is available.
Once these conditions are met, the attacker can intercept and manipulate the victim’s traffic. The CVE-2023-52424 vulnerability poses significant risks, especially in environments where credential reuse is common, such as educational institutions using eduroam.
Researchers have identified at least six universities where staff and students are particularly vulnerable due to credential reuse across different networks. Enterprise networks are also at risk, as they often use authentication methods that do not rely on the SSID for security.
To mitigate the risks posed by the SSID Confusion attack, several strategies can be employed:
- WiFi Standard Improvements:
- Mandate SSID authentication during the 4-way handshake.
- Include the SSID in key derivation or as additional authenticated data.
- WiFi Client Enhancements:
- Improve beacon protection by authenticating beacons before connection.
- Store and verify reference beacons during the handshake.
- Avoid Credential Reuse:
- Use distinct credentials for different SSIDs, particularly in enterprise and home networks.
- Proper VPN Usage:
- Configure VPNs to remain active regardless of the network’s trust level to ensure continuous traffic protection.
For a detailed technical analysis and further insights, download the full report: SSID Confusion: Making Wi-Fi Clients Connect to the Wrong Network.