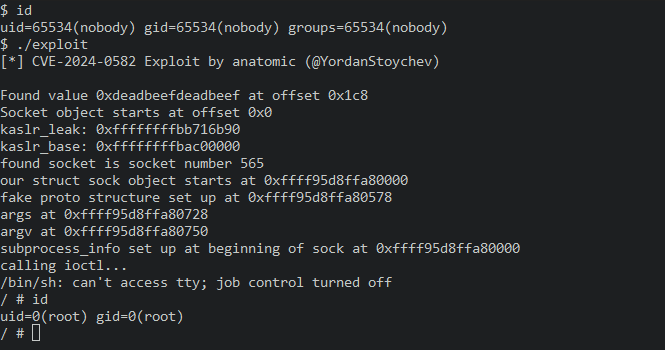
The technical details and proof-of-concept (PoC) exploit code has been released for a significant vulnerability, designated CVE-2024-0582 (CVSS 7.8) in the Linux kernel. The flaw, affecting versions 6.4 through 6.6, could allow attackers with local user access to compromise a system and gain full administrative control.

How the Exploit Works
- Memory Mismanagement: The core issue lies in how the kernel handles memory associated with a specific function (io_uring) used by applications. A lapse in tracking memory state can lead to a “use-after-free” situation.
- The Danger of ‘Use-After-Free’: When an application continues to access memory that has already been released by the kernel, it can lead to unpredictable behavior. Attackers can manipulate this to corrupt data or execute malicious code.
- Privilege Escalation: In this case, attackers with an existing foothold (even a low-privilege user account) could exploit the flaw to gain root-level access, effectively taking over the entire system.
Affected Systems
- Kernel Versions: Linux kernels from 6.4 up to (but not including) 6.7 are affected.
- Distributions: Distributions like Ubuntu 23.10 and some versions of Ubuntu 22.04 LTS initially shipped with vulnerable kernels.
Technical Analysis
The Linux kernel’s io_uring functionality, crucial for managing input/output operations, becomes a double-edged sword when a user registers a buffer ring with the IORING_REGISTER_PBUF_RING operation, maps it with mmap(), and then proceeds to free it. This sequence of actions uncovers a chink in the kernel’s armor, allowing a local user to crash the system or, more alarmingly, escalate their privileges.
The trigger for this vulnerability is an application’s registration of a provided buffer ring with the IOU_PBUF_RING_MMAP flag. In doing so, the kernel takes on the responsibility of allocating memory for the buffer ring, a task typically managed by the application. The application must then use mmap() to create a virtual mapping to access the buffers. The crux of the vulnerability lies in the subsequent step: if an application unregisters the provided buffer ring using the IORING_UNREGISTER_PBUF_RING opcode, the kernel frees this memory, inadvertently opening the door to misuse.
Without a mechanism to verify if the memory has been previously unmapped in userspace, the application retains a valid memory mapping to pages that have been freed and potentially reallocated by the kernel for other uses. Any attempt to read or write to these pages post-reallocation precipitates a use-after-free scenario, placing the integrity and security of the system in jeopardy.
Security researchers @foolisses and @YordanStoychev have provided a detailed analysis of the CVE-2024-0582 vulnerability, including a proof-of-concept (PoC) exploit.
What You Should Do
- Update Immediately: If you’re running an affected Linux version, apply available security patches as soon as possible.
- Check Your Distribution: Visit your Linux distribution’s website [Ubuntu, Debian, SUSE] for specific advisories and update instructions.
- Limit User Accounts: Where possible, minimize the number of user accounts on your system, especially those with elevated privileges. This helps contain the potential impact should a breach occur.